On October 16, 2023, Kroll Cyber Threat Intelligence (CTI) analysts were made aware of an ongoing exploitation of a recently discovered vulnerability within the web user interface (UI) functionality of Cisco IOS XE (CVE-2023-20198). This security flaw is critical with a CVSS score of 10.
Score Range | Severity Category |
|---|---|
0.0 | None |
0.1 – 3.9 | Low |
4.0 – 6.9 | Medium |
7.0 – 8.9 | High |
9.0 – 10.0 | Critical |
Figure 1- CVSS Vulnerability Scores and Categories
A device must have all the following requirements to be exploitable:
- Must be running Cisco IOS XE software
- Must be internet-facing
- Must have the web UI feature enabled
According to Figure 2, at the time the advisory was published, there appeared to be approximately 143,000 devices that match the criteria above.
Figure 2 - Devices Potentially Impacted as of October 17,2023 (Source: Kroll)
The vulnerability enables a remote, unauthenticated attacker to establish an account on a vulnerable system, granting them privilege level 15 access (the highest access), which the attacker can utilize to assume control over the compromised system.
Since the initial advisory from Cisco, there have been multiple reports in open-source of widespread exploitation of this vulnerability. Kroll has observed evidence of this exploitation within its managed detection and response (MDR) client base where many of the same indicators of compromise shared across the intelligence community were present.
Following the establishment of a privileged account, the threat actor was observed installing an implant, providing short-term command execution. In Cisco’s initial blog post, they note that some of the implants have been installed with a previous vulnerability in Cisco’s web UI IOS ZE tracked as CVE-2021-1435. This vulnerability has a CVSS score of 7.2 and allows for an authenticated, remote attacker to inject arbitrary commands that can be executed as the root user. This vulnerability is due to insufficient input validation. However, more important, Cisco also states that fully patched systems also had the implant installed, where the installation method appears likely through a new vulnerability: CVE-2023-20273.
As part of ongoing investigations, Kroll observed successful logins from the malicious IP address 154[.]53.56.231 from the user account “cisco_support” (Figure 3), which is not a legitimate account within the victim environments. Furthermore, Kroll has also observed the implant saved under the file path “/usr/binos/conf/nginx-conf/cisco_service.conf”, which is consistent with existing tactics, techniques and procedures (TTPs) reported in open-source reporting for this campaign.
Figure 3 - Login from Threat Actor-Created Account (Source: Kroll)
Risk of Compromise
Malicious actors possessing unrestricted remote access to a network device could carry out the following actions, each with its associated consequences:
- Surveillance of network traffic involves eavesdropping on sensitive network communications.
- Injecting and redirecting network traffic can lead to man-in-the-middle attacks, posing a risk to the enterprise.
- Breaching protected network segments is a potential consequence.
- Leveraging the unrestricted remote access as an initial entry vector to the network becomes feasible due to the absence of detection and protection solutions for these devices, often going unnoticed until disruptions to user activity become apparent.
Hunting for Exploitation
Below is a list of methods for hunting exploitations of this vulnerability against an affected system:
- Check the system logs for the presence of any of the log messages akin to Figure 3, where “user” could be “cisco_tac_admin”, “cisco_support” or any configured, local user that is unknown to the network administrator
- Search for the implant installation path that has been observed as "/usr/binos/conf/nginx-conf/cisco_service.conf"
- Run the following command against the potentially affected device (replacing the relevant IP address), to identify if the implant is present:
curl -k -X POST "https[:]//DEVICEIP/webui/logoutconfirm.html?logon_hash=1"
A positive match (implant installed) will return a 40-character hexadecimal string that is hardcoded into the implant and unique to each implant.
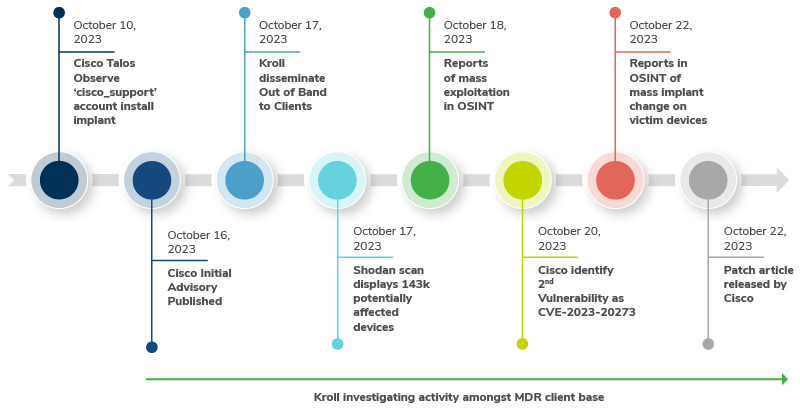
Figure 4 - Timeline of Events (Source: Kroll)
TTPS
Kroll has not observed actions further to the implant being installed.
Patch Available
On October 22, 2023, Cisco released an article stating that a software fix was available to patch against CVE-2023-20198. A comprehensive breakdown of affected products and version available can be found in the article.
Conclusions
The mass exploitation of CVE-2023-20198 highlights the essential requirement for strong cybersecurity protocols and prompt reaction strategies within enterprises.
The ongoing exploitation of this vulnerability showcases the persistent endeavors of threat actors to take advantage of system vulnerabilities. This underscores the need for organizations to promptly install patches and establish a sustainable, long-term cybersecurity framework.
Key measures to develop a robust cybersecurity infrastructure encompass routine system log monitoring for irregular activities, training personnel to identify potential threats, preparing an incident response plan, and engaging in regular threat hunting and internal and external penetration tests.
Recommendations
- Apply the relevant patch to CVE-2023-20198
- Administrators of affected devices should disable the HTTP Server feature on all internet-facing systems. To disable the HTTP Server feature, use the no ip http server or no ip http secure-server command in global configuration mode. If both the HTTP server and HTTPS server are in use, both commands are required to disable the HTTP Server feature.
- Conduct hunting for exploitation on any devices that match the requirements for exploitation listed above
References
1. Cisco: https://sec.cloudapps.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-iosxe-webui-privesc-j22SaA4z
2. Cisco Talos: https://blog.talosintelligence.com/active-exploitation-of-cisco-ios-xe-software/
3. Cisco Patch: https://www.cisco.com/c/en/us/support/docs/ios-nx-os-software/ios-xe-dublin-17121/221128-software-fix-availability-for-cisco-ios.html
Stay Ahead with Kroll
Cyber and Data Resilience
Kroll merges elite security and data risk expertise with frontline intelligence from thousands of incident responses and regulatory compliance, financial crime and due diligence engagements to make our clients more cyber- resilient.
Cyber Vulnerability Assessment
Proactively identify vulnerable systems and devices that may be exploited by an attacker or malicious software, often resulting in data loss or breach.
Data Breach Notification Letters
Kroll will work with your team to implement a personalized, plain-language notification letter that provides pertinent information and maintains message control.





