As organizations consider restarting operations and opening doors, how to engage their third parties becomes very important. Some third parties will have closed, been acquired or emerge radically different into the recovery. Are you prepared to discuss how they are focusing on securing the data you share with them in this new normal? There are many controls you should examine to ensure adequate cyber security maturity in your third parties. While all play an essential role, a massive crisis such as COVID-19 elevates specific controls to priority.
At Kroll, we collect security data on organizations across the state and can evaluate it through the lens of our decades-old experience dealing with third parties.
We have produced a list of controls to focus on as well as statistics to serve as rough benchmarks for you to start your third-party planning. We hope this document will help guide your prioritization of which controls to focus in on as you engage your third-party ecosystem and move your organization from “shelter-in-place” to “recovery.” A high-resolution PDF is also available for download, and we encourage its dissemination across your team to ensure the right controls are getting the proper attention.
Third-Party Cyber Risk Readiness
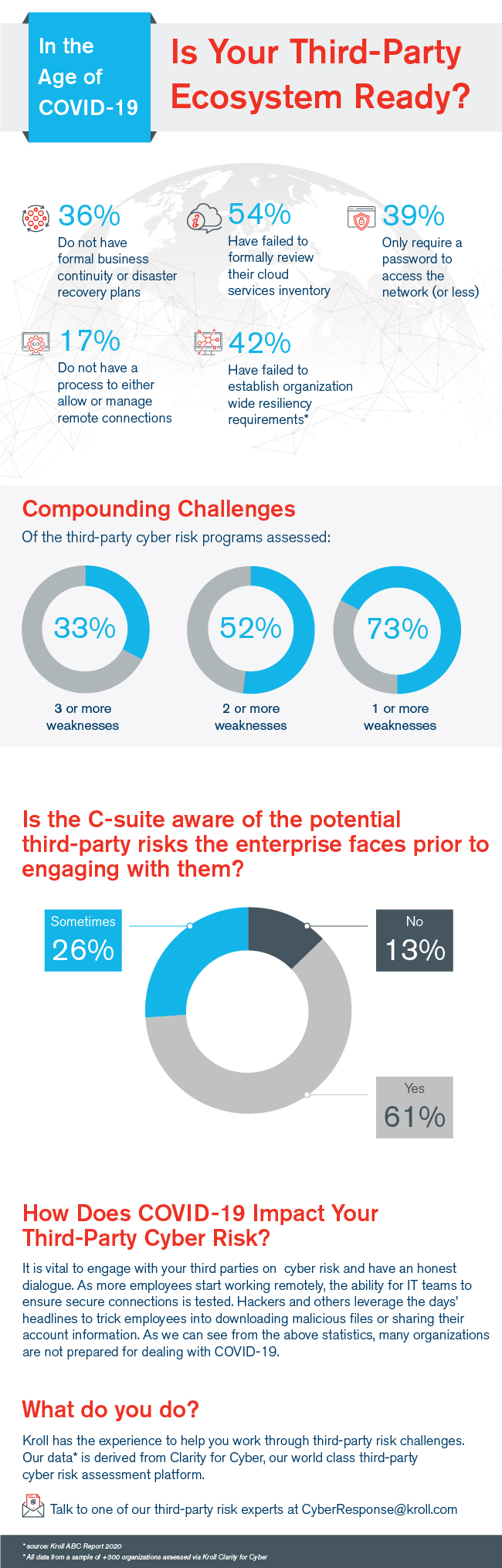
As indicated in the infographic, many third parties did not have the right controls in place heading into the COVID-19 pandemic and may be currently struggling as a result.
How you move forward with your third parties may mean the difference between substantial success in recovery and challenges down the road. Kroll offers robust third-party risk management solutions, which includes cyber risk and enhanced due diligence.
Stay Ahead with Kroll
Cyber and Data Resilience
Kroll merges elite security and data risk expertise with frontline intelligence from thousands of incident response, regulatory compliance, financial crime and due diligence engagements to make our clients more cyber resilient.
Cyber Risk Assessments
Kroll's cyber risk assessments deliver actionable recommendations to improve security, using industry best practices & the best technology available.
