The past several years has been a bonanza for the underground economy as it relates to the purchase and sale of stolen private information and, specifically, to the sheer number of individual consumer records impacted. Numerous large merchants, hospital systems, and insurance companies have been hacked, exposing email addresses and passwords, credit card numbers, and personal profiles. These breaches have resulted in a considerable surge in private personal information being made available for sale in the underground economy. Throughout this same time frame, security companies, researchers, and hackers have commented on the vast amounts of data that have been stolen and are now available for purchase online. Indeed, we have heard all too often from the popular media that billions of personal records have been compromised.
While heightening awareness of identity security and data breaches, the repeated reports of large, high-profile breaches might bring with them another significant risk – many of those impacted can become numb to it all and view the loss of personal information as inevitable. This sense of inability to alter the course of events, while perhaps understandable, is not accurate. As we explain, there are real steps that can be taken to combat the impact of such data thefts. Complacency is not the answer.
This underground economy, which lives in what is often called the “Dark Web,” is a vast place, where all kinds of information can be bought and sold. In this article, we explore the motivations that drive the criminal behavior and the methods and tactics used by criminals to maximize their economic return. As noted above, all kinds of personal information are available for sale on the Dark Web. Here, we focus on one type of information – stolen credit card data – something that impacts millions of people each year. And, we offer some concrete recommendations that can be taken in response to this privacy and financial risk.
The Simple Economics of Stolen Credit Card Data
Unlike diamonds, fine wine, and other valuable goods, stolen credit card data does not get better with age. From the moment credit card information is stolen a race begins between the cyber criminals who seek to sell the credit card number and the banks trying to protect their customers from financial loss. The sellers of the stolen data are trying to get the card numbers quickly into the hands of buyers before the banks can even discover that a merchant has been breached. This race to exploit the “fresh” credit card data results in a high fraudulent use rate. It is important to understand that perpetrators who steal the credit card data sell that information to a different set of bad guys who are also intent on exploiting the information and maximizing the economic return on their illicit investment.
If you are a thief and you have paid $20.00 for a stolen credit card number available for sale on the Dark Web, you want that card number to enable you quickly to acquire at least $1,000.00 in goods. After taking possession of those goods, you will then try to sell them to a reseller and convert them into cash valued at anywhere from $100.00 to $500.00. Thus, in this example, the cyber criminal who purchases the credit card data nets a return of between 5x and 25x on his initial investment. Simultaneously, the banks are working hard to identify and assess transaction anomalies, evaluating variables such as velocity controls (e.g., if a card is used in New York at 5 p.m., how can it physically be in Dallas at 6 p.m. the same day), as well as historical cardholder behavior.
Because of the market dynamics associated with stolen personal information, a card database from a freshly hacked business may start out selling at $20.00 per card with 90% of stolen card numbers being successfully used to execute a fraudulent transaction. Within a week or even a few days of the initial theft, the likelihood of a successful fraud transaction may decline to 50%, and the selling price for that same card data likely will fall precipitously to $3.00 per card number. Just like a thief in a store wants to avoid being caught on camera, traffickers of stolen credit card numbers do not want to develop a reputation of selling cards that are likely to get flagged as fraudulent. Thus, the data – like bread in a grocery store – has a finite shelf life and speed of action in the criminal chain is essential to the thieves’ reaping any financial gain.
Changing Incentives to Slow Down Data Thieves
- Chip and pin
As it relates to credit card transactions, the United States continues to transition from “card swiping” technology to chip-based card processing. As this transition takes hold, we anticipate it will become harder and harder for hackers to gain access to quality, valid credit card numbers. This is because while the data thieves may still be able to intercept a chip card number, there are additional security measures in place that make that intercepted number virtually worthless. With less exploitable credit card data available for sale, the price of stolen card numbers can be expected to rise. So, building on the example above, a credit card number may now sell for $35.00 instead of $20.00. Like everything else, it comes down to a market defined by supply and demand. At the same time, the banking industry will have a much smaller subset of transactions to monitor and examine, hopefully leading to more declines of fraudulent transactions. However, the methods used by those intent on stealing and exploiting credit card data likely will adjust over time, and the race discussed above will start all over again.
- “Card Not Present” fraud – the UK experience
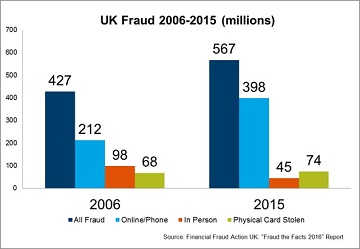
“Card not present” fraud, those transactions that are completed over the internet or on the phone, present a very different set of risks and the story is equally different. The United Kingdom is our best point of comparison. The UK converted to chip and pin over 10 years ago and has already experienced the pain associated with the switch. Since switching to chip and pin technology in 2006, the UK has experienced a shift in fraud cases. A Financial Fraud Action UK report found that before the transition, 50% of card fraud was accomplished via online or telephone fraud, and 23% was accomplished using counterfeit credit cards. Ten years later, in 2016, the remote (“card not present”) fraud was up to 70% of all fraudulent transactions, and counterfeit credit card fraud was down to 8% of all fraudulent transactions. During this same time, overall losses to businesses increased by 30% and the total number of accounts defrauded increased 62%.
Credit Card Fraud – The Future Outlook
With reference to the UK experience, we expect a very similar pattern to occur in the United States. There have been significant changes in the retail landscape over the past 10 years which will impact the specifics of how this plays out. For instance, methods for physical delivery of goods have changed the risk landscape. One of the downside risks for card thieves has always been having to wait for a package to be physically delivered after ordering something online using the stolen credit card number. Logistically, the malicious actors have had to find an address suitable for delivery, preferably one that would not trace back to them. They also have had to worry about the time between the initial order being placed and the arrival of the package itself – the longer this time gap, the greater the ability for the merchant and/or the police to discover that a crime had taken place.
Today, with multiple delivery methods available from some of the largest online retailers and the emergence of small startups offering to pick up packages and deliver them in hours (if not minutes), the window for discovery of a criminal transaction has closed significantly – making it easier for perpetrators to execute a transaction and get away with the fraudulently acquired goods.
In the past 10 years, the sales from physical retail space have taken some serious hits while online retail sales have quadrupled. This is evidenced by both statistics from the U.S. Department of Commerce as well as the number of traditional retailers that have closed stores or gone out of business completely. Online retailers are competing for business in an incredibly aggressive marketplace. Trying to strike that balance between fraud prevention and retaining customers is difficult. Rejecting a legitimate online transaction is the last thing a merchant wants to do as it may drive that customer away forever.
Combining all of these factors – faster delivery, more online retailers, and consumers who are more and more willing to make online purchases – means that the most logical place for fraud to shift is the same direction as in the UK. More and more “card not present” fraud is likely to occur. The cyber criminals are looking to get lost in that ever-growing sea of online transactions, and they will.
What Can Consumers and Businesses Do to Reduce These Fraud Risks?
On the consumer side, preventative controls can be difficult. A person never knows if a restaurant, store, or online merchant is going to be breached, so it can be hard to prevent completely such fraudulent transactions. That said, we do have some recommendations:
- Make smart choices. Do not use your debit card when you have to swipe – only use your credit card in those instances. The simple reason is, if your credit card gets compromised, it is the bank’s money that is at risk; the bank is both able and better equipped to carry that risk while the suspect transaction is disputed. If your debit card is stolen, it is your money that is being siphoned out of your bank account. You may ultimately be entitled to reimbursement, but you are without the use of those funds during the time the investigation remains ongoing. While laws may impose limits on the extent of a direct financial loss, recovery of your money is not instantaneous.
- Purchase ID theft protection. ID theft protection can keep an eye out for your personal information and notify you if there are indications of changes to your credit or non-credit profile that may indicate you are at risk. ID theft protection and restoration coverage can also help you fix the problem after it happens. And, because there is no perfect way to inoculate yourself from this risk of personal data loss, the availability of skilled, trained investigators who can work with you to respond to and remedy the adverse impacts that you may suffer is incredibly valuable and can speed your recovery. You can purchase a service directly, but many employers now offer reasonably priced protection through workplace benefits.
The merchant side is more complex. Most businesses are focused on delivering their goods and services to as many consumers as possible, and fraud is not the first thing on their mind. But there are steps that merchants can and should take:
- Adopt Chip and Pin Processing. First and foremost, migrate to chip and pin processing as soon as feasible. This switch will drive away counterfeit cards and also limit your liability.
- Use a Quality Card Processor. A good card processor will have tools in place, in addition to the banks, to assist with flagging potentially fraudulent transactions.
- Pay Attention to Delivery Time Windows. Be cautious of same-day delivery options for your customers who order online and watch for other flags that a transaction may not be legitimate.
Final Thoughts
Because so many of us have become accustomed to transacting business over the internet and using social media networks, more and more of us have become immune to news about data breaches and other incidents that threaten the security and privacy of our personal information. An attitude of “well it’s going to happen to me eventually, so there’s nothing I can do” has emerged, but there are tangible steps we all can take that can limit our risks and, in the event of a loss, reduce our financial exposure. In the end, each of us must be aware, ever vigilant, and take proactive steps to protect and manage individual and family member personal information.
By David Dunn
Stay Ahead with Kroll
Cyber and Data Resilience
Kroll merges elite security and data risk expertise with frontline intelligence from thousands of incident responses and regulatory compliance, financial crime and due diligence engagements to make our clients more cyber- resilient.
Forensic Investigations and Monitorships
The Kroll Investigations, Diligence and Compliance team consists of experts in forensic investigations and intelligence, delivering actionable data and insights that help clients worldwide make critical decisions and mitigate risk.