Wed, Dec 11, 2019
After 1,000% Increase in 2018, UK’s Financial Conduct Authority on Track to Receive 900 Cyber Incident Reports in 2019
Based on information released by the UK Financial Conduct Authority (FCA) earlier this year, 2019 looks to enter the record books as a problematic year for financial services firms in terms of reporting material cyber incidents. The numbers are on track to possibly reach nearly 900 cyber incidents for 2019, surging past the 819 incidents reported for 2018, a total that itself was an astronomical 1,000% increase over the mere 69 cyber incidents reported for 2017.
Will 2020 continue this troubling trend? Financial services firms may find pragmatic avenues for mitigating avoidable events in the future by looking at the incidents of the past two years.
From January 1, 2019 to May 27, 2019, financial services firms had reported 370 material cyber incidents to the FCA according to the agency’s response to a May 2019 Freedom of Information Act request. That amounted to 74 incidents per month; if that pace continues through the rest of the year, regulators will have received 888 cyber incident reports by year’s end. Bearing the brunt of those incidents will be retail banks, which reported 208 of those 370 incidents; wholesale financial markets were running a distant second with 55 reported incidents.
While the FCA required mandatory notification prior to GDPR, we expected GDPR implementation would sharpen organizations’ focus and reporting on cyber incidents, which would partially account for the spike of reported incidents for 2018. Along the same lines, looking at the types of incidents reported for the first five months of 2019, what I believe is very telling is the fact that the leading cause of incidents (82 incidents) was still “to be confirmed” at the time of the report, reflecting the difficult and time-consuming nature of cyber incident investigation. As for the leading known root causes reported for cyber incidents, these come as no surprise as they represent the types of challenges that Kroll has seen affecting firms across industry sectors.
The five top known root causes for cyber incidents according to the most recent figures for 2019 (Figure 1) were:
- Third-party failures (79 incidents)
- Hardware/software (64 incidents)
- Change management (53 incidents)
- Cyberattacks (36 incidents)
- Human error (24 incidents)
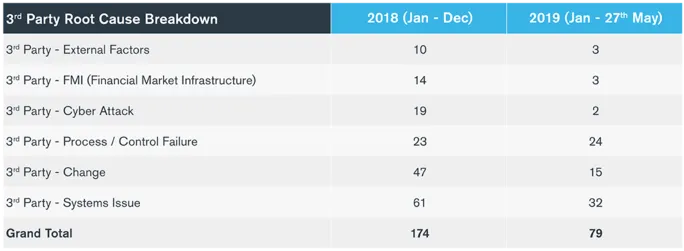
Figure 1 – Root causes and number of cyber incidents reported to FCA for 2018 and for period January 1-May 27, 2019
Third-Party Risks – Persistent and Growing
In 2016 and 2017, only one cyber incident reported to the FCA each year involved third-party failure (Figure 2). That number skyrocketed to 174 in 2018 and could tentatively account for nearly 190 incidents by 2019 year-end. These results dovetail with survey findings recently published in Kroll’s Global Fraud and Risk Report 2019/20. Forty-two percent (42%) of UK respondents – a larger share than in any other country – reported suffering reputational damage due to third-party relationships. Likewise, UK respondents more often hold third parties responsible for incidents generally (25% vs. 19% globally). Overall, survey respondents indicated that cyber breaches played a primary role in nearly half (42%) of incidents involving reputational damage from third-party relationships.
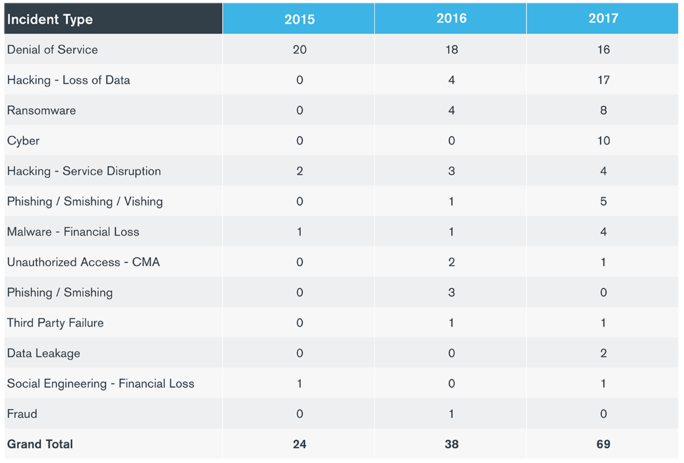
Figure 2 – Root causes and number of cyber incidents reported to FCA, 2015-2017
The risks associated with third-party vendors are amplified when one includes “Nth” parties, described as the third parties of third parties. This expanded universe of third parties likely contributes to the fact that process/control failures, systems issues and change are the top three root causes of third-party failures listed for both last year and the first five months of 2019 (Figure 3).
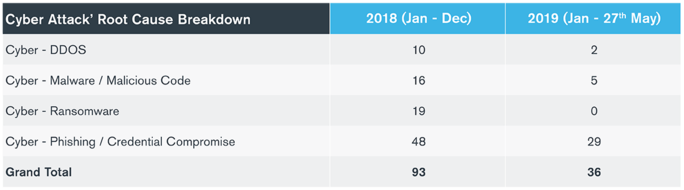
Figure 3 – Root causes of third party cyber incidents reported to FCA for 2015-2017
Phishing and Credential Compromise Leading the Pack in Cyber Threats for Now
The root cause for more than 80% of the Jan-May 2019 cyber incidents reported to the FCA was attributed to phishing/credential compromise (29 incidents). This was the leading cause for cyber incidents in 2018 as well, but the newer numbers are on pace to outstrip last year’s incidents by almost 50%. Globally, losses caused by business email compromise and wire fraud, which are facilitated in large part by successful phishing attacks, exceeded $26 billion for the period June 2016 to July 2019, according to a September 2019 FBI alert. (For more information on BEC trends in 2019, see Kroll’s analysis here.)
However, the fact that not one of the reported incidents was attributed to ransomware (Figure 3) is highly anomalous when viewed from several perspectives:
- A full 20% of 2018’s FCA-reported cyber incidents involved ransomware
- Published reports single out the UK as the “worst hit region” for ransomware in 2019, noting “ransomware is up 195% in the first six months of 2019 compared with the same period a year ago”
- Kroll’s own casework reflected a resurgence of ransomware
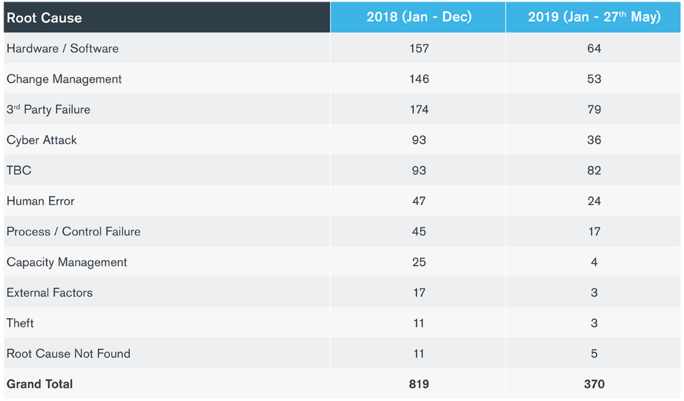
Figure 4 – Root causes of cyberattacks reported to FCA for 2018 and for period January 1-May 27, 2019
Technology-Driven Arms Race Reveals Achilles’ Heel
In Kroll’s Global Fraud and Risk Report, colleagues of mine and I discuss the growing realization among forward-looking organizations that cyber security strategies should not be siloed within a technology white tower. Of course, sophisticated “detect and defend” technology is indispensable for contending with today’s vast amount of data and digital connections. But three of the top five root causes for incidents reported in 2018 and 2019 – hardware/software, change management and human error – provide real-world examples of the problems that can occur when “companies that spend millions of dollars on technology solutions must ensure that they also provide the ongoing resources, policies and procedures needed to make that technology work.”
Our investigative casework is replete with issues that result from avoidable missteps that didn’t account for the human factor, such as misconfigured systems, security features that someone neglected to turn on, changeovers that were not implemented comprehensively, lack of data inventories throughout the enterprise, ineffective “tick-box” cyber security awareness training for staff, etc. Establishing and nurturing a cyber security culture enterprise-wide helps promote collaboration amongst all areas of the business – technology, executive leadership and the board, operations, human resources, compliance, communications, internal audit and legal – that in turn helps close gaps and makes cyber security an integral part of how employees carry out their everyday duties.
Plan Now for a More Positive 2020 Year-End
Firms in the UK financial services sector maintain some of the most sophisticated and robust cyber security environments. This is mainly due to stringent regulatory mandates, customer expectations and their experience as the target of unrelenting attacks by cybercriminals. For all that, the industry might still be reporting 900 cyber incidents by the end of 2019. While a sobering thought, financial services firms should let it be the impetus to test, and if necessary, update incident response plans now, including arrangements with a breach notification partner. From a proactive stance, firms should consider starting 2020 with a fresh slate by conducting vulnerability assessments, penetration testing, tabletop exercises, policies and procedures overview, technology and data inventory, and making the commitment to nurturing cyber security as a culture. Hopefully, by this time next year, rather than wondering what went wrong, firms can celebrate what went right.
Cyber Risk
Incident response, digital forensics, breach notification, managed detection services, penetration testing, cyber assessments and advisory.
Data Protection Officer (DPO) Consultancy Services
Kroll's data privacy team provide DPO consultancy services to help you become and stay compliant with regulatory mandates.
Virtual CISO (vCISO) Advisory Services
Kroll’s Virtual CISO (vCISO) services help executives, security and technology teams safeguard information assets while supporting business operations with augmented cyber expertise to reduce business risk, signal commitment to data security and enhance overall security posture.
Cyber Risk Assessments
Kroll's cyber risk assessments deliver actionable recommendations to improve security, using industry best practices & the best technology available.
