On December 20, 2018, the U.S. Department of Justice (DOJ) announced an indictment charging two Chinese nationals with conspiracy to commit computer intrusions, conspiracy to commit wire fraud and aggravated identity theft. At first blush, the indictment might appear to be an interesting, if typical, round of cost imposition and public attribution intended to control international cybertheft. The announcement, however, contained an important detail about the hackers’ targets that raise the indictment from merely interesting to remarkable.
In the words of the indictment, the attackers “engaged in an intrusion campaign to obtain unauthorized access to the computers and computer networks of MSPs (managed service providers) for businesses and governments around the world.” MSPs are suppliers who remotely manage client information technology (IT) infrastructure. An especially important type of supplier, MSPs frequently have privileged access to their clients’ IT systems and data in ways similar to or even exceeding that held by internal IT department employees.
The DOJ indictment continued, noting the attackers targeted the MSPs not to steal their information, but to gain access to their clients around the world. According to the indictment, the attackers sought unauthorized access to the intellectual property and confidential business data of victim companies in at least 12 countries through the MSPs. Let that sink in for a moment. Your own company’s cybersecurity efforts may be top-notch, but how are your managed service providers managing their cybersecurity? At this point, you may even be asking more fundamental questions such as, “How many managed service providers do I have?” – and rightfully so.
Team Telecom and National Security Concerns
While these questions are relevant for businesses in many industries, they become critical in situations where the U.S. government reviews your business through a national security lens. After all, December’s indictment directly connects the attackers and the hacking group to the Chinese Ministry of State Security. Lest any doubt remain that MSP security is a U.S. government priority, the Director of the Defense Criminal Investigative Service, Dermot F. O’Reilly, was direct: “The theft of sensitive defense technology and cyber intrusions are major national security concerns.”
National security interest in a given business manifests through several regulatory programs. Frequently, these programs focus on those businesses directly involved in national security matters. For example, the National Industrial Security Program focuses on contractors assisting with classified work. The Committee on Foreign Investment in the United States (CFIUS) and the informal working group known as Team Telecom, however, extend their inquiries beyond businesses engaged in national security work to include businesses in many sectors who share a common characteristic: foreign investment.
CFIUS reviews foreign investment into the United States for national security concerns. Its lesser-known sister process reviews certain Federal Communications Commission (FCC) licenses involving similar risks. The FCC defers to the expertise of the executive branch regarding national security, public safety and law enforcement concerns associated with foreign license applications. The executive branch conducts its reviews of these applications through the informal Team Telecom working group.
While CFIUS and Team Telecom are similar in their focus on national security, the prevalence and critical roles of MSPs in telecommunications make Team Telecom an especially important context for this type of risk. In fact, some Team Telecom risk mitigation agreements already give the government the opportunity to object to third-party providers, including MSPs, who may access sensitive information or classified information, as defined in the agreement. We can reasonably expect Team Telecom to increase its scrutiny of a carrier’s MSP arrangements based on the spotlight the December indictment shines on the issue. Signaling an effort to significantly raise awareness of this threat, the U.S. Department of Homeland Security’s (DHS) Cybersecurity and Infrastructure Security Agency (CISA) presented not one, but two webinars on China’s targeting of MSPs in February 2019.
Cost-Effectively Managing MSP Risk
Imagine a scenario where Team Telecom is reviewing your FCC license application. In your response to Team Telecom’s triage questions, you present your own cybersecurity procedures to demonstrate your ability to operate your network in a secure and trusted fashion. How do you effectively show, however, that your MSPs, who may also be empowered with access to the very same network, are equally as diligent? Alternatively, imagine that you are already subject to a Team Telecom risk mitigation agreement and the government shared generalized concerns about your management of the MSP risk. What evidence can you present that demonstrates the cybersecurity posture of your MSPs and your ongoing risk management activities regarding this third-party risk?
In response, you may be able to present vendor policies that outline robust controls for vendor access and activity on your network. While helpful, those policies only partially answer the question as their underlying assumption is that the MSPs themselves have not been compromised. Your MSPs may be abiding by the rules when accessing your network, but how secure are their networks? You could certainly require an onsite cybersecurity audit for your MSPs, but that approach becomes prohibitively expensive very quickly. As an additional disadvantage, that approach runs the risk of creating an adversarial relationship with your MSPs instead of a collaborative one.
Now, imagine an entirely different approach: a scalable, quantitative assessment of the cybersecurity risks presented by each of your MSPs. Let’s ground that assessment in the foundation of technical controls from the National Institute of Standards and Technology (NIST) Cybersecurity Framework. You share the scores of each MSP with Team Telecom to demonstrate, using the government’s own standard, the specific risks associated with each MSP and the aggregate risk for your MSP portfolio. For those where an elevated risk causes concern, the assessment points directly to actionable remediation steps. Following the remediation and another run of the assessment, you share the improved score with Team Telecom, providing persuasive evidence that you are actively addressing the risks associated with MSPs. If the MSP cannot or does not remediate the issue sufficiently, you have the data you need to inform a business decision regarding replacing that service provider altogether. CyberClarity360TM from Kroll and its parent company, Duff & Phelps, is the tool that enables this approach.
The Solution: CyberClarity360TM
CyberClarity360TM, a purpose-built software as a service (SaaS) tool from Duff & Phelps, enables you to quantify MSP risk in a scalable way. The results not only provide easy reporting and trend analysis, but they also support actionable risk management for your organization, regardless of the amount, type or role of your third-party vendors.
In addition to assessing technical security controls against the NIST Cybersecurity Framework, CyberClarity360TM offers unique insights into geopolitical challenges, insider threats, privacy and other non-technical risks. Assessment distribution, collection, validation, scoring, compliance analysis and collection of supporting documentary evidence are all completely automated.
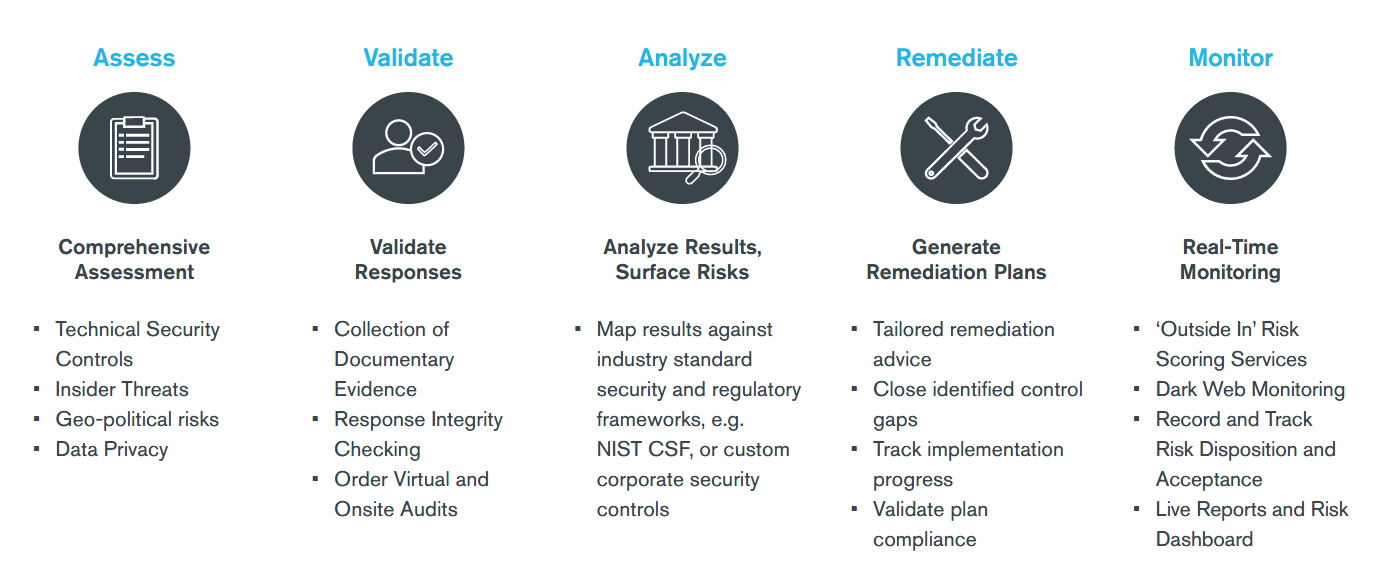
CyberClarity360TM leverages industry best practices to enable range and velocity for your team’s third-party assessment program, all with centralized reporting and documentation.
The tool works by presenting vendors a battery of multiple-choice questions mapped to comprehensive cybersecurity controls. After the vendor answers the questions, the CyberClarity360TM engine applies several verification and validation methods to help ensure accuracy. Throughout the process, you enjoy real-time insight into the progress of each vendor’s assessments through the CyberClarity360TM Corporate Portal.
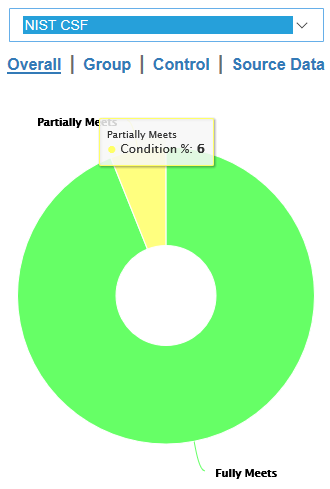
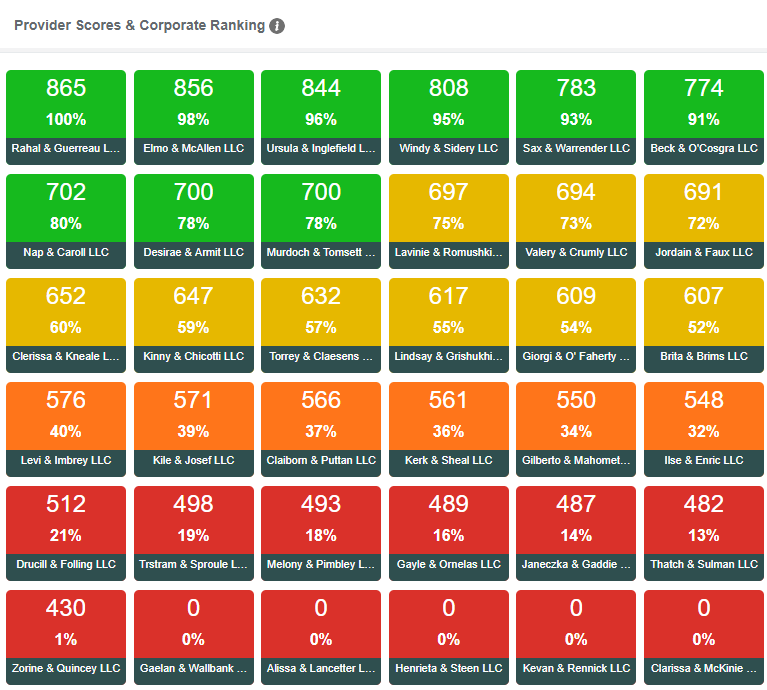
The portal presents its results of all the MSP assessments using a straightforward, color-coded dashboard with each tile representing a vendor. Clicking into each tile reveals the specific security controls contributing to the scores, immediately highlighting opportunities for remediation.
For carriers and operators who do not prefer the NIST Cybersecurity Framework, CyberClarity360TM maps its findings back to other security controls and frameworks, including:
- Center for Internet Security Critical Security Controls (CIS CSC)
- Information Systems Audit and Control Association (ISACA) Control Objectives for Information and Related Technology (COBIT)
- American National Standards Institute (ANSI)/International Society of Automation (ISA) 62443-2-1-2009 (99.02.01) – “Security for Industrial Automation and Control Systems: Establishing an Industrial Automation and Control Systems Security Program”; ANSI/ISA 62443-3-3-2013 (99.03.03) – “Security for Industrial Automation and Control Systems Part 3-3: System security requirements and security levels”
- International Organization for Standardization ISO/IEC 27001:2013 – “Information security management systems requirements”
- NIST Special Publication 800-53, Revision 4 – “Security and Privacy Controls for Federal Information Systems and Organizations”
CyberClarity360TM in an Undersea Cable Context
Telecommunications providers in diverse situations leverage MSPs, but undersea cable system operators offer a tangible, clearly relevant example due to the considerable interest Team Telecom shows in these licenses. Reinforcing this interest and specifically applying it to MSPs, DHS’s 2017 Threats to Undersea Cable Communications highlights the risks associated with vendors, characterizing their involvement as potential “supply chain insider threats.”
An undersea cable system operator may utilize dozens of vendors in their normal course of business, starting with the vendor who may own and operate their cable landing stations. A different vendor altogether may staff and manage their primary network operations center (NOC). Another vendor may operate a secondary NOC. The vendor for the cable’s network management system (NMS) may or may not have access to the NMS depending on their business arrangements.
These and other vendors have a variety of roles and access, and the cable system operator may maintain an internal inherent risk register based on the extent of the vendor and MSP roles. Unfortunately, this limited understanding of the inherent risk associated with MSPs does not readily lend itself to sharing with Team Telecom during the review of the license application. Furthermore, the operator has no easily repeatable process for documenting and reporting on the evaluation of MSP risks over the service life of the cable system, throughout which Team Telecom will be monitoring the operator’s compliance with the mitigation agreement.
Deploying CyberClarity360TM, the cable system operator quickly achieves an understanding of each vendor’s cybersecurity posture as it relates to the NIST Cybersecurity Framework. The tool presents that understanding in an easily-digestible dashboard, which the operator can share with Team Telecom as persuasive evidence of its MSP risk management program. Armed with this understanding, the system operator can recommend remediation actions and implement internal compensating controls to manage its MSP risks. Following the remediation, a repeat of the CyberClarity360TM assessment quantitatively and visually documents improvement in the MSP risks. By folding these iterative assessment results into their annual report to Team Telecom, the cable operator establishes a record of demonstrating consistent improvement over time.
In this scenario, and virtually any other involving substantial Team Telecom mitigation, CyberClarity360TM helps the operator achieve two critical business goals: managing the risks associated with MSPs and building a strong compliance record with Team Telecom.
Conclusion
Cybersecurity challenges remain among the most difficult risks for businesses to effectively manage. Once third parties become part of the equation, the complexity grows exponentially and quickly exceeds the capacity of individuals or even dedicated teams. By creating a purpose-built technology solution, CyberClarity360TM, Kroll has delivered an industry-leading solution to one of the most pressing areas of Team Telecom concern. Contact us today to learn more about how Kroll can help implement, mature or scale your third-party risk management program.
Stay Ahead with Kroll
Cyber Risk Assessments
Kroll's cyber risk assessments deliver actionable recommendations to improve security, using industry best practices & the best technology available.
Supply Chain Investigations
Creating a detailed portrait of a supplier’s financial stability, operations, compliance and culture.