One of the original successes of early social media, Friends Reunited, recently announced that it would close permanently after 15 years. At its peak the site boasted over 10 million active users, though recently its participants had dwindled to “a handful” in the wake of Facebook, Instagram, LinkedIn and Twitter and the myriad of social networking sites in between. Obviously, for those of us that ever used the site, we may have had a publicly accessible profile that could have listed pretty unique personal information, such as what schools we attended, perhaps our closest and early friends and probably a good indication of where we lived when we grew up.
In terms of information security, forgotten or abandoned accounts on social networks can be a goldmine for identifying personal information about someone whether for spear phishing, password cracking attempts or social engineering. So while it’s always sad to see trailblazers be consigned to history, maybe all that historical information about our lives is better off out of reach from cyber criminals?
As investigators, we often come across abandoned accounts on LinkedIn, which might be a result of someone registering on the site when it first launched (back in 2003), or set up an account with a work email address at a previous employer and lost access, or a change in personal email providers so got forgotten about. These accounts are usually those with no photo, few connections and only a few personal details – but more often than not, especially if they were created at a time when Information Security was less of a hot topic, they will include school/university, a previous employer (“1998 to Present”) and the city where the person was at the time. Such information can give clues into an individual’s past and perhaps people they know via the “People also viewed” bar.
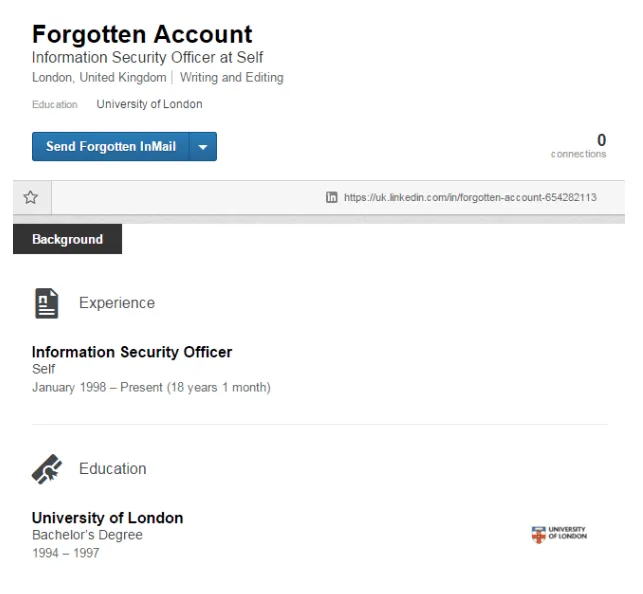
Most cyber criminals, like many people who spend their days in front of a computer screen, are there to earn money. But the difference (we hope!), is that they don’t usually like to work particularly hard especially if information that can enable a quick payday is so readily available and ripe for harvesting. Every now and then we may Google ourselves in moments of online vanity, but if you’ve been selected to be a victim for an identity theft, or worse as the unwitting façade for a social engineering or phishing fraud against your co-workers, criminals will use whatever information they can find about you to cash out: who you are, where you’re from and what you’ve done.
It has been estimated that 20 percent of LinkedIn accounts (over 80 million) out of the total registered 400 million are actually abandoned or forgotten accounts, just sitting there, maybe portraying an unconnected, unpopular, and certainly not the most professional version of you. It might also be gifting away your information security to those wanting to use it for ill-gotten gains. LinkedIn does not have a policy for closing inactive accounts.
So why not show yourself, or at least your online profile, some love and protection and dust away those world-wide cobwebs. After all, you are one of a kind.
Tips for online spring cleaning:
- Check on LinkedIn for any accounts that share your name and if you find a forgotten or abandoned account, recover the password and get it closed down.
- Consider (depending on how public or private you need/want to be) updating your Facebook, Instagram and Twitter Privacy settings to see what information you are sharing and who you are sharing it with, which could be everyone online.
- Did you ever have a MySpace account? If yes, what do you think happened to it? Most likely, it might still be out there.
- If you cannot figure out how to close an existing account, the great accountkiller.com, gives the direct routes to closing all the social/online media accounts that you no longer use.
Kroll provides a vast range of cyber and information security solutions including reviews of public records and social media to help protect the information that matters most to you or your business.
For more information, contact your local Kroll office.
