On July 14, 2021, WooCommerce issued an emergency patch for a critical vulnerability allowing an unauthenticated attacker to access arbitrary data in an online store’s database.
WooCommerce is one of the most popular e-commerce platforms in the world and is installed on over five million websites. Additionally, the WooCommerce Blocks feature plugin, which is installed on more than 200,000 sites, was affected by the vulnerability and was patched at the same time.
The vulnerability affects versions 3.3 to 5.5 of the WooCommerce plugin and WooCommerce Blocks 2.5 to 5.5 plugin. Versions below WooCommerce 3.3 do not appear to be affected.
At the time of writing, there was no CVE assigned to this vulnerability. It is probably because the WooCommerce team has quickly fixed the issue after reporting it. Kroll has not identified any public exploits, although with details now public, we have seen proof-of-concept exploits against vulnerable versions of WooCommerce, and threat actors may now be able to create their own exploits.
If not already done, Kroll advises clients to take the following steps as soon as possible:
- Check if you are using affected software version (versions below WooCommerce 3.3 do not seem to be affected)
- If so, check for signs of compromise such as suspicious queries in server or database logs
- Immediately install patched or the latest software version
- Update the passwords for any Administrator users on all your sites, especially if they reuse the same passwords on multiple websites
- Rotate any payment gateway and WooCommerce API keys used on your sites
WooCommerce advises checking for evidence of the following IP addresses in web access logs, which have been detected exploiting this vulnerability:
- 137.116.119[.]175
- 162.158.78[.]41
- 103.233.135[.]21
According to WooCommerce, over 98% of detected exploit attempts have originated from the first IP address in the list. If these addresses appear in web access logs, assume compromise and move to incident response footing.
Diving Into the Vulnerability
The vulnerability was a time-based Blind SQL Injection, although it appears that UNION-based SQL Injection may be possible with this vulnerability, which would mean that an attacker can more quickly retrieve the database information.
WooCommerce has also published a series of regular expressions that can be used to search for relevant lines in web access log files. These regular expressions will hopefully help locate and analyze potential compromise.
- Requests matching the regular expression: /\/wp-json\/wc\/store\/products\/collection-data.*%25252.*/
- Requests matching the regular expression: /.*\/wc\/store\/products\/collection-data.*%25252.*/ (note that this expression is not efficient/is slow to run in most logging environments)
- Any request to /wp-json/wc/store/products/collection-data or /?rest_route=/wc/store/products/collection-data using POST or PUT methods.
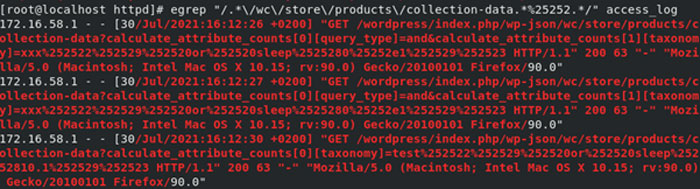
Figure 1 – Test of the vulnerability in the Kroll forensics lab showing the SQL injection queries in server’s logs
Regardless of any perimeter protection system you may have, proactively keeping your CMS software up to date is the best possible protection against today’s web attacks and significantly reduces the risk of vulnerabilities being exploited by threat actors.
It’s important to remember there are many legitimate reasons for a company to keep an unpatched vulnerability in place for business or operational reasons. Maintaining a program that can monitor and understand the impact of new vulnerabilities to determine how soon to patch requires considerable resources beyond what many smaller teams can undertake. A mature cyber security program would balance vulnerability management investments with a stronger ability to detect and respond to incidents, which provides a more robust defensive posture.
Sources
WooCommerce advisory: https://woocommerce.com/posts/critical-vulnerability-detected-july-2021/
WPSEC proof of concept details: https://blog.wpsec.com/woocommerce-unauthenticated-sql-injection-vulnerability-2/
Official updates regarding WooCommerce: https://developer.woocommerce.com/releases/
Stay Ahead with Kroll
Cyber and Data Resilience
Kroll merges elite security and data risk expertise with frontline intelligence from thousands of incident responses and regulatory compliance, financial crime and due diligence engagements to make our clients more cyber- resilient.
Cyber Vulnerability Assessment
Proactively identify vulnerable systems and devices that may be exploited by an attacker or malicious software, often resulting in data loss or breach.
24x7 Incident Response
Kroll is the largest global IR provider with experienced responders who can handle the entire security incident lifecycle.
Cyber Risk Retainer
Kroll delivers more than a typical incident response retainer—secure a true cyber risk retainer with elite digital forensics and incident response capabilities and maximum flexibility for proactive and notification services.
Ransomware Preparedness Assessment
Kroll’s ransomware preparedness assessment helps your organization avoid ransomware attacks by examining 14 crucial security areas and attack vectors.
Data Breach Notification Letters
Kroll will work with your team to implement a personalized, plain-language notification letter that provides pertinent information and maintains message control.