Thu, Jan 10, 2019
Six Best Ways to Protect Your Organization from Insider Cyber Risks
Cyber risk discussions often center around how criminals, nation states, hacktivists and/or terrorists could breach perimeter defenses to carry out objectives such as data theft, denial of service and financial fraud. But what about the trusted employees, contractors and third-party suppliers that already have legitimate access to your systems and data? These are commonly neglected data breach vulnerabilities.
Independent research and years of Kroll’s extensive global fieldwork have shown that trusted insiders can actually pose a greater cyber risk to a business, whether by accidentally or negligently exposing data, or acting with malicious intent. For example, many incidents are traced back to employees carelessly clicking a phishing email link that delivers malicious software or steals credentials, or when they send confidential data to a personal email account “to work from home.” Employees can also be tricked into changing payment details in response to a message received from a compromised email account. We have also encountered cases where proprietary source code was posted to a public repository, likewise when former employees have taken client lists, source code, proposals, etc., to a competitor upon changing jobs.
These examples are just the tip of the iceberg. To reduce insider risk, it is imperative that your internal policies, procedures and controls are as strong as your perimeter defenses. Following are some best practices that organizations of all sizes, in all industry sectors, should establish or strengthen:
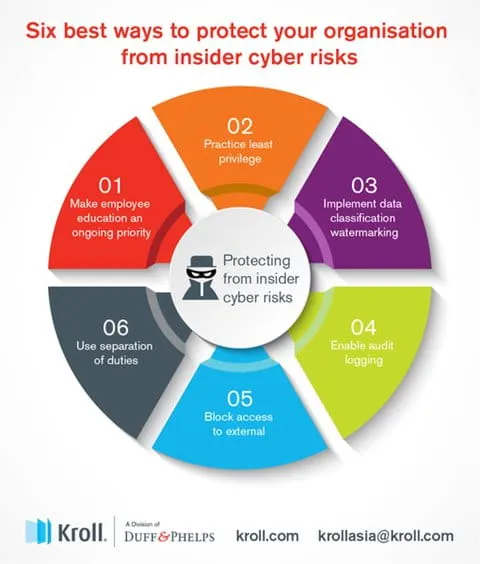
Make employee education an ongoing priority. Teach your employees to have a security-first mindset when it comes to external email communications and handling business-related data. Reinforce this training on a regular basis.
Practice least privilege. Only assign users the access they need to carry out their specific duties. Elevated/privileged accounts should be kept in a software vault solution that requires a change ticket for checkout rather than having users with permanent escalated access 24/7/365.
Implement data classification watermarking (Internal Use Only, Confidential, Sensitive, etc.) and encryption standards for the different data classifications created in your environment. Utilize a data loss prevention (DLP) solution to enforce handling of this watermarked data as well as any personally identifiable information (PII), protected health information (PHI), account numbers, credentials, critical server IP addresses/names, source code, etc.
Enable audit logging wherever possible, especially on any confidential systems or network shares. Regularly review these logs for any abnormalities.
Block access to external email/website domains and universal serial bus (USB) external drives not required for business-related duties.
Use separation of duties, maker-checker or other similar principles to control changes to payment details, critical systems and access management.
If you believe a breach has occurred, immediately contact an experienced breach incident response provider. Time is of the essence in these cases to preserve data in a forensically sound manner and to begin the analysis necessary to understand the full breach scope before critical evidence may be lost.
Cyber Risk
Incident response, digital forensics, breach notification, managed detection services, penetration testing, cyber assessments and advisory.
24x7 Incident Response
Kroll is the largest global IR provider with experienced responders who can handle the entire security incident lifecycle.
