Why is CVE-2020-0688 so Critical?
We asked Kroll experts Jeff Macko and Sam Smoker about this vulnerability, and why organizations must urgently patch it:
- This vulnerability permits an attacker to run any code of their choosing as SYSTEM, the highest level of security on a windows system.
- Depending on the network configuration, it may permit an attacker to pivot into the internal network and access additional hosts.
- CVE-2020-0688 would likely permit an attacker to read, alter or send email on behalf of any user.
- Organizations that allow off-network access to Outlook Web App (OWA) only are still vulnerable to this because the vulnerability is in Exchange Control Panel (ECP), one of its web components.
- This vulnerability will be useful to actor groups, such as those aligned with nation-states, that have a trove of credentials from past breaches or phishing but no way to leverage those credentials against organizations due to measures like multi-factor authentication for VPN access. However, if the organization has not patched this vulnerability, all criminals would need is one valid username and password.
- Exchange service accounts typically have very high privileges in Active Directory. An attacker that has gained an initial foothold but with an account that lacks local admin permissions can now pivot to SYSTEM on any vulnerable Exchange servers where the user has a mailbox, and depending on the server configurations, quickly scrape credentials to escalate to domain or enterprise admin.
Deep and Dark Web References to Remote Code Execution Vulnerability
On March 2, Kroll analysts noted that the user @cryptomaniac on the forum Exploit was seeking to buy ready-made exploits for the vlunerability.1 One day later, a user on Raidforums supplied a Github link to exploits and detect tools for CVE-2020-0688.2
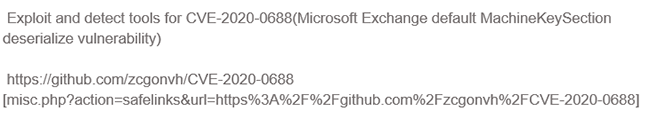
Figure 1 - On March 3, a User on Raidforums Posts a Link to Exploits for CVE-2020-0688
Metasploit Integration Renews Warnings to Patch
When the MS Exchange RCE exploit was integrated into Metasploit on March 3, more attention was directed to the criticality of the vulnerability. This was followed by calls for action to patch more widely and efforts to increase awareness about the availability of exploits.
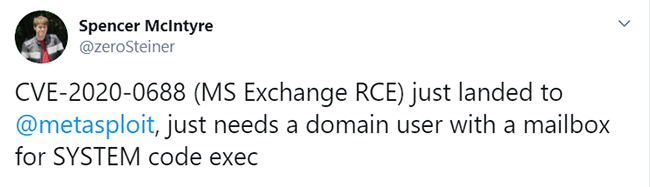
Figure 2 - A Tweet from March 3 Referencing a Github Link to the Metasploit Exploit
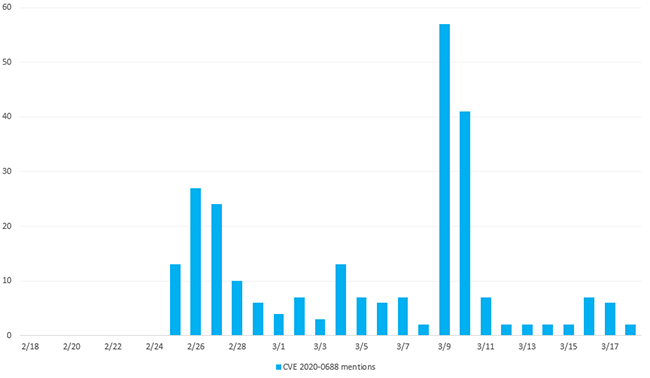
Figure 3 - Mentions of CVE-2020-0688 Spiked on March 9 (Source: Silobreaker)
APT Groups Actively Seeking to Exploit Vulnerability
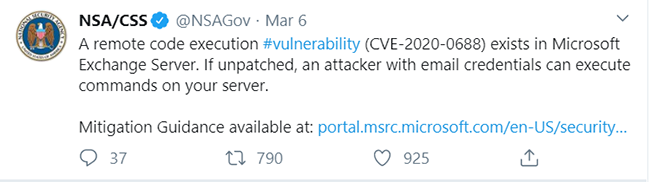
As multiple APT groups raced to exploit the unptached instances of CVE-2020-0688, the National Security Agency (NSA) posted a warning on its Twitter account reminding organizations to patch the flaw as quickly as possible.
The European Union CERT released a report on March 10 noting that multiple state-backed hacking groups were trying to exploit the REC-vulnerability CVE-2020-0688. The Department of Homeland Security (DHS) reiterated by stating, “Multiple APT hacking groups are actively targeting unpatched Microsoft exchange server flaws…if successful, an attacker could remotely install code with elevated privileges.3
Kroll advises clients to follow the mitigation procedures provided by Microsoft and to patch accordingly. Kroll is providing incident response services to affected organizations and will continue to monitor the deep and dark web and open sources for new exploits against CVE-2020-0688.
Sources
1 Web site; Exploit forum; URL : exploit.in ; 2 Mar 2020 ; accessed on 17 Mar 2020.
2 Web site; Raidforums; URL: hxxps://raidforums.com; 3 March 2020; accessed on 17 Mar 2020.
3 Web site; CERT EU; URL: hxxps://cert.europa.eu ; 12 Mar 2020 ; accessed on 17 Mar 2020.
The critical Microsoft Exchange Remote Code Execution (RCE) vulnerability labeled as CVE-2020-0688 was released by Microsoft on February 11, but it's gaining renewed attention after a Metasploit module was introduced on March 3. According to Microsoft, “a remote code execution vulnerability exists in Microsoft Exchange Server when the server fails to properly create unique keys at install time.” Reports are now spreading widely about nation state actors scanning for the vulnerability to leverage attacks. Exploits for the vulnerability were available in early March, and deep and dark web forum users were actively seeking to capitalize on available exploits. In mid-March, a Metasploit integration created a renewed sense of urgency to implement patches for the vulnerability, with warnings from government agencies to patch as soon as possible.
Watch our video for Remote Work Security Assessment – Safer WFH Environments
Stay Ahead with Kroll
Cyber and Data Resilience
Kroll merges elite security and data risk expertise with frontline intelligence from thousands of incident responses and regulatory compliance, financial crime and due diligence engagements to make our clients more cyber- resilient.
Cyber Vulnerability Assessment
Proactively identify vulnerable systems and devices that may be exploited by an attacker or malicious software, often resulting in data loss or breach.
Office 365 Security, Forensics and Incident Response
Digital forensic experts investigate hundreds of Office 365 incidents per year and help strengthen your security.
Computer Forensics
Kroll's computer forensics experts ensure that no digital evidence is overlooked and assist at any stage of an investigation or litigation, regardless of the number or location of data sources.
24x7 Incident Response
Kroll is the largest global IR provider with experienced responders who can handle the entire security incident lifecycle.