Intro
Modern tools and techniques for mobile device forensics have dramatically changed how investigators and attorneys approach investigations, with mobile devices often being at the forefront of the investigation. The new approaches provide better options for quickly and efficiently analyzing tens or hundreds of devices in parallel while incorporating a wider array of information from the devices. Mobile devices have been a prominent part of disputes and investigations for over a decade, and with the ubiquity and intermixing of mobile devices for business and personal use, comes a wealth of data that is more data-rich and accessible than any other data source. That coupled with the frequency of usage and users’ sense of privacy makes mobile devices incredibly valuable in any investigative analysis.
Kroll’s advanced approach to mobile device analysis is to perform unified analysis across data types and devices that enables attorneys and investigators to interrogate and present all forms of mobile device data. The traditional approach has been to perform mobile device analysis in by-device isolation or to perform a traditional analysis whereby communication data (e.g., SMS) is treated like “documents.” Indeed, modern analysis tools and techniques allow for a faster, more powerful approach. In this piece, we present an introduction to performing modern mobile device forensic analysis.
Phases of Mobile Device Analysis
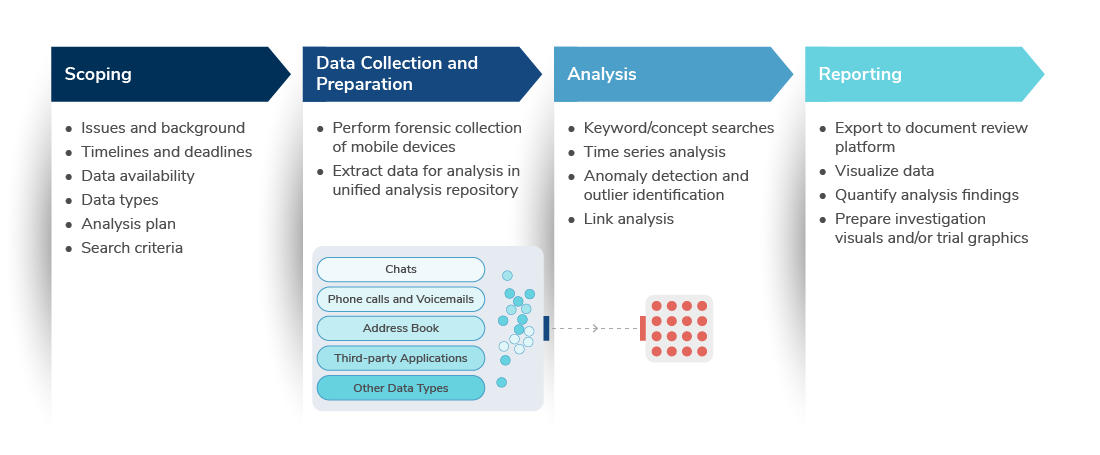
Mobile device analysis can be divided into several iterative phases. Every matter involving mobile device analysis begins with a process scoping, which critically includes steps to identify the goals of the analysis, selecting the data types to analyze (e.g., text messages), fact-pattern development, and establishing other logistical considerations. The second phase is the forensic collection of the devices, which can be performed via different means, such as Cellebrite or Oxygen Forensics, cloud-based collection or a logical collection of the device contents.
Once acquired, the mobile device data can be extracted and analyzed with a variety of tools. In simpler matters involving a small set of devices and limited or known issues, the data can be analyzed manually in spreadsheets or through traditional document review platforms. In complex matters, however, a unified analysis approach utilizing data analysis techniques is required. This approach involves the extraction of specific data types and the import of data across multiple mobile devices into a unified database for consolidated analysis.
The next phases — analysis and reporting — are more time-intensive and can require multiple iterations and additional data collection or analysis rescoping. As later discussed, the types of analysis used can vary, but the objective is to apply techniques based on known facts to accelerate the analysis and reduce time sifting through irrelevant data. The analysis phase can involve multiple iterations, with each iteration adjusting or refining the analysis based on newly gained information from prior analyses. The review and production phase involves the compilation of data into a visual and interactive platform for reviewers to consolidate their findings and produce them in the form of documents, metadata and/or visual representations.
The following chart illustrates this phased approach:
Mobile Device Data Types
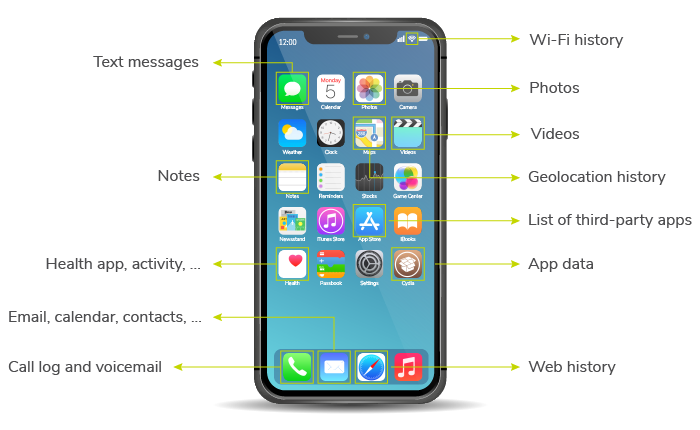
Every mobile device contains a unique, rich and expansive set of information. While every device is unique, several categories of evidence are primary to forensic analysis. These data types represent the communications, geolocation and other event-based data found on smartphones and tablets.
The following are several of the major categories of mobile device data types and the primary sets of content that are examined as part of an investigation:
|
Data Types |
Content |
Examples |
|
Communications |
Text messages |
SMS, MMS |
|
Chat messages |
WhatsApp, WeChat |
|
|
Call log |
Call participants, call timestamps |
|
|
Voicemails |
Voicemail audio file, voicemail timestamp |
|
|
Third-party app content |
Discord, fitness trackers |
|
|
Ephemeral messaging app info |
Signal, Telegram, Snapchat |
|
|
User Content |
Address book |
Names, email addresses and phone numbers |
|
Calendar |
Meetings, appointments |
|
|
File storage |
Downloaded files |
|
|
Web browser history |
Visited websites |
|
|
Pictures/Videos |
Camera roll, videos |
|
|
Notes/Tasks |
User-generated lists, memos and tasks |
|
|
Device Content |
Geolocation history |
Maps usage, device geocoordinates |
|
Third-party app list |
App name and installation dates |
|
|
Wi-Fi network history |
Wi-Fi network names, connection timestamps |
|
|
Deleted data |
Files and text messages |
Every type of data found on a mobile device is collected during the forensic acquisition; however, the data types selected for analysis depend on the scope and focus of the analysis. Once the data has been extracted, the data is available for analysis. Kroll’s methodology involves advising clients on which data types are potentially relevant and extracting the relevant data to a unified database to analyze those data in concert. Even if text and chat messages are the focus, analyzing other data sources — such as the phone’s address book and geolocation data — alongside the communications records yields a deeper understanding of events. This can include, for example, knowing where the device’s custodian was physically located when a key message was sent or identifying additional individuals for analysis.
Primary Types of Analyses
The types of analyses that can be performed on mobile devices vary based on the data types that have been selected and the objectives of the analysis. The key to a successful analysis process is identifying the fastest approach to performing analysis that is exhaustive and yields immediate results to support the broader investigation. Investigations rarely only require analysis of mobile device data, so the analysis of mobile devices should support the broader investigation’s objectives and aid in accelerating those other areas (e.g., interviews and document review).
Kroll’s experts and analysts work with clients to select from a library of over 30 standard and bespoke mobile device analyses.
The following table lists several of the primary analyses that are typically performed in our investigations:
|
Analysis |
Findings |
|
Keyword and concept searches |
Communications and other content containing queried text |
|
Network/link |
Relationships across and between individuals and organizations |
|
Data profiling |
Quantitative overview of available data by data type |
|
Cross-device |
Different treatment of similar data by custodians |
|
Deleted/hidden data |
Efforts to obfuscate or hide evidence |
|
Geolocation |
Events tied to geographic locations |
|
Timeline |
Events occurring at specific times |
|
Emoji and media |
Relevant non-text-based communications |
|
Address book |
Identification of individuals' names and contact information |
|
PII |
Identification of data with personally identifiable information matching specific values or formats |
|
Anomaly detection |
Identification of non-standard communications or behaviors |
The analyses can be separated into the objectives of reducing results or expanding results.
For reducing results, analyses can be combined to segment and otherwise refine the results. For example, a timeline analysis can be used in conjunction with concept searches to show the types of communications and other data containing those concepts over a specific time period. This analysis, subsequently, can be further refined to be limited to specific individuals or geographic locations.
Expansion analysis can be performed to identify additional relevant data from a set of responsive results. For example, the analysis can fan out from a single device to multiple devices using the same criteria, or an analysis can be performed to identify communications from a newly identified individual of interest. Another form of expansion analysis is identifying additional data sources based on information found on a mobile device, such as web history or third-party app history, that indicates the usage of social media or other platforms, such as Facebook, Instagram, Twitter or Slack.
Cross-Device Analysis
Analyzing multiple mobile devices in concert offers advantages for complex matters. A cross-device analysis approach enables analysts to identify additional individuals and establish much more information about communications and other events. Several of the benefits of analyzing multiple devices together are:
- Mining devices’ address books to associate names with phone numbers and accounts
- Identifying physical locations of individuals at points in time
- Building a map of known participants and the relationships in visualized network graphs
- Determining whether additional data should be collected
Most mobile devices contain over 200K discrete messages, files and other data. Analyzing multiple devices requires a strategic approach to correctly and efficiently search and develop fact patterns.
Cross-device analysis can better identify when certain data was deleted or altered by individuals, but it can also pose challenges to legal teams if not addressed properly. While forensic experts can typically recover deleted content, representing this across devices is more definitive and powerful. Cross-device analysis can pose challenges for legal teams who follow traditional approaches of producing deduplicated data.
Consider the following example, where the devices for two chat participants were acquired. One custodian did not perform any deletions, while the other custodian selectively deleted messages. Both copies of the message threads contain valuable information, which is why Kroll develops an analysis strategy with legal teams in advance of any review and production. Performing a cross-device analysis ensures that situations like the one below are identified prior to document review and production.
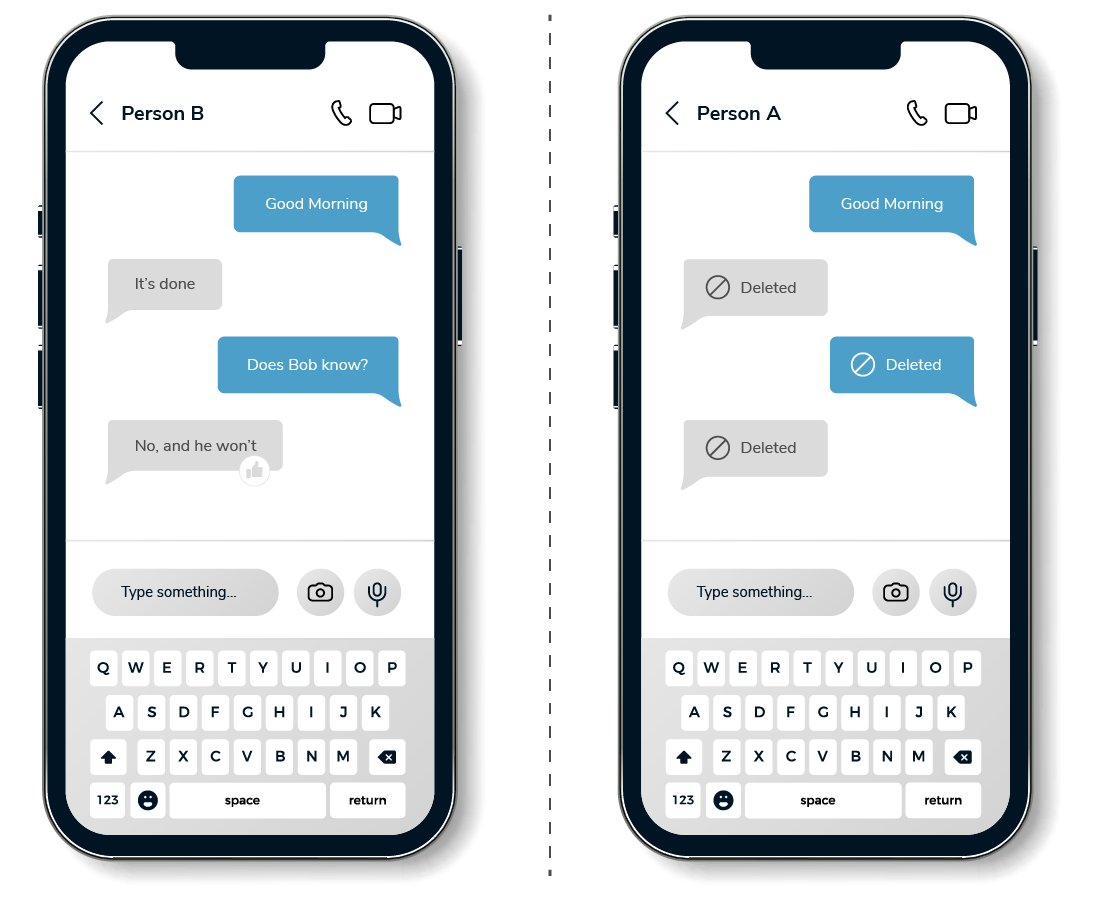
A cross-device analysis requires rigorous auditing and metadata management to track source data and enable more powerful cross-device analysis. Several key points to consider when conducting a cross-device analysis are:
- Storing and tracking all available metadata about the devices, device collections and data is critical for evidence management
- Analysis across different data types requires precise data mapping and a deep understanding of mobile device data
- Data types and metadata across different iPhone and Android devices can impact unified analysis if not properly addressed
- Applying data across all devices, such as address books, can create issues if not properly performed
Kroll’s approach involves managing source data in a unified database and making the data available for legal teams through traditional document review platforms, such as Relativity, and through self-service analytics platforms for deeper analysis, visualizations and custom searching.
Designing a Mobile Device Analysis Strategy
Every mobile device investigation is unique, but there are common approaches to devising an analysis strategy. These steps begin with compiling known information regarding the investigation and isolating key facts or theories for further corroboration or analysis expansion. For example, if an investigation centers around three events at specific points in time, the analysis can be developed around those epochs to identify the individuals involved, whether any communications or other event-related data are found on the devices, and to begin culling or expanding the channels of communication and keywords/concepts involved in the investigation.
In parallel, mobile device data should be profiled to assess what information is available and whether anomalies or data gaps exist. One approach is to perform an automated data profiling to assess summary-level details on the data found on the mobile devices, generate data timelines and identify relationships between individuals. This type of profiling allows investigators and attorneys to quickly assess what information is available and begin identifying what data to further analyze.
A successful mobile device analysis typically has a defined stopping point when the analysis is complete or sufficient. Determining when to stop depends on the nature of the investigation, but there are several ways to gauge this. The first is establishing at the onset which and how the narrowing analyses will be performed, whereby narrowing filters are applied and the expected communications and other details are identified. That is, the analyses to filter out extraneous information and find key data is defined at the beginning. The second test is reviewing the expansion analyses to assess whether those are complete and that each finding from those was reviewed. Virtually no investigation can establish the precise stopping point criteria before the analysis is performed but having those criteria in mind throughout aids the investigation.
The analysis strategy should include an approach to how the data will ultimately be reviewed and reported. One approach is to transfer mobile device data to a document review system, such as Relativity, for review. These types of systems enable attorneys and other reviewers to review mobile device content in a common platform alongside email and electronic documents. One key consideration for this process is to determine how communications and other data are represented. Text messages and other communications can be printed to PDFs in formats to look like the original messages, and other data can similarly be printed to a file format based on the metadata to represent a document.
A second approach is to review the metadata and quantitative results of the analysis in a data visualization platform. A data visualization platform enables reviewers to examine information and apply filters to the data to identify data patterns. The visualizations can be printed and produced to represent the findings. This approach can be conducted in conjunction with or in lieu of reviewing data in a document review platform.
Conclusion
Mobile device analysis is a process rich with opportunities to examine data alongside one another and explore the variety of data types and devices. Advanced tools, such as self-service analytics and visualization platforms, enable investigators and legal teams to perform these analyses faster and with much more depth than is traditionally considered with document review tools. The keys to a successful mobile phone analysis are to properly scope the goals and known facts in a case and then systematically analyze the data.

