At a time of year when consumers and organizations want to give back, cybercriminals seek to exploit that generosity with cyber scams.
The Cybersecurity and Infrastructure Security Agency (CISA) recently warned consumers to be vigilant when browsing or shopping online, noting that predicted attack vectors for the upcoming holiday season include phishing emails with “ecards containing malicious links” or “spoofed emails requesting support for fraudulent charities or causes”.
Phishing emails are a common way for bad actors to get into an organization’s infrastructure. Employees who think they are clicking on a link to give money to a charity or download a holiday card may open the door for a bad actor to compromise an email account for fraud or leave behind a banking trojan like Emotet, which can be used by cybercriminals to steal credentials and deploy a ransomware attack.
According to the Anti-Phishing Working Group, the number of phishing attacks observed in the third quarter of 2019 rose to a level not seen since late 2016, demonstrating that phishing attacks are still a common and effective tool in a cybercriminal’s playbook. This statistic correlates with what Kroll, a division of Duff & Phelps, sees within its incident response intake process. Email compromises, the majority of which start with a phish, currently account for approximately 40% of reported incidents, making it the most commonly observed threat type so far in 2019.
Phishing for Donations
Common phishing scams this holiday season could be emails seeking donations for fraudulent or fake charities. “We live in a time when any incident that can lead people to exercise charitable feelings is attractive to cybercriminals,” notes Kroll Senior Managing Director, Alan Brill. For instance, after the Notre Dame Cathedral fire in April, scammers created phony fundraisers on crowdsourced funding sites and fake websites within hours of the actual event. Brill notes that such fake pages are “easy” for criminals to create. In addition, he observes that recent limitations put on the access to internet WHOIS information because of the EU’s General Data Protection Regulation (GDPR), make it “almost impossible for the average consumer to know if a site was established by a recognized organization or criminal.”
Brill further comments that “combining charitable feelings during the holiday period with the increased difficulty for an individual to validate purported charitable sites makes this a happy time of year for cybercriminals.”
In underground markets and chat platforms where cybercriminals advertise their services, Kroll frequently observes vendors offering services to facilitate phishing attacks. Some vendors offer targeted phishing exploits, for example, a page that is already configured to look like a trusted organization. Others offer phishing tutorials, instructing others how to carry out a phishing attack, such as this one on underground market DarkBay offering to show buyers “How to Make a Phisher For a Website.” In encrypted chat applications such as Telegram and Wikr, criminals offer “hacking tuition” services on how to commit SQL injections and phishing attacks. At that time of analysis, many of these vendors are even getting into the holiday spirit by offering 50% off tuition courses until the New Year.1
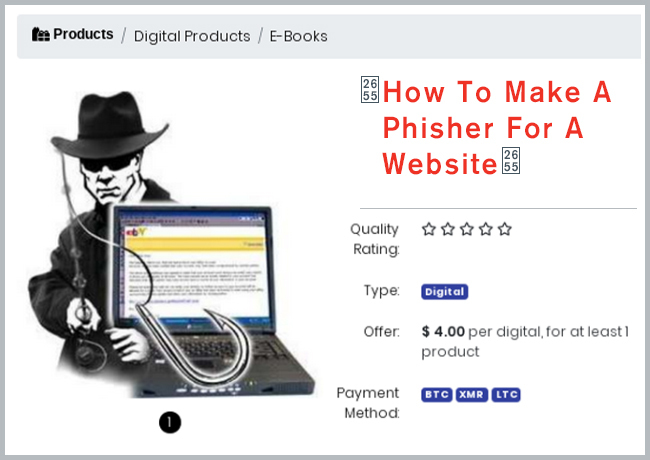
Figure 1: Phishing Tutorial Offered in a Dark Web Market2
Crowd-Sourced Donations and the Internet Fraudster
The rise of popular crowdsourced donation sites (e.g. GoFundme, Fundly, Kickstarter, etc.) may also be another vector of attack for cybercriminals looking to exploit the season’s generosity.
The Federal Trade Commission (FTC) reports that a common scam on such sites is for a fraudster to set up a fake site soliciting donations, sometimes from a real person or group, then pocket the money instead of distributing to the individuals in need.
Atleast one vendor on dark web marketplace DarkBay has advertised cashout guides for such sites. A cashout scheme is a way for criminals to leverage access to a network or infrastructure for financial gain. Access is sometimes, but not always, leveraged through phishing attacks like the ones described above. In this particular advertisement, the vendor vouches that it has been making “US$2000 a day” with this scheme and that it has 100% positive reviews for guides from another popular underground market, Empire, lending legitimacy to this posting.
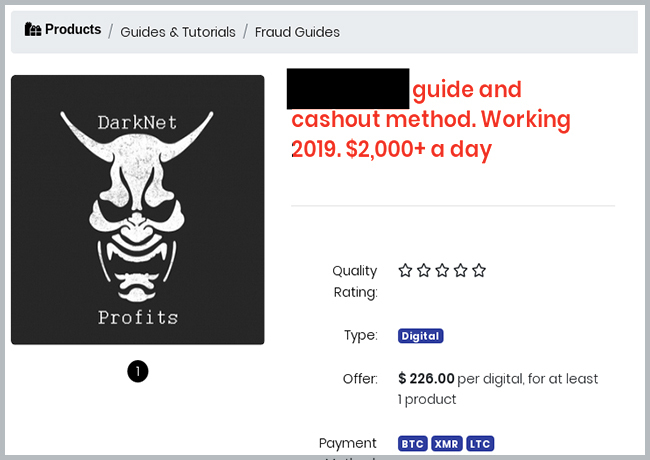
Figure 2: Crowdsourcing Guide and Cashout Method3
In addition, searches for popular crowdsourcing sites bring up hundreds of listings on Genesis Marketplace, a new credential shop offering device fingerprint access to an individual computer. The device fingerprint includes access to all of the saved credentials in an individual’s history, including many popular crowdsourced donation sites where users may save profiles for easy access to donations. Kroll assesses that customers with saved credit card information on such sites may be opening themselves to fraudulent transactions if a threat actor successfully takes over their account. Figure 3 shows a typical listing for a computer access on Genesis Market. This particular listing is for access to a device configuration with a Windows 10 Enterprise Operating System (OS) using Chrome as an internet browser. The sale includes access to the log-in credentials used by the individual owning this device. This particular listing included access to popular crowdsourced funding sites. Genesis Market represents an evolution of the traditional credential shop in giving access to a device fingerprint to help fraudsters defeat automated fraud technology during account take-over attacks.
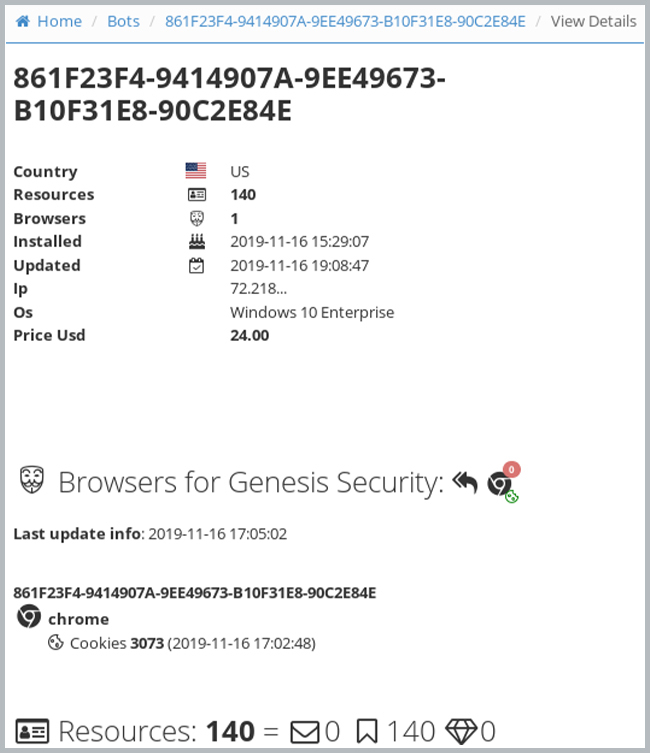
Figure 3: Listing from Genesis Marketplace4
What Can You Do to Avoid Charity Scams?
Awareness and good cyber hygiene are key in avoiding such cyber scams. Best practices include:
- Organizations should conduct regular employee training on how to spot suspicious emails as described in our article on ransomware and the retail sector.
- Individuals should do online research before contributing to a cause. Searching for the name of the cause along with words such as “reviews,” “complaint” or “scam” may shed light on whether the charity in question is legitimate.
- Resources such as the FTC’s consumer site and the CISA site are valuable in vetting charities or providing guidance on how to spot phony websites or suspicious emails.
Scammers may pose a significant threat this holiday season, but research and due diligence can help ensure the money you donate goes to legitimate causes.
Sources
1 Contact Kroll for sourcing details
2 hxxp://bfc3czua5idp5d5y.onion/product/0d89b9d0-ceb8-11e9-8c7a-25e71a003d43/feedback
3 hxxp://darkbayupenqdqvv.onion/product/c41dceb0-cda6-11e9-a36f-f1fd9bd91a39/rules
4 hxxps://genesis.market/client/bots/view?id=140235305&page=4
Stay Ahead with Kroll
Cyber and Data Resilience
Kroll merges elite security and data risk expertise with frontline intelligence from thousands of incident responses and regulatory compliance, financial crime and due diligence engagements to make our clients more cyber- resilient.
24x7 Incident Response
Kroll is the largest global IR provider with experienced responders who can handle the entire security incident lifecycle.
Cyber Risk Assessments
Kroll's cyber risk assessments deliver actionable recommendations to improve security, using industry best practices & the best technology available.
