Kroll identified several web compromise incidents via its cyber intake process during the month of June 2019, including cases that involved code injection techniques and sniffers. Web compromises most commonly affected the e-commerce platforms in the retail sector.
Web application compromises involve a variety of exploits directed at web applications (e.g., content management systems) and e-commerce platforms, such as the popular e-commerce platform Magento. Actors use techniques such as structured query language (SQL) injection, cross-site scripting (XSS) and account takeover (ATO) attacks to gain access to payment data and other personal information submitted on payment sites.
The National Vulnerability Database (NVD) posted an alert in April 2019 specifically on an SQL injection vulnerability in Magento which could allow an unauthenticated user to execute arbitrary code and gain access to payment information.
According to Kroll Managing Director J. Andrew Valentine, bad actors are primarily focusing their web compromise attacks on vulnerabilities in three areas: (1) the Magento platform itself, (2) third-party plug-ins and (3) misconfigured Amazon S3 buckets.
“Users can address the S3 bucket issue by simply configuring their AWS accounts with the proper access controls,” says Andrew. “However, dealing with the Magento and third-party plug-in issues is a more difficult proposition and requires both proactive and ongoing mitigation efforts. For example, a Magento idiosyncrasy requires users to patch sequentially. In other words, if a user applies the patch for the Magento issue noted in the April 2019 NVD alert but hasn’t applied earlier patches in sequential order, that vulnerability will remain unpatched until all previous patches have been applied first.”
Andrew also notes that many exploits used against the Magento platform and third-party plug-ins can be difficult to spot: “We find alterations in nondescript areas of websites, e.g., headers and footers, which can help them evade detection, or in PHP functions or third-party plug-ins, like customer support chat capabilities. Sometimes, attackers will strategically alter scripts in multiple areas of an e-commerce platform; in many of these cases, website owners may see one exploit, but not the others.”
From a proactive standpoint, Andrew says Magento users might want to consider running the Magento Security Scan Tool on their sites to help monitor and detect potential issues. The growing risk landscape may also warrant upgrading to a higher, more robust version of the Magento platform or exploring the PCI Security Standards Council list of Validated Payment Applications for potential alternatives.
See more of Andrew’s recommendations in the Experts Corner of this newsletter.
Magecart Compromises
Many exploits leveraged against e-commerce systems are often labeled or attributed to “Magecart.” According to Kroll consultant and dark web specialist Samuel Colaizzi, “Magecart is a generic term that is used by the cyber security industry to classify JavaScript inject attacks that sniff and scrape payment card data from e-commerce platforms, such as Magento. There is no specific code that would define an attack as being Magecart; rather, any JavaScript inject that sniffs and scrapes payment card data as well as other personally identifying information (PII) from payment sites would be classified as Magecart.
Technically Speaking: Sniffer E-commerce Exploits on the Dark Web
A packet analyzer, aka “sniffer,” is not an inherently malicious program; system administrators commonly use it to monitor network’s traffic. Bad actors, however, use sniffers to intercept data that they can monetize directly or through its sale, such as unencrypted passwords, usernames, account numbers, etc.
Below are screen captures of activity on the dark web where someone was selling a sniffer exploit (screenshot 1 below) and a credit card aggregation/dump (screenshot 2) that could have been obtained via this type of sniffer.
Screenshot 1
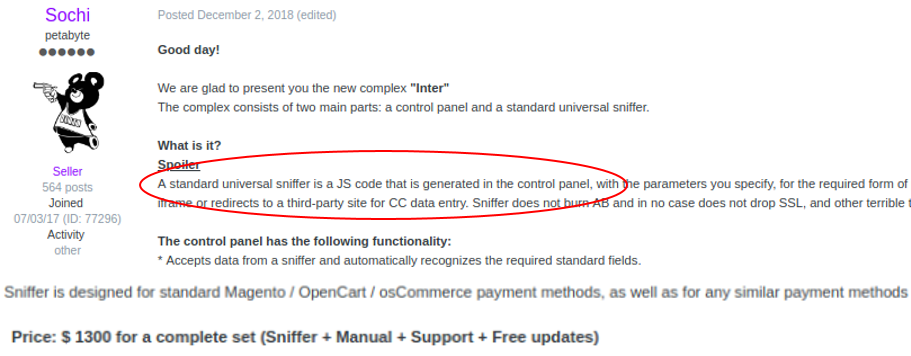
What is happening in the screenshot above:
- E-commerce exploit called “Inter” for sale on the dark web
- Seller “Sochi” posted advertisement on exploits forum on December 2, 2018
- According to open sources, this exploit continues to be sold by criminal actors.
Screenshot 2
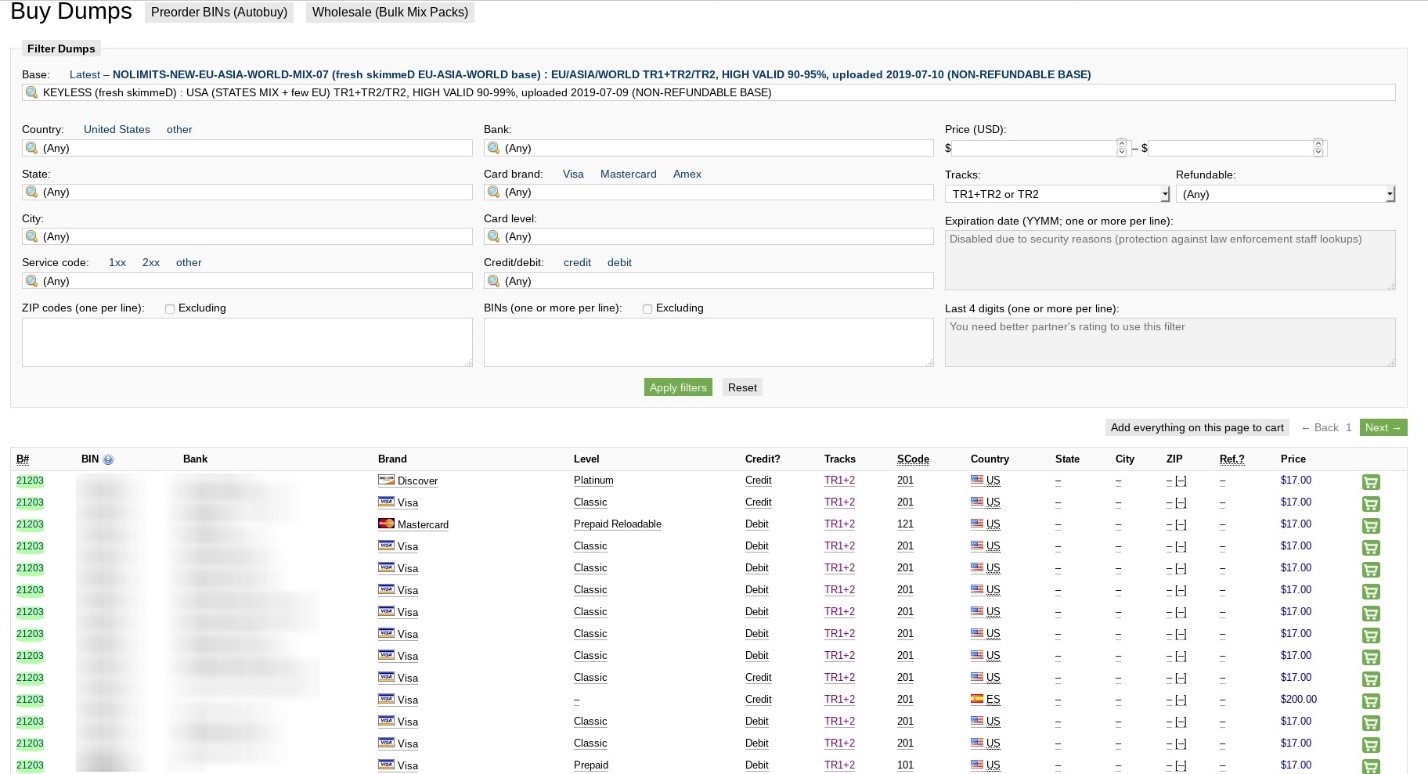
What is happening in the screenshot above:
- On July 9, 2019, JokerStash forum published an aggregated list of credit cards, which could have been obtained via a sniffer like the one that was being offered in screenshot 1.
- The JokerStash credit card dump provided credit card details, including track 1 and track 2 data for major U.S. credit cards.
- Card identifiers included bank and BIN number. (Kroll’s CyberDetectER® BINWatch can monitor for this activity, enabling clients to take quick action on these cards to preempt fraud.)
Case Studies
- Kroll reviewed one web compromise incident in which a software-as-a-service (SaaS) company discovered the website it used for transactions was injected with malicious code. When our analysts reverse-engineered the code, we discovered it was scraping sensitive data, temporarily storing it and then sending the data outbound. The malicious code impacted the victim’s cloud storage platform and affected the client-side browser.
- Another web compromise incident affected the payment system of a food service retailer. The retailer’s web developer conducted a security scan and found a JavaScript code exploit in the content management system (CMS) block. According to the web developer, the exploit was announced in March 2019 and identified as PRODSECBUG-2198 (an exploit against Magento).
Kroll Experts Corner: Best Practices for Mitigating Web Compromise
Managing Director Andrew Valentine recommends the following strategies for mitigating web compromises, particularly those affecting e-commerce sites.
- Understand and precisely follow the patching regimen for your e-commerce platform. In the case of Magento, remember that you must patch sequentially in order for patches to fully execute.
- Regularly review and properly configure access controls on Amazon S3 buckets.
- Implement a file integrity monitoring (FIM) solution, create hash sets for payment pages and monitor the findings every day for any alterations to payment functions.
- Similarly, consider employing an endpoint threat monitoring solution such as Kroll’s CyberDetectER® Endpoint Powered by Red Canary to provide early visibility to potential attack vectors enterprise-wide.
- Update to the latest version of your website’s content management system (CMS).
- Monitor the NIST National Vulnerability Database for new vulnerabilities related to the type of e-commerce platform your organization utilizes.
- Encourage the use of secure coding practices to prevent SQL injection and XSS.
The article above was extracted from The Monitor newsletter, a monthly digest of Kroll’s global cyber risk case intake. The Monitor also includes an analysis of the month’s most popular threat types investigated by our cyber experts. Subscription is available below.
NewsletterSubscription
JSS component is missing React implementation. See the developer console for more information.
Stay Ahead with Kroll
Cyber and Data Resilience
Kroll merges elite security and data risk expertise with frontline intelligence from thousands of incident response, regulatory compliance, financial crime and due diligence engagements to make our clients more cyber resilient.
Payment Card Industry Services
Kroll offers a wide range of services for both merchants and payment processors, from audits to incident management services, to pragmatic approaches for strengthening your cyber defenses.
24x7 Incident Response
Kroll is the largest global IR provider with experienced responders who can handle the entire security incident lifecycle.
