In March, nearly one in five of all Kroll’s Cyber Risk engagements were insider threat incidents, most commonly affecting the healthcare and financial service industries. Kroll reviewed cases that involved former employees gaining unauthorized access to data, as well as current employees inadvertently exposing confidential data.
According to the New Jersey Cybercrime Communications and Integration Cell (NJCCIC), “Insider threats can include current or departing employees, contractors, third party vendors, technicians, business partners, and anyone granted administrator privileges. If organizations do not have the right preventative measures in place and management is not cognizant of the indicators of an insider threat, they are putting themselves at great risk.”
Insider threat incidents involving former employees are increasing as companies move proprietary information to cloud-based services. Departing employees with active credentials (their own or those of a co-worker) pose a threat to even the most secure networks, as the examples below highlight:
- In a recent incident covered in open source news reports, a disgruntled former employee at a UK-based firm stole a coworker’s credentials and deleted 23 of his former company’s cloud servers.
- A New Jersey woman stole trade secrets from her employer, posting the stolen material on the website of a Chinese subsidiary company, of which she was part owner. She admitted to accessing an internal company database and downloading information related to chemical compounds onto her employer-issued laptop. She then transferred the information to her personal home computer by sending it to her personal e-mail address or via a USB thumb drive.
Cases like these demonstrate the high-impact nature of some insider threat investigations. It is imperative that organizations deploy procedures to make it as difficult as possible for departing or disgruntled employees to have access to active credentials which can be used to exfiltrate sensitive data or access key internal systems.
Monetizing Insider Threats on the Dark Web
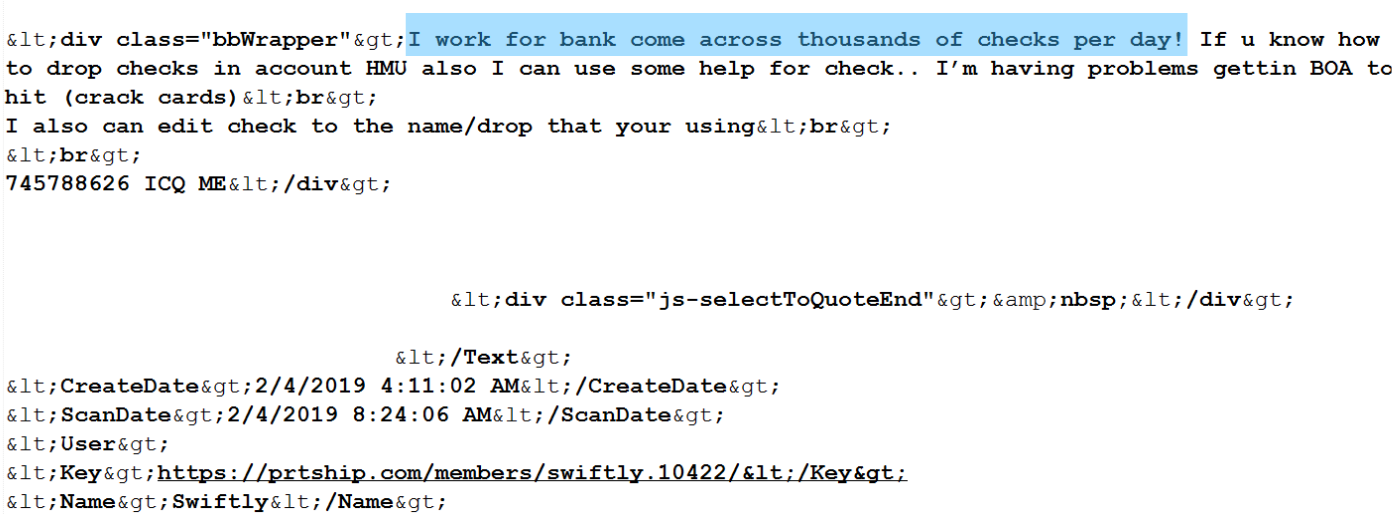
The screenshot below shows a possible insider threat actor advertising access to checks on hacker forum prtship.com, which could be evidence of a check fraud scheme involving a potential employee of the bank.
Kroll Experts Corner: Mitigating Insider Threats
Following are some insights from Kroll experts on how to prevent or more quickly detect data exposure caused by insiders.
- Don’t Let Your Business Outgrow Your Security
Businesses of all sizes need to carefully weigh their exposure, but quick-growing or complex enterprises can particularly find the team overdriving technology, leaving some gaping security holes. If your business is expanding or in the midst of other organizational changes, consider deploying technical resources (e.g., endpoint threat monitoring or third-party cyber risk management solutions) and dedicated in-house staff or contract with outside resources (such as a virtual CISO) to help keep your business safe. Significant changes in size, through organic growth or acquisition should be seen as a trigger to update your risk assessment. - Make Security Part of Workflows to Promote Sustainability
Assess how your employees really work and then use that knowledge to put in place the right rules, tools and compliance mechanisms. For example, in Kroll’s latest Global Fraud & Risk Report, security experts Alan Brill, John Friedlander, and Jonathan Fairtlough described how an organization could provide each outside salesperson with a tablet complete with paid cellular access. Customer data and forms are stored in a document management system in the cloud, and the tablet has mobile device management software that blocks all browsing. If lost, the device is encrypted and can be remotely wiped. No local storage, no vampire data or data hoarding. - Establish and Maintain Defensible Data Access Policies
For example, an “Acceptable Use of Information Technology Policy” should reflect and communicate rigorous controls the organization has established for employees and third parties regarding the proper use of its systems, data and resources. These can include practices such as requiring employees to use only company-approved devices and systems as well as restrictions on using social networking sites and non-corporate email on company devices. Of course, in setting these rules, you must be serious about compliance, as the rules represent what is in effect a promise of what you’re going to do to protect information. - When Employees Depart, Immediately Restrict Physical and Electronic Access
Preferably before an employee permanently leaves the premises, make sure to deactivate, disable or delete network account access (both local and remote), ID authentication tokens, security codes, email accounts and access cards. Because malicious insiders can leverage “forgotten access” to enterprise applications, the use of a single sign-on (SSO) solution can help close this gap. Also, try to determine if the individual would have access to the credentials of other employees and if so, re-set those as well. - Employ Technology That Can “look Beyond Your Borders” for at-risk Data
In professional circles, it is common knowledge that for some industries, engineers and others are using chat rooms on the dark web to specifically sell and buy intellectual property and trade secrets. Sophisticated solutions such as Kroll’s CyberDetectER® DarkWeb continuously monitors this activity and acts as an early warning system that sensitive proprietary data could be compromised.
More best practices to address insider threats, by Senior Managing Director Alan Brill:
- Set the tone from the top and promote a corporate culture where “cybersecurity is everyone’s responsibility.”
- Apply the principle of least privilege: Limit network access to those who need it for their jobs.
- Restrict the use of removable media.
- Integrate checks of cybersecurity program elements into your internal audit and compliance programs to assure that they are working as intended.
- Consider data loss prevention (DLP) processes designed to prevent data loss holistically, including DLP products, company policies, user training, internal reviews, and more.
- Watch for early warning indicators that include remote access during off-hours, unexplained exporting of large amounts of data and never taking a vacation.
- Regularly scan your network and generate an automated inventory of all IoT devices that are connected. Investigate any entries that cannot be accounted for to ensure no “mystery” devices are attached to your network
Get the Latest Trends and Insights from Kroll In Your Inbox
Sign up for The Monitor and every month you’ll gain access to exclusive cyber threat trends derived from Kroll’s global case intake, along with tailored recommendations and examples from our threat intelligence experts.
The article above was extracted from The Monitor newsletter, a monthly digest of Kroll’s global cyber risk case intake. The Monitor also includes an analysis of the month’s most popular threat types investigated by our cyber experts. Subscription is available below.
NewsletterSubscription
JSS component is missing React implementation. See the developer console for more information.
Stay Ahead with Kroll
Cyber and Data Resilience
Kroll merges elite security and data risk expertise with frontline intelligence from thousands of incident responses and regulatory compliance, financial crime and due diligence engagements to make our clients more cyber- resilient.