New Product Release Notes - Core Assessment Version 2.1
The CyberClarity360 team is proud to announce another major update – Core Assessment 2.1. Based on feedback from our corporate clients, providers and others in the third-party cyber risk field, the subject matter experts at CyberClarity360 have improved upon the current assessment by:
- Adding additional guidance notes to help non-technical audiences understand the questions
- Adding usability updates such as a glossary and a quick start guide
- Re-ordering of content to better align the logical and conceptual flow of the questions
- And more!
Download the full report by clicking the “Download” button. Please reach out to [email protected] to learn more or get a demo to see how CyberClarity360 can help you reduce your third-party cyber risk.
Guidance Notes
Many CyberClarity360TM providers are cyber security professionals, but not every organization that is assessed on our platform has security professionals on-staff. To increase the understanding around the assessment and the accuracy of the answers, and provide additional cyber risk education content for assessment participants, we have deployed two different guidance note modalities in our latest release: Executive and Extended Guidance Notes.
Executive Guidance Notes
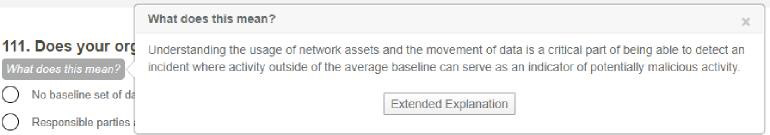
Following each and every control question (for more on control questions vs. insight questions, see Cross-Category, Cross-Section Question Migration), CyberClarity360 users will find a button that reads “What does this mean?” Clicking on the button will reveal a short paragraph designed to help clarify the content of the question and some examples of how the control in question might manifest in an organization:
Extended Guidance Notes
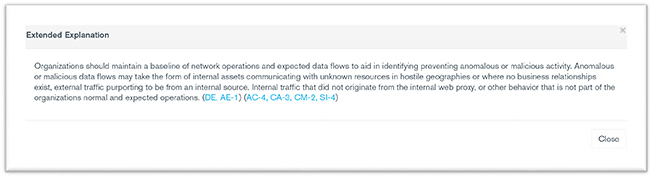
The extended explanation, available within every single Executive Guidance Note by clicking on the “Extended Explanation” button will provide additional detailed and technical content.
These Extended Guidance Notes align the content of the question to the control framework it is evaluated against. The content of these notes often features detailed language describing the implementation, validation, or other related mechanics of the control, and also includes direct links to the source material available in the NIST Cybersecurity Framework as well as the underlying NIST SP 800-53 Revision 4 control.
Usability Updates
In addition to adding technical support content to the assessment in the form of guidance notes, the CyberClarity360TM Core 2.1 release features an improved workflow (see Content Reordering), a complete glossary of the technical terms utilized across the assessment, and an embedded quick-start guide that allows users to make rapid, yet informed, progress in their assessment journey.
Glossary
Because much of the terminology used within the CyberClarity360TM Core Assessment are domain-specific and often highly nuanced (i.e. the difference between network segmentation and network segregation), a glossary is available to all users.
Our glossary includes full definitions of the terminology utilized within the assessment and is searchable. It is our hope that this glossary helps users better understand what is meant by each question, and it allows them to provide accurate assessments based on a clear understanding of not only the control question but the implementation of that control within their organization.
Quick Start Guide
The CyberClarity360TM Core 2.1 Assessment introduces a new category (Instructions) and section (Quick Start Guide) to support users who want to begin completing their assessment as rapidly as possible, but may have one or two outstanding question around platform functionality.
The Quick Start Guide covers various features and functionalities of the platform, including the aforementioned glossary, how to select and save answers, our delegation functionality to support collaboration within or beyond your organization, the question-level comments and evidence capability to support a rich and wholistic representation of one’s security posture and the certification and submission process.
Additional details can still be found in the Assessment Details menu, located at the top of each Assessment page, but the Quick Start Guide should get most participants making forward progress in short order.
Content Reordering
In addition to the features described above, there have been several changes made to the question order, scoring, and weighting mechanics of the CyberClarity360TM 2.1 Core Assessment. A detailed explanation of each is listed below.
Cross-Category, Cross-Section Question Migration
To better align the logical and conceptual flow of the questions, and more closely pair the control questions with their supporting insight questions, the following questions have been moved from one category and section into another category and section:
|
2.1 Question # |
Previous Category |
Previous Section |
New Category |
New Section |
|
6 |
Identify |
Asset Management |
Organization |
Target Profile |
|
24 |
Organization |
Demographic |
Identify |
Asset Management |
|
25 |
Organization |
Demographic |
Identify |
Asset Management |
|
31 |
Organization |
Information Security Team |
Identify |
Business Environment |
|
34 |
Organization |
Information Security Team |
Identify |
Business Environment |
|
50 |
Organization |
Certifications |
Identify |
Risk Management Strategy |
|
51 |
Organization |
Certifications |
Identify |
Risk Management Strategy |
|
61 |
Identify |
Asset Management |
Protect |
Identity Management, Authentication and Access Control |
|
67 |
Identify |
Asset Management |
Protect |
Awareness and Training
|
|
73 |
Organization |
Culture and Morale |
Protect |
Awareness and Training & |
|
74 |
Organization |
Culture and Morale |
Protect |
Awareness and Training
|
|
118 |
Organization |
Insurance Claims and Coverage |
Detect |
Anomalies and Events |
|
120 |
Organization |
Insurance Claims and Coverage |
Detect |
Anomalies and Events |
|
121 |
Organization |
Insurance Claims and Coverage |
Detect |
Anomalies and Events |
|
122 |
Organization |
Insurance Claims and Coverage |
Detect |
Anomalies and Events |
Intra-Category, Cross-Section Question Migration
To better align the logical and conceptual flow of the questions, and more closely pair the control questions with their supporting insight questions, the following questions have been moved from one category and section into another category and section:
|
2.1 Question # |
Previous Category |
Previous Section |
New Category |
New Section |
|
10 |
Organization |
Demographic |
Organization |
High Risk Territories |
|
11 |
Organization |
Information Security Team |
Organization |
High Risk Territories |
|
71 |
Protect |
Information Protection Processes and Procedures |
Protect |
Awareness and Training |
|
72 |
Protect |
Information Protection Processes and Procedures |
Protect |
Awareness and Training |
|
83 |
Protect |
Information Protection Processes and Procedures |
Protect |
Data Security |
|
85 |
Protect |
Information Protection Processes and Procedures |
Protect |
Data Security |
|
88 |
Protect |
Protective Technology |
Protect |
Data Security |
|
116 |
Detect |
Incident History |
Detect |
Anomalies and Events |
|
117 |
Detect |
Incident History |
Detect |
Anomalies and Events |
|
119 |
Detect |
Incident History |
Detect |
Anomalies and Events |
|
124 |
Detect |
Incident History |
Detect |
Anomalies and Events |
|
125 |
Detect |
Incident History |
Detect |
Anomalies and Events |
|
126 |
Detect |
Incident History |
Detect |
Anomalies and Events |
The CyberClarity360 team is proud to announce another major update – Core Assessment 2.1. Based on feedback from our corporate clients, providers and others in the third-party cyber risk field, the subject matter experts at CyberClarity360 have improved upon the current assessment by:
- Adding additional guidance notes to help non-technical audiences understand the questions
- Adding usability updates such as a glossary and a quick start guide
- Re-ordering of content to better align the logical and conceptual flow of the questions
- And more!
Download the full report by clicking the “Download” button. Please reach out to [email protected] to learn more or get a demo to see how CyberClarity360 can help you reduce your third-party cyber risk.
Guidance Notes
Many CyberClarity360TM providers are cyber security professionals, but not every organization that is assessed on our platform has security professionals on-staff. To increase the understanding around the assessment and the accuracy of the answers, and provide additional cyber risk education content for assessment participants, we have deployed two different guidance note modalities in our latest release: Executive and Extended Guidance Notes.
Executive Guidance Notes
Following each and every control question (for more on control questions vs. insight questions, see Cross-Category, Cross-Section Question Migration), CyberClarity360 users will find a button that reads “What does this mean?” Clicking on the button will reveal a short paragraph designed to help clarify the content of the question and some examples of how the control in question might manifest in an organization:

Extended Guidance Notes
The extended explanation, available within every single Executive Guidance Note by clicking on the “Extended Explanation” button will provide additional detailed and technical content.
These Extended Guidance Notes align the content of the question to the control framework it is evaluated against. The content of these notes often features detailed language describing the implementation, validation, or other related mechanics of the control, and also includes direct links to the source material available in the NIST Cybersecurity Framework as well as the underlying NIST SP 800-53 Revision 4 control.

Usability Updates
In addition to adding technical support content to the assessment in the form of guidance notes, the CyberClarity360TM Core 2.1 release features an improved workflow (see Content Reordering), a complete glossary of the technical terms utilized across the assessment, and an embedded quick-start guide that allows users to make rapid, yet informed, progress in their assessment journey.
Glossary
Because much of the terminology used within the CyberClarity360TM Core Assessment are domain-specific and often highly nuanced (i.e. the difference between network segmentation and network segregation), a glossary is available to all users.
Our glossary includes full definitions of the terminology utilized within the assessment and is searchable. It is our hope that this glossary helps users better understand what is meant by each question, and it allows them to provide accurate assessments based on a clear understanding of not only the control question but the implementation of that control within their organization.
Quick Start Guide
The CyberClarity360TM Core 2.1 Assessment introduces a new category (Instructions) and section (Quick Start Guide) to support users who want to begin completing their assessment as rapidly as possible, but may have one or two outstanding question around platform functionality.
The Quick Start Guide covers various features and functionalities of the platform, including the aforementioned glossary, how to select and save answers, our delegation functionality to support collaboration within or beyond your organization, the question-level comments and evidence capability to support a rich and wholistic representation of one’s security posture and the certification and submission process.
Additional details can still be found in the Assessment Details menu, located at the top of each Assessment page, but the Quick Start Guide should get most participants making forward progress in short order.
Content Reordering
In addition to the features described above, there have been several changes made to the question order, scoring, and weighting mechanics of the CyberClarity360TM 2.1 Core Assessment. A detailed explanation of each is listed below.
Cross-Category, Cross-Section Question Migration
To better align the logical and conceptual flow of the questions, and more closely pair the control questions with their supporting insight questions, the following questions have been moved from one category and section into another category and section:
2.1 Question # | Previous Category | Previous Section | New Category | New Section |
|---|---|---|---|---|
6 | Identify | Asset Management | Organization | Target Profile |
73 | Organization | Culture and Morale | Protect | Awareness and Training |
74 | Organization | Culture and Morale | Protect | Awareness and Training |
118 | Organization | Insurance Claims and Coverage | Detect | Anomalies and Events |
120 | Organization | Insurance Claims and Coverage | Detect | Anomalies and Events |
121 | Organization | Insurance Claims and Coverage | Detect | Anomalies and Events |
122 | Organization | Insurance Claims and Coverage | Detect | Anomalies and Events |
24 | Organization | Demographic | Identify | Asset Management |
25 | Organization | Demographic | Identify | Asset Management |
31 | Organization | Information Security Team | Identify | Business Environment |
34 | Organization | Information Security Team | Identify | Business Environment |
50 | Organization | Certifications | Identify | Risk Management Strategy |
51 | Organization | Certifications | Identify | Risk Management Strategy |
61 | Identify | Asset Management | Protect | Identity Management, Authentication and Access Control |
67 | Identify | Asset Management | Protect | Awareness and Training |
Intra-Category, Cross-Section Question Migration
To better align the logical and conceptual flow of the questions, and more closely pair the control questions with their supporting insight questions, the following questions have been moved from one category and section into another category and section:
2.1 Question # | Previous Category | Previous Section | New Category | New Section |
|---|---|---|---|---|
10 | Organization | Demographic | Organization | High Risk Territories |
119 | Detect | Incident History | Detect | Anomalies and Events |
124 | Detect | Incident History | Detect | Anomalies and Events |
125 | Detect | Incident History | Detect | Anomalies and Events |
126 | Detect | Incident History | Detect | Anomalies and Events |
11 | Organization | Information Security Team | Organization | High Risk Territories |
71 | Protect | Information Protection Processes and Procedures | Protect | Awareness and Training |
72 | Protect | Information Protection Processes and Procedures | Protect | Awareness and Training |
83 | Protect | Information Protection Processes and Procedures | Protect | Data Security |
85 | Protect | Information Protection Processes and Procedures | Protect | Data Security |
88 | Protect | Protective Technology | Protect | Data Security |
116 | Detect | Incident History | Detect | Anomalies and Events |
117 | Detect | Incident History | Detect | Anomalies and Events |
Stay Ahead with Kroll
Cyber and Data Resilience
Kroll merges elite security and data risk expertise with frontline intelligence from thousands of incident response, regulatory compliance, financial crime and due diligence engagements to make our clients more cyber resilient.
