The education sector proved to be a key target for threat actors in Q2 2024, particularly for ransomware groups. FOG ransomware was a significant threat to the sector this quarter, with clear seasonal cycles in incidents impacting educational institutions, possibly due to perceived reduction in IT staffing around the summer months or the belief that schools may be more likely to pay a ransom during peak periods.
Professional services stayed at the top spot as the most targeted industry, with other sectors, such as healthcare, seeing increases in comparison with the previous quarter.
Kroll’s findings for Q2 highlight a 7% increase in incidents related to unauthorized access. This included a case in which threat actors associated with the group known as SCATTERED SPIDER (KTA243) leveraged social engineering to create new accounts and probe access to cloud systems. This case, alongside significant attacks around the cloud service Snowflake during the second quarter, highlights threat actors’ increasing focus on the cloud as an entry point into networks, and the growing use of information-stealing malware.
Q2 2024 Threat Timeline
Sector Analysis: Professional Services Remains Top Target
Q2 2024 saw the professional services sector retain its place as the most targeted industry for over a year. Other sectors in the top five, such as manufacturing, health care and retail/restaurant, experienced increases from the previous quarter. Manufacturing underwent a small rise from the last quarter, aligning with insights in the recent Kroll report, The State of Cyber Defense 2024: Manufacturing Cyber Resilience. In contrast, health care has seen a significant jump from Q1 to Q2, reflecting the concerning findings in the Kroll report, The State of Cyber Defense: Diagnosing Cyber Threats in Healthcare. While the professional services sector clearly needs to remain vigilant, trends show that other sectors have very good reason to strengthen their defenses too.
Most Targeted Industry by Sector Over the Past Three Quarters
Sector Spotlight: Education Sector a Key Focus for FOG Ransomware Group
Kroll saw an uptick in activity against the education sector in Q2 2024. Much of this began in June when Kroll observed a spike in higher education organizations experiencing FOG ransomware incidents. Looking at the education sector over time, Kroll has observed clear seasonal cycles, with attacks more likely to occur in Q2 and Q3. Threat actors may target the sector during these periods for myriad reasons: perceived reduction in IT staffing around the summer months, or the belief that schools may be more likely to pay a ransom during peak periods such as the end or beginning of a semester.
While ransomware is the most impactful threat targeting education, actors most frequently target the sector with business email compromise.
Incident Response Cases in the Education Sector Over the Past Five Quarters
Threat Actor Analysis: FOG-Descends on the Education Sector
In Q2 2024, Kroll observed an increase in cases in which FOG ransomware targeted higher education institutions. This ransomware variant was first publicly reported in May 2024, with a branded leak site published in July 2024. It gains access into networks via compromised credentials. Our review of the indicators of compromise (IOCs) and tactics, techniques and procedures across cases identified that there were likely two distinct actors involved in the cases observed at Kroll. It is likely that the ransomware group operates on the ransomware-as-a-service (RaaS) affiliate model and that at least one of the actors observed was an affiliate for other ransomware gangs such as AKIRA. However, while AKIRA publicly solicited affiliates on various cybercriminal forums, Kroll has not observed the FOG ransomware gang openly advertising its operation.
Q2 2024 Education Sector – Threat Incident Types
Threat Incident Types: Unauthorized Access Incidents Rise as Actors Target SaaS Applications
In Q2, Kroll observed a 7% increase in incidents related to unauthorized access. Unauthorized access involves actors gaining access to a particular network but are typically stopped before they can progress into a more impactful incident like ransomware or data theft. Unauthorized access cases frequently relate to cloud or Software-as-a-Service (SaaS) applications that actors target for access via valid accounts.
Most Popular Threat Incident Types Over the Past Three Quarters
In Q2, Kroll observed a case in which threat actors associated with the well-known collective SCATTERED SPIDER socially engineered a help desk employee to reset a domain admin password. Once the password was reset, actors gained access to the account and proceeded to collect information that would help them access new accounts. Although in this case, actors were identified in the system before they could achieve their objectives. In that time, they accessed multiple accounts and created new email and domain admin accounts. They also probed access to multiple cloud services used by the organization.
This case reflects recent reporting that the group is increasingly targeting SaaS and/or cloud applications. Coinciding with the significant attacks around the cloud service Snowflake during the quarter, this activity serves as an important reminder that threat actors are targeting cloud services as an entry point into networks. Later in the report, we will discuss how the criminal ecosphere of infostealers is likely abetting these kinds of attacks.
Ransomware Persists as a Prominent Threat
Kroll observed a 2% increase in incidences of ransomware in Q2. The rise underscores the continued prominence of ransomware activity. This is in spite of significant volatility in the space during Q1 with the seizure and disruption of LOCKBIT’s site and the exit of BLACKCAT ransomware after the Change Healthcare attack.
In May 2024, the United States Department of Justice named Dmitry Yuryevich Khoroshev as the individual behind the moniker LOCKBITSupp, the alleged operator of the LOCKBIT ransomware collective. However, just days after the publication of this indictment, the LOCKBIT site re-emerged, once again publishing names of victims.
As of the writing of this report, LOCKBIT site is still actively posting victims.
Kroll observed increases in activity related to INCRANSOM , MEDUSA, and the previously mentioned FOG ransomware group. Also observed were more cases of QILIN and RANSOMHUB, both of which are now associated with KTA243 (SCATTERED SPIDER).
Top 10 Ransomware Variants Q2 2024
CVEs on the Rise - Initial Access Methods
In Q2, Kroll observed a decline in phishing and an uptick in cases involving external remote services and vulnerability exploitation. As with similar quarters, phishing as an infection vector was most likely to be related to an email compromise threat.
Valid accounts counted for 19% of all cases in both Q1 and Q2. This is an initial access method whereby actors use easily guessed or compromised credentials to log into legitimate accounts. In May 2024, the CEO of Change Healthcare disclosed that credentials exposed on the dark web were the entry point for the attack that led to significant disruption and financial losses for hundreds of companies. Valid accounts were also associated with attacks against customers of the cloud service Snowflake.
Top 4 Initial Access Methods—Past Three Quarters
Initial Access Spotlight: PAN-OS
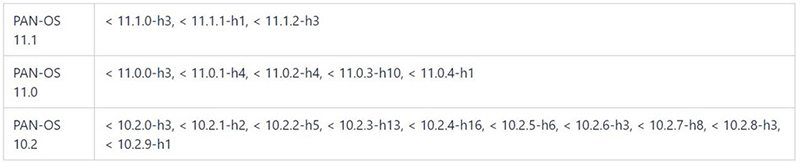
The increase in vulnerabilities observed in Q2 were tied to an influx of cases associated with CVE-2024-3400, impacting the Palo Alto Networks Operating System. This was a critical vulnerability in PAN-OS which could result in an unauthenticated root-privilege command injection.
Exploitation in the wild was noted as early as March 26 and rapidly increased after public disclosure. It impacted versions PAN-OS 120.2, PAN-OS 11.0 and PAN-OS 11.1.
If exploited on vulnerable PAN-OS versions and distinct feature configurations, an unauthenticated attacker could execute arbitrary code with root privileges on the firewall.
The majority of cases that Kroll observed related to this vulnerability where instances were attackers tested the vulnerability but did not move to unauthorized command execution. Of cases where there was post-exploitation, this issue was linked to lateral movement within victim networks via SMB/WinRM via stolen credentials and progression to ransomware, including LOCKBIT and AKIRA.
Malware Trends and Analysis
Kroll actively tracks malware C2 infrastructure, submissions to public sandboxes and active incident response (IR) and managed detection and response (MDR) case data to generate lists of the most active malware strains for comparison. In Q1, the most notable changes were a drop in activity from QAKBOT and PIKABOT. Kroll’s Cyber Threat Intelligence (CTI) Team believed that this was due to a shift in KTA248 behavior toward other malware strains, such as ICEDID and ICENOVA (LATRODECTUS). However, “Operation Endgame” conducted by Europol, the National Crime Agency (NCA), the FBI and others disrupted more malware ecosystems in May 2024, including arrests and infrastructure seizures affecting the ICEDID, PIKABOT and SYSTEMBC malware. Kroll observed the effects of this disruption in our case and open source collection data: impacted dropper malware such as ICEDID and PIKABOT dropped out of the top 10, to be replaced by commodity or open-source stealers and remote access trojans (RATs).
Common post-exploitation tools such as COBALT STRIKE and METASPLOIT remain in the top 10, making up a core part of attackers’ toolkits. It is clear that information stealers continue to be highly beneficial malware to develop infection chains for, enabling threat actors to quickly compromise a user and leverage their access to continue attacks on internal networks and SaaS and cloud environments.
In Q2, Kroll observed a rise in the distribution of infostealers via an infection chain beginning with tools such as CLEARFAKE or another “drive-by-downloader.” This often used loaders that were unaffected by Operation Endgame, such as GULOADER or IDATLOADER, to install infostealer payloads.
Top 10 Malware Strains - Q2 2024
CLEARFAKE
CLEARFAKE is the term used to describe the malicious in-browser JavaScript framework deployed on compromised webpages as part of drive-by compromise campaigns to deliver information stealers. It has the potential to impact all sectors. CLEARFAKE’s technique involves tricking users into initiating fake updates, ultimately leading to the installation of malicious payloads on their systems. The fake updates are often browser-related update prompts (Chrome or Safari) that appear on compromised websites through the use of JavaScript injections.
The CLEARFAKE campaign begins with a user browsing to a compromised webpage, typically a WordPress site. There appears to be no forced social engineering to persuade users to navigate to the compromise webpage; instead, CLEARFAKE acts as a drive-by compromise waiting for users to land on the page.
In May 2024, Kroll observed a new method that CLEARFAKE leverages to trick users into running malicious code on behalf of the threat actors, bypassing the initial download of files that would have previously conducted malicious activity. In these cases, Kroll observed the victim being redirected to a malicious webpage (in the format “{domain}/lander/powershell/index.html"), which is disguised as a browser error. Although it has a similar theme to previous fake update iframes, the decrease in the quality of the lure is notable because it does not appear to mimic any legitimate error that Chrome would produce
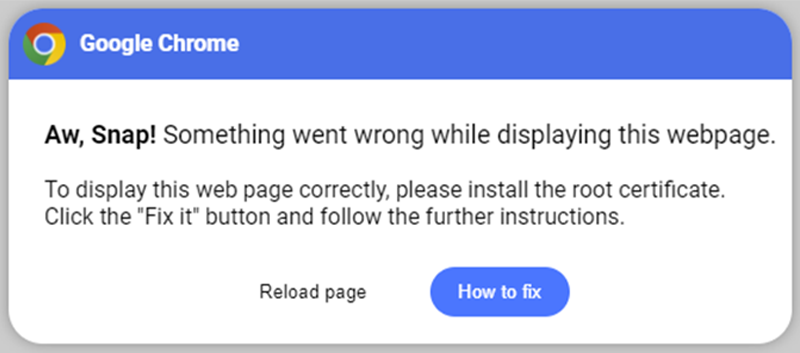
Initial Browser Error Screen
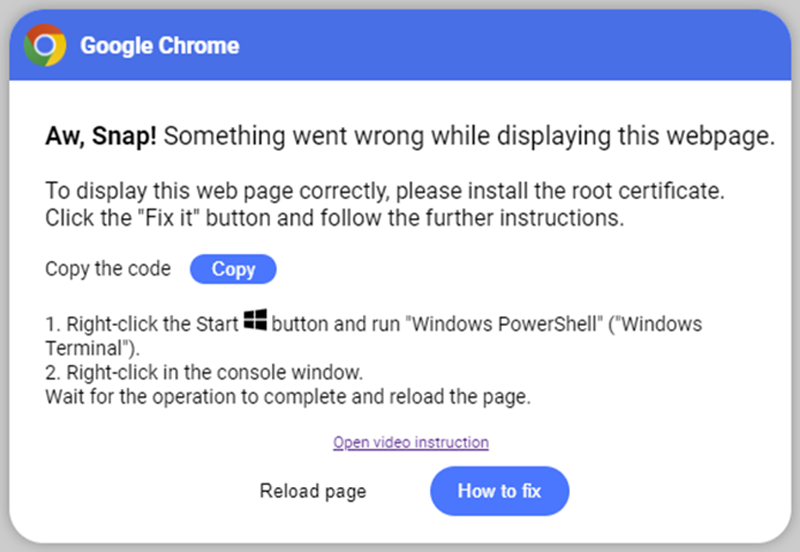
Follow-On Browser Error Screen With Instructions to Victim
(Source: Kroll. For a full technical analysis of this issue, view our article)
IDATLOADER (aka HIJACKLOADER)
Similarly, Kroll observed an uptick in IDATLOADER infections stemming from drive-by-download, used to execute information stealers on the victim machine.
In June, Kroll’s MDR team responded to an incident in which suspected malware was exhibiting strange download behavior. After successfully containing and resolving the incident, Kroll’s CTI team investigated further, uncovering a complex infection chain involving many layers of obfuscation being used to deliver IDATLOADER. Had the infection not been detected and stopped, it would have ultimately resulted in the deployment of information-stealing malware.
As the investigation unfolded, it was discovered that the IDATLOADER infection hinged on using Microsoft’s mshta.exe to execute code buried deep within a specially crafted file masquerading as a PGP Secret Key, also making use of novel adaptations to common techniques and heavy obfuscation to hide the malicious code from detection.
Additionally, Kroll identified a sideloading technique that leveraged Borland Package Library (BPL) files instead of regular dynamic link libraries (DLLs), which Kroll calls “BPL sideloading.” At time of writing, there is no MITRE sub-technique for BPL sideloading. Kroll has requested that a new sub-technique to be added to the MITRE framework.
Stay Ahead With Kroll
Cyber and Data Resilience
Kroll merges elite security and data risk expertise with frontline intelligence from thousands of incident response, regulatory compliance, financial crime and due diligence engagements to make our clients more cyber resilient.
24x7 Incident Response
Kroll is the largest global IR provider with experienced responders who can handle the entire security incident lifecycle.
Cyber Risk Retainer
Kroll delivers more than a typical incident response retainer—secure a true cyber risk retainer with elite digital forensics and incident response capabilities and maximum flexibility for proactive and notification services.
Kroll Responder MDR
Stop cyberattacks. Kroll Responder managed detection and response is fueled by seasoned IR experts and frontline threat intelligence to deliver unrivaled response.
Ransomware Preparedness Assessment
Kroll’s ransomware preparedness assessment helps your organization avoid ransomware attacks by examining 14 crucial security areas and attack vectors.



