Free Template: MITRE ATT&CK Detection Maturity Assessment & Guide
The threat landscape has evolved rapidly in recent years due to major changes in the way organizations operate and adopt new technologies. Cloud services such as Software-as-a-Service (SaaS) and Infrastructure-as-a-Service (IaaS) have seen massive growth over the last decade. With accelerated digital transformation, increased remote working and cloud adoption, the attack surface has increased for most organizations. Threats are also increasing as innovations like generative AI emerge, creating opportunities for threat actors if not secured properly.
As a result, the most prevalent attack types we see today, as highlighted in our latest Kroll threat landscape report , are ransomware, which encrypts data for ransom, and business email compromise, which tricks users into processing unauthorized payments. Defenders must focus on resilience against these dominant threats, but they also cannot lose sight of securing new attack vectors such as AI and a diversifying supply chain. The threat landscape continues to evolve rapidly so organizations must maintain vigilance and proactively identify and mitigate emerging risks through threat intelligence, data analysis and continuous security improvements. However, this can be a daunting prospect.
MITRE ATT&CK® is a global knowledge base of adversary tactics and techniques drawn from real-world observations. It provides a common language for security teams to communicate in relation to threats and shares a range of use cases. In this article, we will outline a lightweight, programmatic approach to performing a maturity assessment using free MITRE tools (like ATT&CK framework, D3FEND, and MITRE Centre for Threat Informed Defense (CTID)) to provide a starting point for you to understand your organization’s coverage against the framework, identify areas for improvement and prioritize them for implementation.
To accompany this article, our Kroll Cyber Risk experts have created a template which adopts the same five-step process as described below. You can complete it as you go through the article. As a part of this article, we will be leveraging the MITRE ATT&CK framework and ATT&CK navigator tool to interpret the result. The ATT&CK navigator has been replicated in the template to give users similar outputs as depicted in this article.
Download the Kroll MITRE Cyber Maturity Review Template

How to Use the MITRE ATT&CK Detection Maturity Assessment Tool
We will follow a five-step process as shown below:
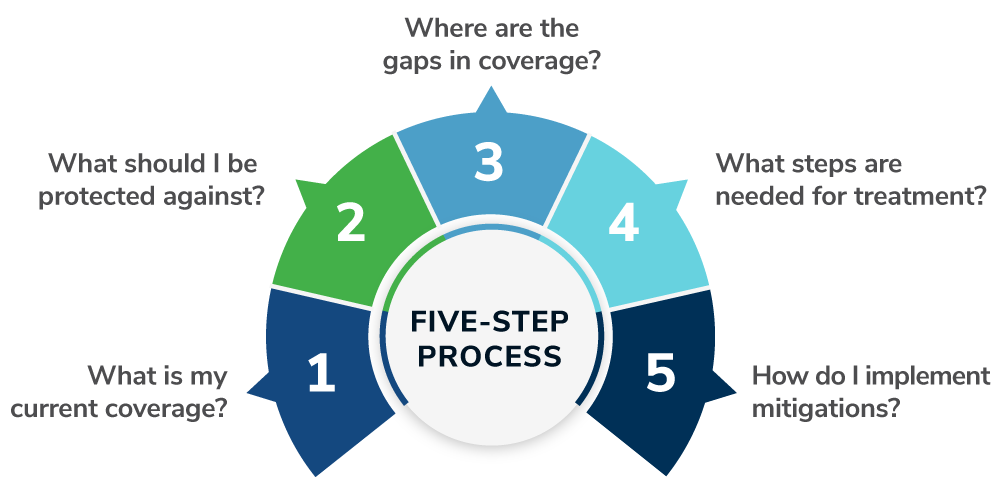
Step 1: What is My Current Coverage?
The first step is to review your existing security solutions and create a baseline of your current security controls. We recommend using MITRE ATT&CK to determine this as it provides a common taxonomy to map your technical controls to. There are a number of ways to begin this process. Below are a few recommendations to get you started:
Option 1a: Many organizations have already invested in defensive technology, either in the cloud or on-premises. With MITRE ATT&CK becoming the de facto language for how we communicate, analyze and attribute adversary activity, most vendors now map their alerts and detections to this framework. Ask your security solution vendors to share their coverage against MITRE for the tools that you have already invested in.
Option 1b: MITRE’s Centre for Threat Informed Defense (CTID) has also done some great work in mapping cloud security controls to the ATT&CK framework. If you leverage any of these tools, use these maps to build a view of your current coverage in MITRE ATT&CK:
As an example, if you were using Azure AD, Azure Firewall and Azure Key Vault, the coverage on the ATT&CK framework would resemble the image below:
Option 1c: Ask your Managed Detection and Response (MDR) provider to share their coverage for the infrastructure and security devices that are under their monitoring scope. For example, with our MDR service, Kroll Responder, we map all our detections to the MITRE ATT&CK framework, share a view of the current coverage and suggest future improvements to this coverage.
Option 1d: Use MITRE mitigations to map the coverage you already have based on some of the mitigations that your organization might have already implemented. This could be MFA, network-based intrusion detection systems, user awareness training, vulnerability scanning or software patching. Add the TTPs covered by implementing these mitigations into the map to understand the coverage gained by implementing these controls.
It is important to understand the scope of the implemented mitigation control. Be sure that the mitigation controls you are including in your scope of coverage are applicable holistically across your organization and not just to a siloed scope. For example, often Kroll engages in incident response support for clients who have appropriate EDR tooling deployed to their endpoints, however, the compromised assets are the "few exceptional" assets which fell short of those controls.
Option 1e: Leverage MITRE D3fend to understand the coverage your existing security tools offer; then map this coverage to offensive techniques that can be detected using MITRE ATT&CK.
Combine all the maps from Step 1a, 1b, 1c, 1d and 1e to map your current coverage against the ATT&CK Framework. By the end of this step, you should have a view of your current coverage against the framework. The image below shows a preview of how the coverage looks for the steps just completed. If you are using the tool, you should be able to see a similar view in the Step1-ATT&CK-CurrentCoverage sheet of the workbook.
Step 2: What Should I Be Protected Against?
In this step, we will identify the high-priority TTPs that should be covered by your organization. This requires a good understanding of the threats against your organization. There are a number of ways to begin this process. Below are a few recommendations to get you started.
Option 2a: Ask your security team the following questions:
- What is the most common threat we face?
- Which threat actor group is likely to attack us?
- Are there any TTPs that we should prioritize for detection?
Once you have the answers to these questions, use them to prioritize the TTPs that are not currently covered. If you don’t know the answers to these questions, the ATT&CK framework can still provide insights. Read on to learn how MITRE ATT&CK can help with some of these responses.
Option 2b: Use the TTPs based on threat actor groups. MITRE tracks more than 130 threat actor groups here. From this point, you can filter out the threat actor that might be applicable to your organization based on the industry of operation. For example, if you choose to filter down based on “Manufacturing” as the industry of operation, you will now be presented with all the threat actors that have been known to attack the manufacturing sector. Select the threat actor/s most applicable to your organization to identify the key TTPs applicable to that threat actor. Let’s say for example, we want to analyze for Lapsus$ (G1004) and Threat Group-3390 (G0027), the image below shows the results that might come up.
Option 2c: MITRE also tracks campaigns here. If you believe you are likely to be a part of a threat actor campaign, use the one most applicable to your organization.
Option 2d: MITRE Top 10 is another project from CTID that allows you to identify the top 10 TTPs your organization should aim to prioritize in order to prevent ransomware attacks. Use the tool to create a customized list of top 10 techniques that might be applicable to your organization. The tool is available here.
Option 2e: Use frameworks like NIST to identify key priority areas. CTID has also mapped the NIST framework to ATT&CK. This allows you to identify TTPs that can be covered by specific Control IDs. You can prioritize the TTPs required for coverage based on the control IDs you’re looking to implement.
Option 2f: Research for threats that might be applicable to your organization. Lockbit has been known to target the manufacturing sector in the past, and the CISA has published this detailed report that gives valuable insight into the TTPs it uses. Kroll publishes regular threat intelligence reports that are available to view and download here. Other useful sources on the latest threats include CERT-EU, SANS Internet Storm Center, Homeland Security and NCSC Twitter.
By the end of this step, you should have a list of the TTPs you are looking to cover as a part of your ongoing security improvement plan. For the purposes of this illustration, we will continue to use the version we created in Step 1b. If you are using the tool, you should be able to see a similar view in the Step2-ATT&CK-KeyTTPs sheet of the workbook.
Download the Kroll MITRE Cyber Maturity Review Template
Step 3: Where Are the Gaps in Coverage?
Overlay the TTPs identified in Step 1 and Step 2. This stage is crucial for gaining a view of the gaps that exist within the current coverage and the ones you should prioritize for mitigation.
The techniques marked in red in the graph above are those that are not currently covered, which might be important for your organization to protect against. If you are using the tool, you should be able to see a similar view in the Step3-ATT&CK-GapinCoverage sheet of the workbook.
Step 4: What Steps Are Needed for Treatment?
Now that you have identified the gap in your coverage, the next step is to identify how they will be added to your coverage. You can choose to take one of the three actions for the TTPs that you have identified for coverage:
- Create a new detection
- Invest in technology
- Risk accepted
Create a new detection: Creating a new detection can, in many cases, offers a simple, yet effective solution for organizations. However, new detections can often create a false-positive alerts, so be mindful about tuning them to ensure that you can still detect malicious behavior without overwhelming your team with false-positive detections or “noise”.
If you have an MDR provider, work with the provider to understand the effectiveness of covering the TTPs via custom detection rules. For example, as a part of our Kroll Responder MDR service, our dedicated Detection Engineering team supports the creation of bespoke detections for our clients. We also provide them with a technical account manager to support them in maturing their MDR coverage over time. We work with our clients to continuously improve their coverage for threat detection via either bespoke detection or recommendations on improvements.
MITRE D3fend can help to identify appropriate detection and mitigation methods. Search the technique name in the D3fend database to gain a view of available options for detection. Pivot into the detection logic and other valuable insights from there.
Invest in Technology: More specifically, investing in technology to provide this mitigation. In such cases, look at the overall coverage offered by this tool (defense in depth). From the identified TTPs, there may be some that can be mitigated by implementing a new technology but the cost of implementing the tool may be high. Think of these TTPs as part of the attack chain instead of them being standalone to understand if the additional investment is worth it. Alternatively, you could also undertake a red team exercise to determine the likelihood of occurrence based on the security controls you have and to identify new TTPs that you may not have considered.
Risk Accepted: Risk acceptance is where you accept the risks posed to the organization by not covering the TTPs that are identified. Sometimes the cost of implementing a detection or new technology outweighs the value this mitigation step provides to the organization. In these types of scenarios, weigh up your options for risk mitigation.
Step 5: How Do I Implement Mitigations?
In this step, you will implement one of the treatment plans outlined above. Once the mitigation is in place, update your ATT&CK coverage to reflect the latest enhancements (let’s say you implemented two controls to cover three additional TTPs). Create a renewed ATT&CK MAP to visualize the impact of implementing additional TTPs, then document the changes and repeat the process again. If you are following the free template we provided, the ATT&CK-Renewed coverage tab will provide this view. If you are using the tool, you should be able to see a similar view in the Step5-ATT&CK-RenewedCoverage sheet of the workbook.
When using this approach, keep in mind some key caveats:
- While MITRE offers an excellent knowledge base for offensive techniques (MITRE ATT&CK) and maps those to relevant defensive techniques (D3FEND), it is not an exhaustive list. Because threat actors continuously evolve, it is important to understand the latest behaviors and adapt your defensive strategy to counter them. Kroll has vast expertise in this area drawn from 3,000+ incident response engagements around the world. Kroll also publishes regular threat intelligence reports that highlight these changing behaviours as observed by our incident responders. Subscribe here to stay updated.
- Can you achieve 100% coverage? For most organizations, 100% coverage against the MITRE ATT&CK may never be possible. Use ATT&CK as a guide to understand your current coverage, as well as gaps in your coverage. Use the above methodology to prioritize the TTPs you are looking to cover, then come up with a mitigation plan.
- Avoid tracking adversary behaviour as specific actions; instead, look to understand the common sequence of TTPs that the threat actor might use and build your detections against them. It is important to understand the context of a particular technique used by the actor in order to be able to build effective detections.
Advancing Threat Detection: Next Steps
As this overview shows, MITRE offers several tools readily available to help organizations create a plan for security maturity. By using these alongside our template, organizations can gain a valuable starting point for identifying key areas for improvement and prioritizing them for implementation. However, while the ATT&CK maps offer a notional view of the defense in your organization, it is important to continuously test, monitor and update these controls to ensure they are being protected in order to adapt effectively to the ever-changing attack landscape.
In addition to the process outlined here, it is important to consider a more comprehensive process of continuously improving your cyber defense by identifying your priority threat exposures, testing the effectiveness of your controls against real-world scenarios and addressing any missing detections, response playbooks, security configurations or policies. For example, Kroll’s Security Validation services combine automated and practitioner-led testing using TTPs gained from our unrivalled exposure to 3,000+ incident response cases a year, 80 million+ indicators of compromise from our adversary intelligence, and our existing MDR clients’ use cases to bring bespoke simulations to our clients’ environments. We then leverage our purple teaming expertise (the collaborative efforts of our Detection Engineering, Offensive Security and Threat Intelligence teams) to build new detections, mitigations (automated and manual processes) and policy changes.
Contact us to learn more about how we help organizations continuously identify and address gaps in their cyber maturity.
Stay Ahead with Kroll
Cyber and Data Resilience
Kroll merges elite security and data risk expertise with frontline intelligence from thousands of incident responses and regulatory compliance, financial crime and due diligence engagements to make our clients more cyber- resilient.
Threat Exposure Management
Kroll’s field-proven cyber security assessment and testing solutions help identify, evaluate and prioritize risks to people, data, operations and technologies worldwide.
Kroll Responder MDR
Stop cyberattacks. Kroll Responder managed detection and response is fueled by seasoned IR experts and frontline threat intelligence to deliver unrivaled response.





