
Wed, Apr 29, 2020
Building a Data Inventory � Fundamental Steps
When it comes to leveraging proactive services to protect your organization against the consequences of a cyberattack, data mapping is crucial. Having a proper data inventory has increasingly become a requirement when developing proper cyber security strategies to protect your organization’s data and ensure that it remains secure. In a webinar co-hosted with Snell & Wilmer, Jonathan Fairtlough, Managing Director in the Cyber Risk practice of Kroll discussed key steps organizations can take to bolster their data security to reduce the vulnerabilities that can lead to cyberattacks, such as ransomware and business email compromise (BEC).

Why Build a Data Inventory?
It is vital for security and privacy leaders to take data inventory when deciding where to focus and implement defenses around priority targets. With an inventory, it is easier to identify if certain data has been accessed, or a system as been disabled or affected during a data breach. Knowing what you have and what needs protecting will quicken the process of evaluating any damages to your data from a cyberattack. In addition, not only is data mapping in your organization’s best interest when protecting sensitive information, it is also necessary for compliance efforts. Control frameworks, such as CIS or NIST, are more commonly recommended as data privacy has become increasingly important.
Data Inventory Best Practices
Data mapping involves taking inventory and knowing the full scope of your data. The process of taking data inventory may seem daunting but will ultimately streamline incident response. To efficiently create a thorough data map, it requires asking the right questions, such as:
- Do we know what we have?
- How long are we keeping it?
- Where are we keeping it?
- Why are we keeping it?
- Who has access to it?
- Has the data been classified?
- Who is responsible for the data?
Using the infographic below, Jonathan identifies key considerations when data mapping. He highlights the need to take the proper steps to verify the policies in place to protect your data. This includes steps to verify what you have and how you’re protecting it through various points such as a data classification policy, data loss protection (DLP) tools, data retention policy and data use policy.
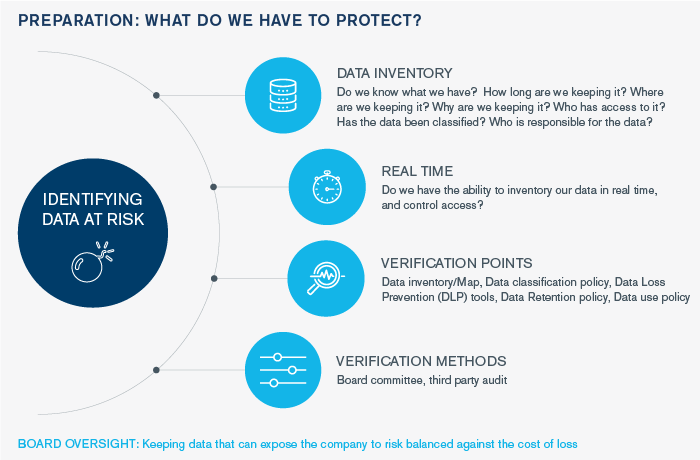
Data mapping is a tedious job, but ultimately provides great clarity and protection that will ensure that your risk management team can make decisions that are properly balanced. Take the extra steps today in mapping your data inventory to protect your organization tomorrow.
Cyber Risk
Incident response, digital forensics, breach notification, managed detection services, penetration testing, cyber assessments and advisory.
Cyber Risk Assessments
Kroll's cyber risk assessments deliver actionable recommendations to improve security, using industry best practices & the best technology available.
Virtual CISO (vCISO) Advisory Services
Kroll’s Virtual CISO (vCISO) services help executives, security and technology teams safeguard information assets while supporting business operations with augmented cyber expertise to reduce business risk, signal commitment to data security and enhance overall security posture.
Data Protection Officer (DPO) Consultancy Services
Kroll's data privacy team provide DPO consultancy services to help you become and stay compliant with regulatory mandates.
Insights
Article List



Threat Intelligence
Developing Your AI Business Strategy: Initial Considerations
April 12, 2024
by Josh Mitchell, Paul Connolly

Forensic Investigations and Intelligence
Foreign Bribery Reform in Australia - a long-awaited reform to Australia’s Foreign Bribery Framework
April 8, 2024
by Cem Ozturk, Gary Gill, Sergio Revilla , Amanda Wood

Cyber
LESLIELOADER – Undocumented Loader Observed
March 13, 2024
by Josh Mitchell, Marc Messer

Cyber
JetBrains TeamCity Vulnerabilities (CVE-2024-27198 and CVE-2024-27199) Exploited
March 11, 2024
by George Glass

