Kroll has investigated many different tactics that threat actors use to steal consumer data on e-commerce sites. These types of attacks can be especially damaging for organizations that are responsible for storing customers’ personal and financial information that is collected during transactions.
What is Magecart?
Magecart is one of the most long-lived and persistent threat actor groups plaguing businesses. Technically, Magecart refers to the multiple cybercriminal groups known to exploit vulnerabilities within Magento e-commerce panels to steal payment card data, personally identifiable information (PII) or credentials through online skimming.
Many of Magecart’s methods involve injecting malicious code into e-commerce checkout pages to steal credentials or modifying paths to checkout pages that lead users to enter their payment information on a fake checkout form.
Evolution of Magecart Attacks
Since the first Magecart attacks made headlines back in 2010, the group have diversified, originally targeting only vulnerabilities in the Magento platform and selling data only on the dark web, before spreading to other e-commerce platforms and third-party services.
Moreover, the attacks themselves have become more technically diverse, relying on sophisticated obfuscation techniques that hide malicious code behind seemingly legitimate domains, or even image metadata. As e-commerce has expanded, so has the Magecart’s ingenuity.
High profile attacks against brands like British Airways and ticketmaster have catapulted Magecart into public consciousness. Come 2024, Magecart attacks continue to operate, exploiting backend systems and third-party dependencies to inject malicious code and siphon off payment information, albeit with a lower frequency.
How Magecart Attacks Work: Example Tactics, Techniques and Procedures
Kroll experts have observed one Magecart tactic where attackers inject malicious skimmer code via image files. The malware is designed to mimic a “favicon,” also known as a favorite or shortcut icon, which actors used to modify a file path that leads to a fake .png"noopener noreferrer" href="http://www.riskiq.com/blog/labs/magecart-adverline/" target="_blank">pooling IP addresses to reduce the risk of threat actor-controlled servers being be taken down. Actors have also used persistent skimming attacks that include running a hidden system process to restore skimmer code to a compromised e-commerce site after being already discovered and removed.
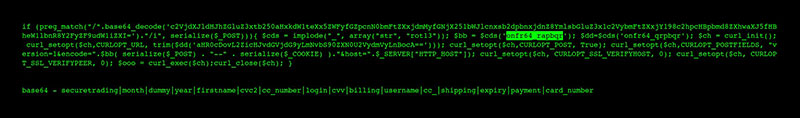
Figure 1 – Example of a threat actor tagging and exfiltrating data
Best Practices and Mitigation
- In August 2021, updates were released for Magento Commerce and Magento Open Source edition platforms that fixes 26 known vulnerabilities. Magento site administrators are advised to install these and any subsequent updates as soon as possible. Unlike most applications, Magento updates must be installed cumulatively in sequential order, rather than updating to the most recent update or patch.
- Magento store administrators should complete regular auditing of third-party e-commerce code, including code from online advertising vendors. Administrators are also advised to host third-party scripts on their own infrastructure to minimize the risk of a third-party compromise which can be leveraged against their web stores. Additionally, Magento administrators should implement multifactor authentication (MFA) in front of their admin panels. This can include a password coupled with a token, card, key, PIN or biometrics, which will greatly decrease the likelihood of unauthorized access.
- Administrators should implement a Content Security Policy (CSP) header on their web stores. This is an HTTP response header that enhances the security of a website and allows administrators to set restrictions on how certain browser resources are used, including JavaScript and CSS. With a CSP, administrators can also implement an allowlist of trusted and validated network locations, which helps to prevent data exfiltration if an e-commerce business is compromised in a Magecart attack.
- End-users can protect themselves against digital skimming attacks by assuring that they perform online shopping from a secure network, preferably using a VPN, and avoid shopping while connected to public Wi-Fi networks. Users should also avoid saving payment information in web browsers, assure that they are shopping from trusted businesses and check for “https” within the site URL before making an online purchase.
Magecart Attack Patterns
Kroll has seen a series of Magecart attacks where threat actors have written code that included cardholder data rights to a customer’s database. In these instances, customers were not able to detect any illicit activity within their site since the vast majority of the activity was happening within their own legitimate databases.
Kroll later observed threat actors using an existing web shell to query the database table they’d created, or set an auto exfiltration timer, such that any net new data would be re-queried at a set cadence, often daily or twice daily. This minimized the need for threat actors to return to victim environments and manually exfiltrate data, essentially creating a never-ending stream of fresh cardholder data.
How to Defend Against Magecart Attacks
Here are three important steps for protecting your e-commerce platform from Magecart attacks:
- Make sure MFA is enabled in front of any and every admin panel or content management system (CMS).
- Implement a hosted iFrame with a merchant acquirer to ensure transactions are secured.
- Regularly conduct test transactions to ensure that the iFrame is working as intended.
Securing your e-commerce platform is crucial to protecting yourself from Magecart attacks. Enabling MFA for every admin, implementing a hosted iFrame with a merchant acquirer, and regularly testing transactions can help keep your online store safe. For further guidance, contact one of our Kroll experts at one of our 24x7 cyber incident response hotlines or connect with us through our Contact Us page.
The article above was extracted from The Monitor newsletter, a monthly digest of Kroll’s global cyber risk case intake. The Monitor also includes an analysis of the month’s most popular threat types investigated by our cyber experts.
Magecart attacks represent a significant threat to businesses and consumers alike. By understanding how they work, businesses can better protect their data and their customers. Therefore, it’s important for businesses to prioritize cybersecurity. Talk to Kroll expert today and more ways to help anticipate, detect, mitigate and respond.
NewsletterSubscription
JSS component is missing React implementation. See the developer console for more information.
Stay Ahead with Kroll
Cyber and Data Resilience
Kroll merges elite security and data risk expertise with frontline intelligence from thousands of incident responses and regulatory compliance, financial crime and due diligence engagements to make our clients more cyber- resilient.
Payment Card Industry Services
Kroll offers a wide range of services for both merchants and payment processors, from audits to incident management services, to pragmatic approaches for strengthening your cyber defenses.
Malware and Advanced Persistent Threat Detection
Our expertise allows us to identify and analyze the scope and intent of advanced persistent threats to launch a targeted and effective response.
24x7 Incident Response
Kroll is the largest global IR provider with experienced responders who can handle the entire security incident lifecycle.