From February through the end of August, Kroll investigated over 100 cases of ransomware for clients across diverse industry sectors. Our findings are underscored by a variety of open- and closed-source reporting, including an August 2019 advisory by the Cybersecurity and Infrastructure Security Agency about the “rapid emergence of ransomware across our Nation’s networks.”
In August alone, Kroll observed seven different variants of ransomware, including newer arrivals such as Tflower and DoppelPaymer. Even Ryuk, the ransomware most often detected, has been characterized by multiple different strains and variants.
The increase in variants is making it more difficult for organizations, incident responders and law enforcement to triage ransomware cases. For example, decryptors for new variants may not become publicly available in a timely manner. Likewise, it may take time to produce case studies or anecdotal reporting on how or if threat actors will decrypt the data if the ransom is paid.
Ransomware on the Dark Web
Kroll intelligence analysts conclude that large-scale ransomware campaigns are often carried out by tightknit cyber-criminal groups, such as Indrik Spider1, that are motivated by profit. These groups will often operate on their own or are solicited to offer their ransomware as a service (RaaS) to paying customers. As a result, access to these pieces of ransomware is often very restricted and they are not typically offered for sale or for rent on the forums or peer-to-peer chat groups. However, once a group is done with a ransomware campaign, that source code is sometimes leaked, and new pieces of ransomware can be created out of that code.
The result of fewer large ransomware campaigns on forums and peer-to-peer chat applications has been a greater presence of smaller, lesser-known ransomware. Often this malware is developed by small groups or individuals looking to make a name for themselves within this specific community.
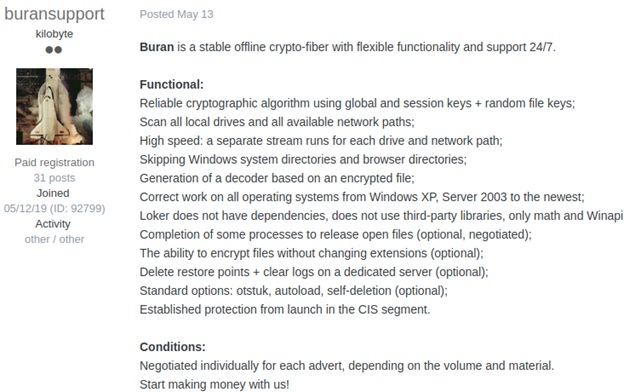
One example of this can be found on the top-tier Russian forum Exploit. The ransomware dubbed “Buran” has been offered for sale, with the seller claiming it will work on every version of Windows from XP to 10, encrypt files without changing extensions and delete restore points for the user. It is being sold for a few thousand dollars, and at the time of analysis, it does not appear any user has verified the effectiveness or validity of this specific Buran offering. Interestingly, no one has confirmed whether it is connected to the Buran ransomware strain that is currently reported to be spread via a RIG exploit kit.2
User advertising the "Buran" variant for sale in dark web forum
Ransomware Variants Observed in Kroll Engagements
Below is a list of ransomware (including any related variants) that Kroll has encountered year-to-date in the course of its investigations. Ryuk ransomware accounted for more than triple the number of incidents over the second most common type, Sodinokibi.

The full list includes:
| Dharma/CrySIS | Hermes | RobbinHood |
| DoppelPaymer | Matrix | Ryuk |
| Evil Locker | Mr.Dec | SamSam |
| GandCrab | Nozelesn | Snatch |
| GlobeImposter 2.0 | Phobos | Sodinokibi |
| WannaCry | Tflower |
Kroll Experts Corner – Best Practices for Ransomware Recovery
Hopefully, your organization will not become a victim of ransomware. However, preparing for the worst-case scenario can help you respond in a quicker, more deliberate manner and limit the impact on your operations. Scott Hanson, a senior vice president in our Cyber Risk practice, recommends that your IT personnel and management team discuss the following best practices now and be ready to implement them quickly in the event you become a victim. \
- Isolate and Disconnect: If a system within your environment is impacted, isolate it from other computers and servers within the network and disconnect from both wired and wireless networks.
- Identify the Infection: Ransomware typically identifies itself within the ransom note. If that is not done, numerous open-source sites such as No More Ransom and ID Ransomware may be able to help you identify what variant you have.
- Report the Incident: Incidents may be reported by contacting your local FBI field office or through the FBI Internet Crime Complaint Center. Information about ransomware attacks provides law enforcement with better understanding of the scope of the threat and helps them allocate resources toward ransomware research and investigations.
- Think Before You Pay: Paying a ransom is ultimately a business decision. Only the victim of a ransomware attack can measure the value of the data loss, the risk to their operations or business and the costs associated with paying versus not paying. Kroll is here to support you in that decision-making process. Whether it is restoring the network from backups or negotiating for a decryptor to restore the business, we can offer our expertise, experience and guidance. Your incident response plan should outline your stance and response to any cases of ransomware; also, if applicable, contact your cyber insurance carrier for any ransomware-related coverage.
- Retain log data: Preserving network and endpoint logs can make the difference between successful root-cause analysis and being left in the dark as to how the incident occurred. Because many log types roll off quickly, timely action is necessary to retain any potentially relevant event data for subsequent investigation.
- Restore Systems: Assuming your backups are still in place, you may choose to wipe your systems altogether and reinstall from safe backups. (For more best practices on backup policies and protocols, see the Kroll Monitor issue, Ryuk and the Resurgence of Ransomware.)
A well-thought-out incident response plan (IRP) is vital if you suffer a ransomware attack. An IRP that is tested on a regular basis will be the “battle plan” that coordinates all the parties enterprise-wide that are necessary to manage a ransomware attack: IT and InfoSec, finance, risk and business continuity, human resources and legal, as well as external partners such as insurers, legal counsel and investigative or forensics responders.
Arranging an incident response retainer with a highly experienced cyber security first responder such as Kroll, can provide additional peace of mind. Kroll offers three incident response retainer plans with no surprises. With our prepaid plans, Kroll lets you customize your retainer with a wide variety of industry-leading reactive and proactive services that ensure you maximize the value of your cyber security investment.
Sources
1.Malpedia entry, https://malpedia.caad.fkie.fraunhofer.de/actor/indrik_spider
2.“Meet Buran: The New Delphi Ransomware Delivered via RIG Exploit Kit”, Acronis website, https://www.acronis.com/en-us/blog/posts/meet-buran-new-delphi-ransomware-delivered-rig-exploit-kit
The article above was extracted from The Monitor newsletter, a monthly digest of Kroll’s global cyber risk case intake. The Monitor also includes an analysis of the month’s most popular threat types investigated by our cyber experts. Subscription is available below.
NewsletterSubscription
JSS component is missing React implementation. See the developer console for more information.
Stay Ahead with Kroll
Cyber and Data Resilience
Kroll merges elite security and data risk expertise with frontline intelligence from thousands of incident responses and regulatory compliance, financial crime and due diligence engagements to make our clients more cyber- resilient.
24x7 Incident Response
Kroll is the largest global IR provider with experienced responders who can handle the entire security incident lifecycle.
Malware and Advanced Persistent Threat Detection
Our expertise allows us to identify and analyze the scope and intent of advanced persistent threats to launch a targeted and effective response.
