
Thu, May 7, 2020
VPN Vulnerabilities Tied to Rising Data Exposure, Ransomware - The Monitor, Issue 13
Kroll reviewed a wide variety of incident response cases in recent weeks that involved some sort of remote access compromise. With record numbers of employees now working from home, accidental and malicious data exposure incidents are on the rise, many of which are due to vulnerabilities associated with virtual private network (VPN) or remote desktop protocol (RDP) connections.
While VPNs are traditionally more secure than RDP solutions, several VPN providers released significant software patches in the past year, a fact that cybercriminals were quick to seize on. Organizations that haven’t updated their VPN software are now prime targets for ransomware operators and other malicious actors. In a recent Cybersecurity Advisory, the National Security Agency (NSA) urged organizations to check VPN products for upgrades. The advisory warned, “Upgrade your VPN products to the latest vendor-released versions to protect your networks from these attacks. The known vulnerabilities include Pulse Secure™, Palo Alto GlobalProtect™ and Fortinet FortiGate™ VPN products.”
Pulse Secure VPNs are particularly vulnerable due to the critical CVE-2019-11510 alert issued by the company last year for a flaw that allows for remote authentication to a VPN appliance. Pulse Secure’s advisory stated vulnerabilities could “allow an unauthenticated user to perform a remote arbitrary file access on the Personal Communication Service (PCS) gateway … and allow an authenticated administrator to perform remote code execution...”, both of which the advisory further added, “pose significant risk to your deployment.” This advisory was updated in 2020 to reflect new exploitation information and recommendations. Given the fact that there is no workaround, the Cybersecurity and Infrastructure Security Agency (CISA) recommends applying patches provided by the vendor and performing all necessary system updates.
How Do Threat Actors Exploit Vulnerable VPNs?
Actors are mainly identifying potential corporate targets by scanning the internet and then gaining access to user accounts via known exploits. Skip to the “Exploit in Action” section of this newsletter to see a video demonstration. In the past, threat actors most often compromised VPNs through “session hijacking,” after getting their hands on a valid session ID through means such as brute-force attacks or reverse engineering.
Thomas Brittain, Associate Managing Director at Kroll, said that has dramatically changed. He commented, “We’ve been seeing engagements where actors are getting access without session hijacking and that’s due to CVE-2019-115110’s pre-authentication vulnerability that allows unimpeded access. Essentially, actors can query the vulnerable VPN to pull a unique ID for an account, then leverage web browser development tools to manually set a value to the ID, and that allows them unauthenticated access to the VPN administrator console.” From there, it’s generally short work for actors with system access to remotely connect to internal systems. Once on your internal network, they download and execute programs and commands to conduct reconnaissance and harvest passwords enabling them to move laterally in the network and, in many cases, prepare to deploy ransomware.
Watch Thomas Brittain go into further detail about how to recognize signs of Pulse VPN exploits.

See a CVE-2019-115110 Exploit in Action
The video below demonstrates how the vulnerability can be exploited in an unpatched system. Actors remotely scan a system to extract an admin session ID and then bypass the admin login screen by loading the session ID to the browser console, which gives them unauthenticated access to all admin functions. In this example, actors force Windows’s calculator app to load after a VPN user connects to the network, but a real attack would execute more damaging scripts.
In addition to financially motivated actors targeting vulnerable VPNs, advanced persistent threat (APT) groups have also been capitalizing on unsecured VPN infrastructure. Microsoft threat intelligence teams have observed multiple nation-state and cybercrime actors targeting unpatched VPN systems for many months. In October 2019, both the National Security Agency (NSA) and National Cyber Security Centre (NCSC) put out alerts on these attacks and encouraged enterprises to patch. These actors could leverage exploits to target newly created VPN appliances to gain access to intellectual property or other sensitive data on company networks.
VPN Exploits on the Dark Web
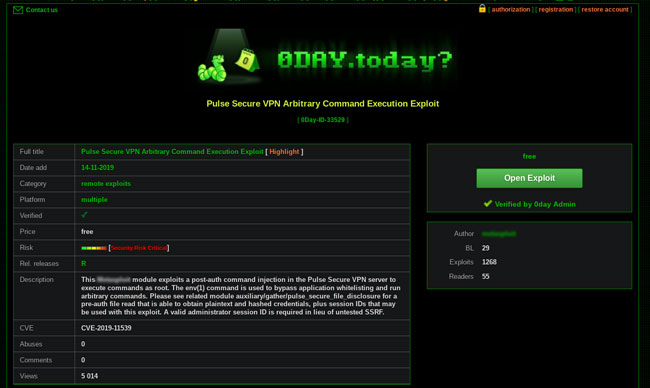
Often the initial challenge in exploring vulnerabilities is finding a way to exploit them, as it involves careful research and may require a rethink of existing attack vectors. Sophisticated exploit scripts can go for thousands of dollars in dark web markets, and some particularly impactful exploit tools are actually considered military weapons. For CVE-2019-11539, however, effective exploits are available on the dark web for free, as you can see below:
Case Studies
Kroll’s recent case studies emphasize the critical need for organizations to know the current status of their VPN infrastructure and apply all patches prior to connecting to the internet.
Sodinokibi ransomware actors entered a client’s system through a vulnerability in Pulse Secure VPN. The actor began deploying the ransomware across all the client’s servers and later sent ransom demands, threatening to publish exfiltrated data.
Actors struck just one to two days after a client added two unpatched VPN appliances to their network. Kroll’s investigation found that prior to a ransomware attack, credentials for the client’s domain administrator and IT director were compromised. Two new domain admin accounts were created by the actors once they gained access to the network. This example demonstrates the importance of patching vulnerable VPN appliances, as quickly as possible.
Watch our video for Remote Work Security Assessment – Safer WFH Environments

Kroll Experts Corner: Best Practices for Securing VPNs
As organizations contend with remote networking challenges, VPN security is imperative. Thomas Brittain has provided several best practices to help prevent the compromise of VPN appliances, related data exposure and ransomware attacks:
Immediate Mitigation Recommendations
- Update and apply all patches and secure configurations of any VPN or other edge/gateway appliance before placing on your network or connecting to the internet
- Enable multifactor authentication (MFA) or two-factor authentication (2FA) for all user accounts leveraging external access over VPN or RDP services; enforce regular password resets that include a complex password policy
- Reset all local VPN accounts, VPN users, administrators and service account credentials before reconnecting upgraded devices to the internet
- Revoke and create new VPN server keys and certificates
- Review your network accounts to ensure adversaries did not create new accounts
Additional Recommendations
- Minimize or eliminate remote access for administrator accounts through VPN or RDP services. Leverage a user account with limited privileges and once logged in to your internal network, switch user accounts.
- Enable logging on all VPN and/or firewall appliances to track all authentication events (successful, failed and unauthenticated), user activity such as RDP connections, file access/downloads and the volume of data (e.g., Cisco’s NetFlow protocol) transmitted and received.
- If possible, send all logs to a Security Information and Event Management (SIEM) system, which can serve as a centralized event and log data collection and analysis point.
- Create a process to review, test and update any edge/internet-connected systems regularly.
Crucial Consideration for the New Normal
Even though some organizations are already planning to return their employees to offices, the move will be gradual; many organizations may prefer to continue remote working indefinitely. VPN configuration remains a crucial step in protecting a remote workforce, and it’s imperative that vulnerabilities like CVE-2019-11539 and CVE-2019-115110 are addressed, along with many others, as part of a robust vulnerability management program. For further guidance, contact a Kroll expert at one of our 24x7 cyber incident response hotlines or our Contact Us page.
The article above was extracted from The Monitor newsletter, a monthly digest of Kroll’s global cyber risk case intake. The Monitor also includes an analysis of the month’s most popular threat types investigated by our cyber experts. Subscription is available below.
Sign up for The Monitor
Email Address
Sign up to receive periodic news, reports, and invitations from Kroll. Our privacy policy describes how your data will be processed.
Cyber Risk
Incident response, digital forensics, breach notification, managed detection services, penetration testing, cyber assessments and advisory.
24x7 Incident Response
Kroll is the largest global IR provider with experienced responders who can handle the entire security incident lifecycle.
Malware and Advanced Persistent Threat Detection
Our expertise allows us to identify and analyze the scope and intent of advanced persistent threats to launch a targeted and effective response.
CyberDetectER
Proactively monitor, detect and respond to threats virtually anywhere – on endpoints and throughout the surface, deep and dark web.
Data Breach Call Center Services
A notification letter can generate lots of questions for those affected by a data breach. Kroll’s call center services are provided by skilled representatives who know how to handle difficult questions and stand at the ready to serve your breached population.


