Many times, Kroll is asked to conduct a cyber security vulnerability assessment to gauge the state of a client’s information security. Part of this cyber security assessment often includes penetration testing — or in other words, the client will ask (and authorize) our cyber security experts to actively try to break into the client’s network. By learning where gaps exist in their security regime, the client can then target the necessary resources and improvements that will better protect client data.
As one of Kroll’s cyber experts, I spend a lot of my time “hacking” into networks across a wide variety of enterprises and industries. In this article, I want to highlight some of the most common hacks that cyber criminals use, and also share security measures that you can implement to stay ahead of attackers.
Microsoft Office Macros
One favored method for breaking into networks used by hackers— and thus one that I use often, unfortunately with great success — is sending a Word document with a malicious macro. When employees open up my document, they are presented with the following yellow bar and button:
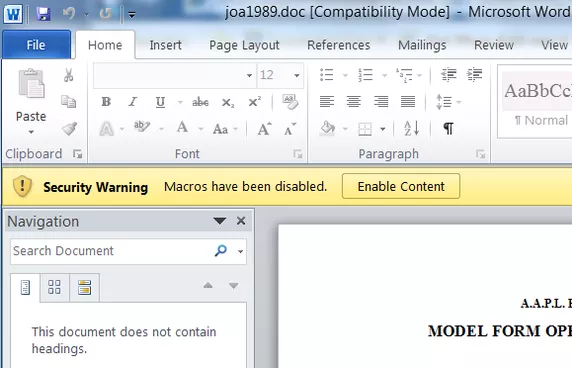
If an employee clicks on the Enable Content button, my “malware” is instantly installed on his or her computer. Afterwards, every 30 minutes, the computer connects back to my server and allows me to gain complete access. From the user's perspective, however, there is no indication that the computer is being controlled remotely.
Pass the Hash Attack
Computers running on Microsoft Windows typically have “domain accounts” and “local accounts.” Employees typically have domain accounts that allow them to access their own computer as well as external resources, such as the company’s file share. Local accounts, by contrast, exist only within the user’s computer and don’t have any special permissions outside of the local computer — hence, the name local accounts. The most common local accounts are Administrator and Guest. Microsoft Windows keeps a “hashed” copy of the password for local accounts stored on the hard drive. (In simple terms, hashing is the process where data — in this case, the password — is converted into a string of characters using a predetermined algorithm. The given “value” of the hashed password is stored and used to validate the password that the user types in. The password is stored as a hash because hashes cannot be converted back into passwords.) In more than 90% of the organizations I test, most computers have the same local Administrator password. Unfortunately, the password hash of a local account can be used in place of the password to log into the computer. The result is that I can use the password hash to bounce from computer to computer very quickly without even knowing the local Administrator password.
Mimikatz
Mimikatz is a tool that allows an attacker to extract a domain user’s password straight out of memory of a Microsoft Windows computer. In other words, if the employee who opened up my malicious Word document has a very complex password, such as “MyVoiceIsMyPassport!”, I am able to discover that password by using Mimikatz. If the organization doesn't use two-factor authentication, I can log into any internet-accessible website that the employee has access to. Certain implementations of Mimikatz are launched directly in memory and don't touch the hard drive. This attribute makes it invisible to anti-virus software.
Effectively, this means that once I get on a computer, I can use the local Administrator password hash to connect to other nearby computers. With Mimikatz, I can then steal the passwords of the employees who are logged into the computers that I can access. If I can find a Domain Administrator's computer, I can steal his or her password and gain complete access to the whole environment. All of this can happen in a matter of hours.
Best Practices to Neutralize These Common Hacks
While these common hacks are just a few in the cyber attacker’s arsenal, they are attacks that your organization can neutralize by implementing these security measures:
- Screen out documents with macros. Make sure your email system can filter out Microsoft Office documents that contain macros. While you can certainly instruct and remind employees to not enable macros in emailed documents, avert the problem by ensuring employees do not receive them at all.
- Employ two-factor authentication. As discussed, passwords are easy to get or guess. Unfortunately, having complex passwords isn’t enough. It is important to use two-factor authentication for all external access. For example, if a company has an employee portal that is internet-accessible, the company should ensure that access to the portal requires more than just a password to access it. It could be a code sent to the employee’s phone or a special token generated by a device or app. With two-factor authentication, an attacker would not be able to access the web application just with a stolen password.
- Differentiate passwords, segregate accounts. Organizations should ensure that each server and workstation have different local Administrator. Another alternative is to prevent local accounts from authenticating to the network. Implementing this will make it very difficult to gain access to other parts of the network.
Just like most criminals, hackers prefer to take the path of least resistance when trying to break into networks. Don’t make it easy for them to steal your company’s data. If your organization hasn’t done so already, you will be ahead of the game by addressing these common vulnerabilities now.
Stay Ahead with Kroll
Forensic Investigations and Monitorships
The Kroll Investigations, Diligence and Compliance team consists of experts in forensic investigations and intelligence, delivering actionable data and insights that help clients worldwide make critical decisions and mitigate risk.
Cyber and Data Resilience
Kroll merges elite security and data risk expertise with frontline intelligence from thousands of incident response, regulatory compliance, financial crime and due diligence engagements to make our clients more cyber resilient.