Note: This vulnerability is highly likely to be exploited, and Kroll experts are investigating. If further details are uncovered by our team, updates will be made to the Kroll Cyber Risk blog.
An authentication bypass vulnerability, tracked as CVE-2024-0204, was discovered in Fortra's GoAnywhere MFT versions prior to 7.4.1 and allows an unauthorized user to create an admin user via the administration portal. This vulnerability has a CVSS score of 9.8 with a high potential for exploitation, which we expect to see in the short term due to a proof of concept (PoC) being available. Fortra informed customers on December 4, 2023, of the flaw via an internal forum post. The Kroll Cyber Threat Intelligence (CTI) team was made aware of the flaw after the disclosure of the vulnerability and immediately began investigating. Due to the ease, impact and availability of the exploit code, patches or mitigation actions must be applied immediately.
Analysis
Researchers at Horizon3 have published a POC for this vulnerability, alongside a technical writeup. The flaw resides in a vulnerable endpoint that can be accessed via path traversal ”https://192.168.1.1:8001/goanywhere/images/..;/wizard/InitialAccountSetup.xhtml”; this leads to an administrator account setup form. Combining this and rewriting the form submit request to include the path traversal to the setup endpoint allows an unauthenticated attacker to create an administrator account.
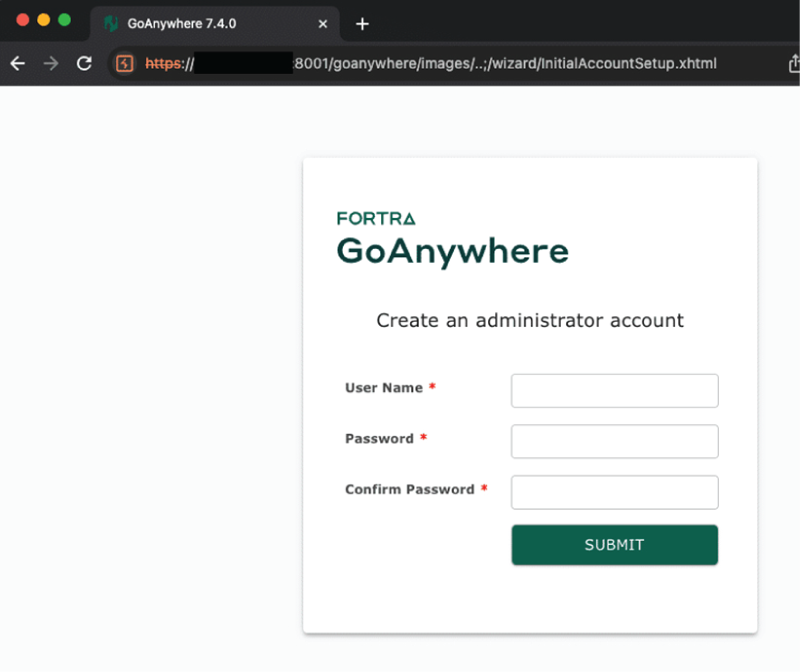
Source: Horizon3.ai
GoAnywhere was the target for many ransomware groups in 2023. Following the discovery of critical zero-day vulnerability CVE-2023-0669, the CL0P ransomware group, who discovered the flaw in the platform, held dozens of organizations to ransom. Once a patch and POC were made public, exploitation by other ransomware families such as LOCKBIT also occurred. The Kroll CTI team estimates that there are over 35,000 GoAnywhere instances available on the internet as of January 24, 2024.
MFT applications make an extremely valuable target for threat actors due to the highly sensitive information that is often shared on those platforms. One of the most impactful MFT exploits was another zero-day exploit discovered by CL0P, which the group used against the MOVEit platform.
Below are recommendations from the Kroll CTI team on addressing CVE-2024-0204:
- Patch Fortra GoAnywhere MFT appliances immediately
- Upgrade to version 7.4.1 or higher
- The vulnerability may also be eliminated in non-container deployments by deleting the InitialAccountSetup.xhtml file in the install directory and restarting the services. For container-deployed instances, replace the file with an empty file and restart.
- For additional information, see https://my.goanywhere.com/webclient/ViewSecurityAdvisories.xhtml (registration required)
Stay Ahead with Kroll
Cyber and Data Resilience
Kroll merges elite security and data risk expertise with frontline intelligence from thousands of incident responses and regulatory compliance, financial crime and due diligence engagements to make our clients more cyber- resilient.
Kroll Responder MDR
Stop cyberattacks. Kroll Responder managed detection and response is fueled by seasoned IR experts and frontline threat intelligence to deliver unrivaled response.
24x7 Incident Response
Kroll is the largest global IR provider with experienced responders who can handle the entire security incident lifecycle.
Incident Response & Recovery
Kroll’s elite security leaders deliver rapid responses for over 3,000 incidents per year and have the resources and expertise to support the entire incident lifecycle, including litigation demands. Gain peace of mind in a crisis.




