The Kroll CyberClarity360 team is very excited to share its latest updates to our cutting-edge platform. Recognizing the need for enhanced risk management tools within the third-party cyber risk assessment process, we have added in a “Risk Register” feature. The new features will enable our corporate clients to accurately and rapidly disposition (formally accept a risk, require remediation, etc.) every control across their entire provider portfolio. We have introduced user-customizable Lifecycle Tags to track the progress of providers through the lifecycle, as well as the ability to be date-driven about the next actions for each provider.
See the rest of the sections below for specific training resources on each new feature and capability.
Download the full report by clicking the “Download” button. Please reach out to [email protected] to learn more or get a demo to see how CyberClarity360 can help you reduce your third-party cyber risk.
Risk Register: Capture and Track Risk-Based Decisions
Disposition
At the heart of our Risk Register functionality is our support for an initial risk disposition, which can be found in the new Disposition component part of a Provider’s Results view:
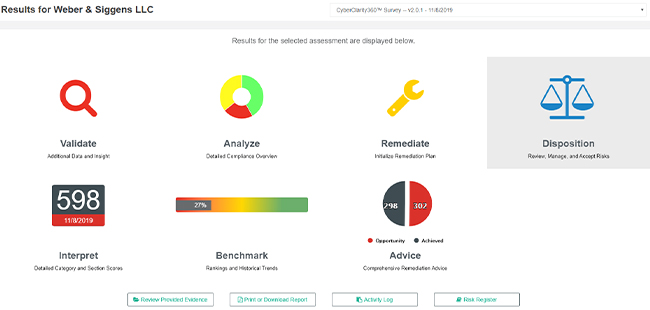
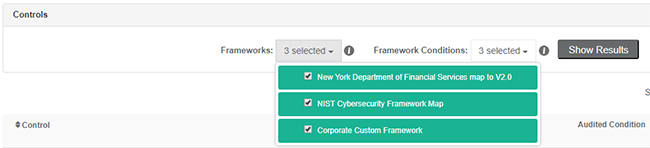
The Disposition view allows users to review all relevant controls for a given provider and supports filtering by the applicable framework:
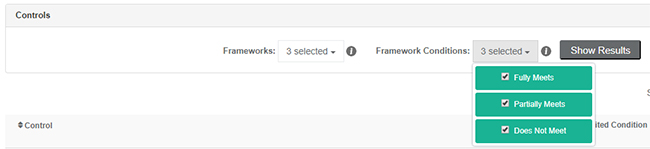
Users are also able to filter by Framework Condition, should they prefer to see a provider’s performance across control sets by a selected condition instead:
Default Dispositions
To accelerate the review process, the CyberClarity360TM platform will automatically populate the Disposition column based on the default Disposition for a given framework condition. Default dispositions are established by CyberClarity360 for common frameworks such as the NIST Cybersecurity Framework or New York Department of Financial Services Cybersecurity Requirements (NYDFS) to provide a suggested course of action for a given risk condition. As part of our enhanced onboarding experience, corporate users will now be given the ability to configure not only custom frameworks and custom framework maps but also custom default dispositions and audited conditions.
Users may adjust the Disposition of any control using a simple dropdown menu:
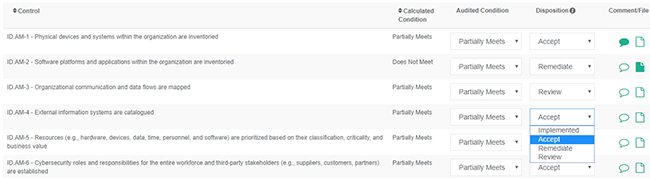
Any comments or files that have been attached to the Control as part of an earlier review process will be carried through to the Disposition screen, and users can review them as part of their Disposition process.
Users are also able to add their own comments or files to each control during the Disposition process.
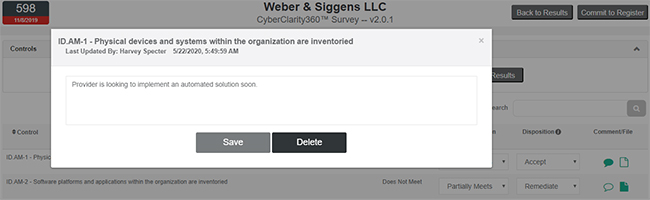
Commit Dispositions
When you are satisfied with the Disposition of each Control for the provider in question, simply click the “Commit to Register” button to finalize your Disposition. This will bring up the Commit Dispositions view, allowing users to apply customizable Lifecycle Tags to the provider, as well as note a date on which to revisit this provider, given their disposition status. See Lifecycle Tags in this document for more details.

In addition to being able to denote which Lifecycle Tags apply to the provider, users may comment at the Disposition level (as opposed to any comments made previously at the Control level) and attach Disposition-level files such as an agreed-upon remediation plan or other collateral.
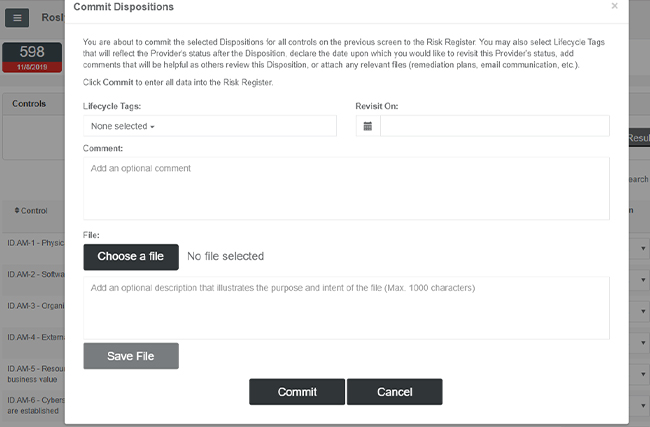
When you are ready to finalize your Disposition, simply click the Commit button, and all the applicable data will be written to your Risk Register for this provider. See the Risk Register section of this document to learn more. You can access the Risk Register in multiple ways. See Navigation Enhancements in this document for details.
Risk Register
Once a set of controls has been dispositioned, this Risk Register entry is made available in the Provider Detail view, under a new Risk Register tab.
You will notice that data from the Risk Register is also available at the Header level for this provider, including any Lifecycle Tags that have been applied; the date upon which the provider’s Disposition should be revisited; and the user who entered the most recent Disposition.
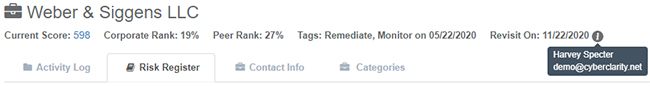
The contents of the Risk Register entry will mirror the Dispostion view in the provider results, including the ability to filter based on a selected Framework or Framework Condition.
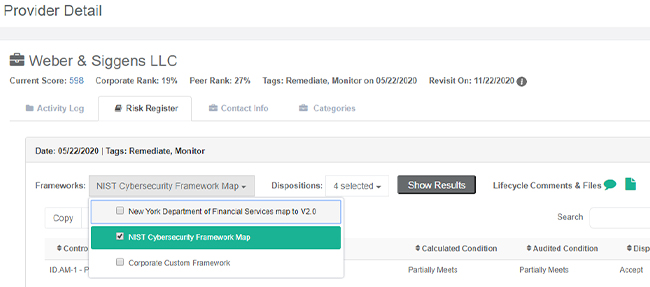
Users may also view Disposition-level comments and files, as well as review multiple Dispositions by simply collapsing the panel. Date of Disposition and applicable Lifecycle Tags remain visible.
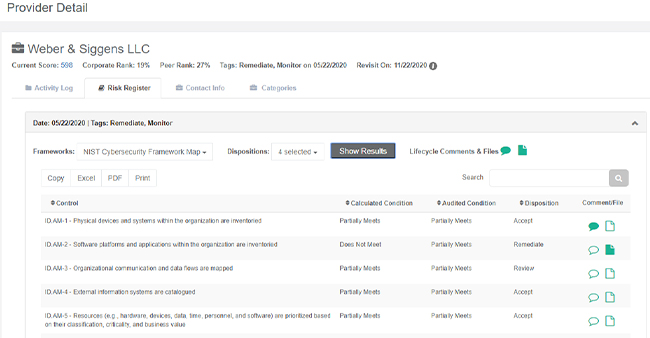
Users can review every content related to a Disposition from a single view, including Control for every available Framework, Calculated Condition, Audited Condition, Disposition and file and comment attached at the Control level.
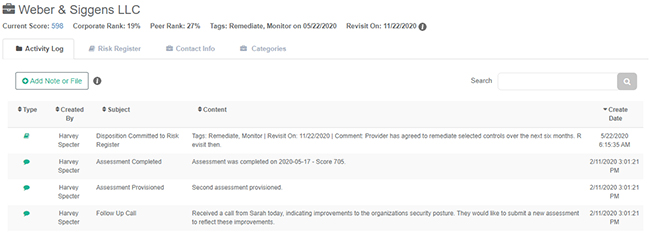
Automatic Activity Log Entries
As part of the Disposition capability, the CyberClarity360 platform will automatically capture the date, time, user, Lifecycle Tags, Revisit On date and comment of a given Disposition, and add it to the Activity Log for the selected provider.
Lifecycle Tags
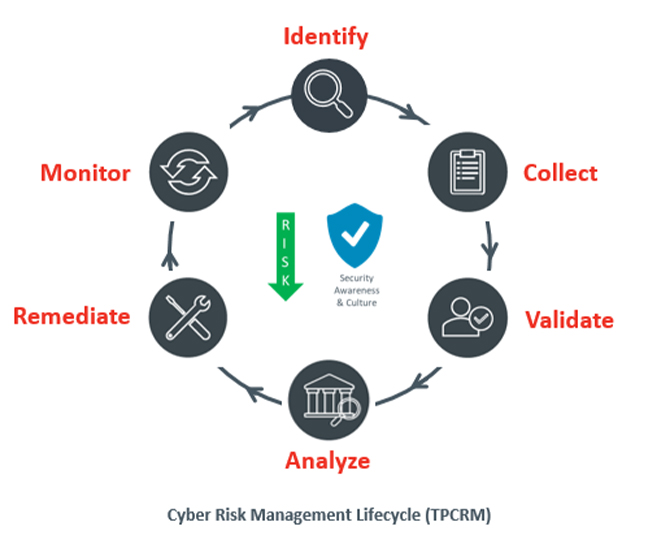
This release introduces the concept of Lifecycle Tags, a feature set that will help CyberClarity360 users continue to align their existing risk management workflows with the functionality of the platform. CyberClarity360 is built on the foundation of the Third-Party Cyber Risk Management (TPCRM) Lifecycle, seen here on the left.
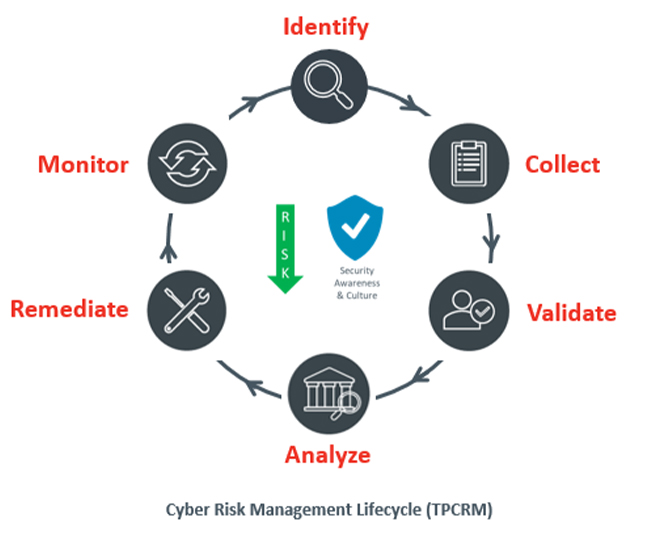
These distinct phases allow the work of risk management to be well-defined and well-structured. New Lifecycle Tags enable this definition to be extended across the CyberClarity360 platform, enabling significantly better alignment with an organization’s larger cyber risk management processes.
Lifecycle Tags are utilized in the Disposition mechanic and are assigned to a given provider when a user chooses to commit dispositions:
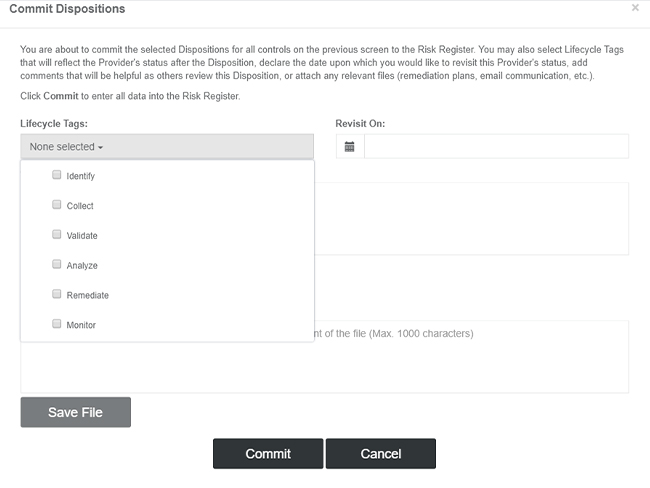
A default set of Lifecycle Tags are included for all users—Identify, Collect, Validate, Analyze, Remediate and Monitor—and may be assigned in any combination, ranging from none to all. Tags can also be added, removed or edited by users. See the next section of this document for details on Lifecycle Tag Management.
Lifecycle Tag Management
Corporate users will now see a new menu in their navigation—Configuration. This menu allows users to manage their configurable data elements, including categories and Lifecycle Tags.
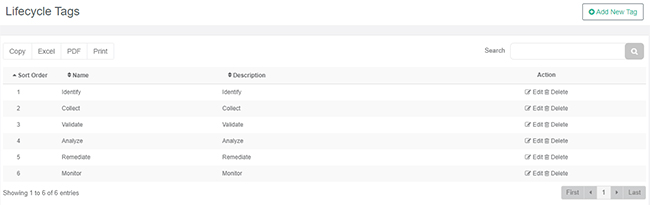
Users who navigate to the Lifecycle Tags option under the Configuration menu can change the Sort Order of the Lifecycle Tags (the order in which they appear in the dropdown menu), or make edits to the Name or Description of a selected tag using the Edit Action:
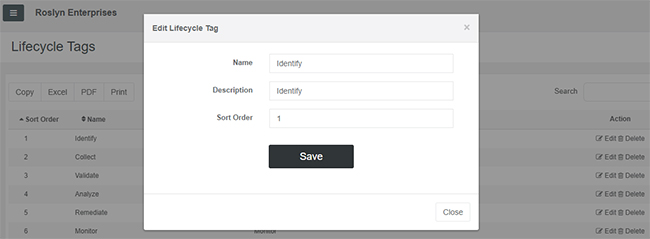
If a Lifecycle Tag is no longer applicable, the Delete Action will make the tag inactive. Wherever a Lifecycle Tag was previously applied, it will remain, it simply won’t be selectable moving forward.
Audited Conditions
In response to user feedback, CyberClarity360 now supports the notion of an Audited Condition for a given Control within a Framework. Previously, the Framework Condition was a static function of the rules related to the given control. While this approach greatly accelerates the analysis and compliance reporting of a given assessment, it does not allow corporate users to capture their own analysis in the platform. With the introduction of Audited Conditions, this is now possible and integrated into the rest of the downstream CyberClarity360 capabilities, including Remediate and Reporting.
Results View: Analyze
In addition to renaming the view previously known as “Compliance” to “Analyze” (learn more about our Results View changes to align with the lifecycle in this section),we have made additional changes to help users better understand the new options available to them in this menu. We have renamed the Level Four view previously known as “Source Details” to “Audit,” as users are now able to provide Audited Conditions with this new feature.
The other levels—Overall, Group and Control—remain in place and function as they previously did.
Audited Conditions
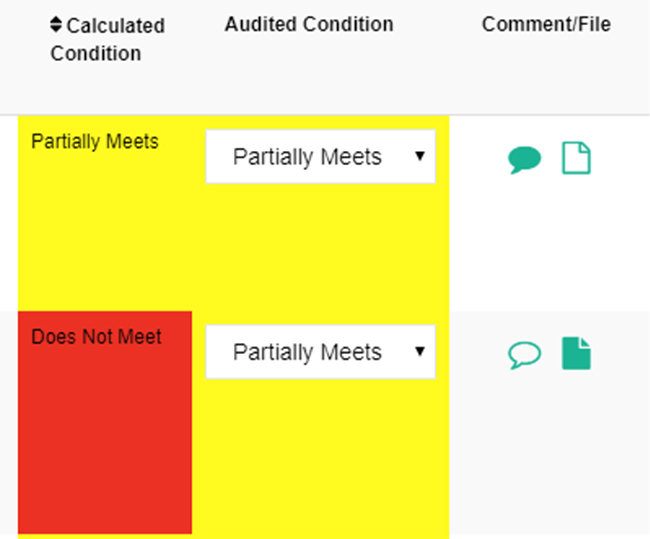
This release introduces the concept of “Audited Conditions,” which stands in contrast to the calculated condition, previously displayed in this component. The Calculated Condition is a result of the CyberClarity360 Framework Engine processing a rule for a given Control, Question and Choice. While these Calculated Conditions are extremely helpful in supporting an analyst’s work within the platform, there are times where changes need to be made given additional context, conversation, inherent risk ratings, etc.
Audited Conditions are conditions that can be modified by a CyberClarity360 corporate user to reflect a desired change in Condition for a given control.
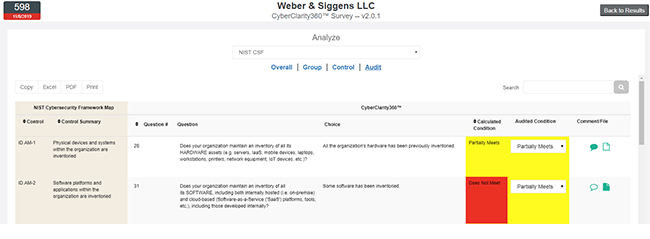
Audited Condition values are automatically seeded for every Framework available to a corporate but are seeded as matching the Calculated Condition value. As a part of our enhanced onboarding experience, corporate users will now be given the ability to configure not only custom Frameworks and custom Framework Maps but also custom default Dispositions and Audited Conditions.
Therefore, unless a corporate user makes a change to an Audited Condition, there will be no functional difference to the previous control mechanics. However, as users make changes to Audited Conditions, we have worked hard to ensure that downstream platform components such as Remediation and Reporting are aware of these changes and take advantage of them in real time.
Files and Comments
Because Audited Conditions represent human input to the system, as opposed to the consistently applied rules of the Framework Engine, we have added the ability for users to append files, comments or both to each control as an opportunity to denote the reasoning behind a change in an Audited Condition. These options are available using the icons to the right of the Audited Condition column and carry through the platform appended to their Control, including the Disposition View and in any Risk Register entries that this Control may appear in.
Rule-Free Controls
An additional element of flexibility is introduced with this release in the Rule-Free Controls capability. Previously, the system was structured such that for a control to appear in the audit view, it required a Rule that the Framework Engine could evaluate. This created conditions where Controls were not included if a Framework Map did not cover mapping to a particular control. Now, with Rule-Free Controls, any Control can be included, even when a mapping does not exist.

Rule-Free Controls will inherit the default condition for the Framework to which they are a part of and allow the user to apply an Audited Condition. This enables users to support the inclusion of Rule-Free Controls in all downstream mechanics that leverage the Audited Condition (including Remediation, Disposition, Reporting, etc.) This also gives significant flexibility to users who are working with complex Control sets or mapped requirements. Now, all controls in a given Framework can be managed by CyberClarity360.
Use of Audited Conditions Across the Platform
As users generate Audited Conditions in the Analyze component, these new conditions are automatically incorporated into downstream functionality to ensure that the most accurate, up to date and applicable data is being utilized.
Remediate
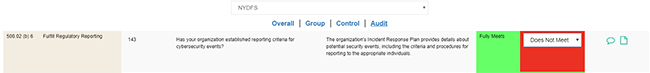
The Remediate functionality will leverage any existing Audited Condition as it generates the Remediation Draft. Even if the Calculated Condition would not have qualified the Control for inclusion in Remediation, an updated Audited Condition that qualifies for Remediation will result in inclusion:

Reporting
The CyberClarity360 platform features an array of reporting modules to help users better understand their risk story. Many of these reports allow users to focus on the status as relates to individual Controls—which will now leverage the Audited Condition values to ensure reporting is as accurate as possible. No user action is required to facilitate this inclusion. Audited Conditions and Calculated Conditions are automatically parsed by the CyberClarity360 platform for reporting inclusion.
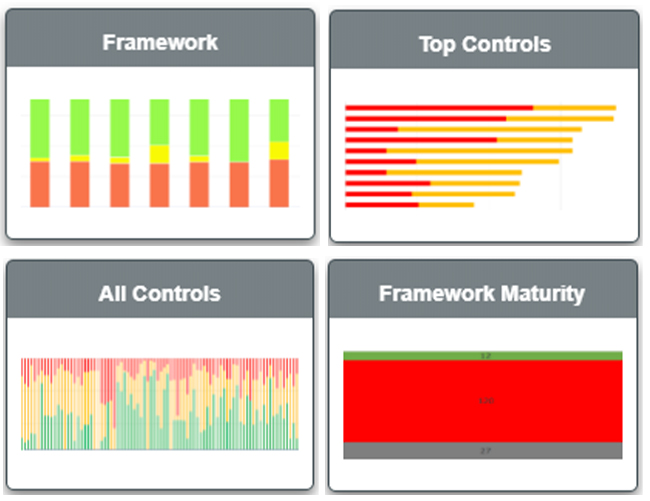
Reports that will now leverage Audited Conditions include Framework, All Controls, Top Controls and Framework Maturity reports.
Usability Updates
This release features several user interface (UI) updates that will enhance usability for CyberClarity360 corporate users.
Results View
The Results View, where corporate users can review the detailed results of a provider’s assessments, has received several changes in this release.
In addition to the inclusion of the new Disposition component, the Validate (formerly Observations), Analyze (formerly Compliance) and Remediate (formerly Remediation Draft) components have all been renamed to better align with the Third-Party Cyber Risk Management Lifecycle. If you are curious about learning more regarding this lifecycle, please download our Legal Vendor Cyber Risk Management Guide.
Additionally, users can now navigate to data elements that are not tied to a specific assessment by utilizing the icons at the bottom of the Results view, including the Activity Log and new Risk Register feature set.

For information on additional navigation enhancements delivered in this release, please see the next section.
Navigation Enhancements
To Risk Register
The Risk Register is homed in the Provider Details menu for a given provider, and is now accessible directly from the “All Providers” table, by selecting the View button in the Risk Register column:
The Risk Register may also be accessed utilizing the new Risk Register tab, available on the Provider Detail menu.
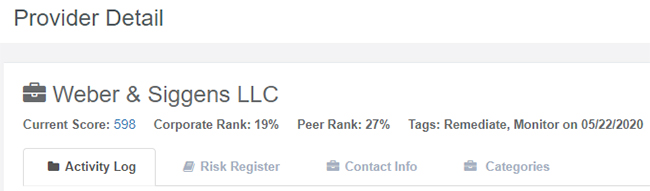
The Risk Register can also be accessed directly from within Activity Log. The new auto-entry feature creates an Activity Log entry for each Disposition entered into the Risk Register—simply click on this entry to be taken to that Disposition within the Risk Register.
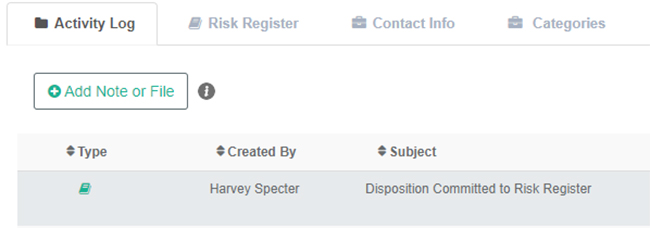
From Risk Register
The Risk Register encompasses a large range of data across multiple assessments and frameworks. That said, CyberClarity360 corporate users are interested in getting the most recent and detailed data to conduct their reviews. As a result, we have simplified the navigation for users to go from within the Risk Register view to the latest results—simply click the CyberClarity360 score under “Current Score” for a provider to be transported directly to the Results View for that assessment.
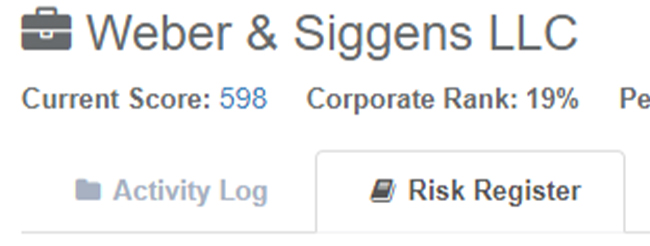
Configuration Menu
With the introduction of user-configurable Lifecycle Tags, along with the pre-existing user-configurable Category Lists, we have introduced a Configuration Menu to the navigation in this release.
This will allow corporate users to quickly and easily reach the elements of their CyberClarity360 platform that are configurable and manage each one directly within their own dedicated menu space.
Stay Ahead with Kroll
Cyber and Data Resilience
Kroll merges elite security and data risk expertise with frontline intelligence from thousands of incident response, regulatory compliance, financial crime and due diligence engagements to make our clients more cyber resilient.
Cyber Risk Assessments
Kroll's cyber risk assessments deliver actionable recommendations to improve security, using industry best practices & the best technology available.
