Thu, Dec 26, 2019
Credentials on Code Repositories: Sharing the Keys to the Kingdom - The Monitor, Issue 10
Cyber threat actors are actively scanning for and finding exposed usernames, passwords and other online credentials in code repositories. Kroll identified two such incidents via its initial intake process for cyber forensics investigations in October 2019. In both cases, cyber threat actors obtained Amazon Web Services (AWS) login credentials and gained unauthorized access to corporate files. Attackers are increasingly scanning public code repositories to find exposed credentials, exploiting these platforms to gain access to a variety of enterprise services and vendors (see “In the News” section).
The Keys to Kingdom Are Exposed
Software developers use cloud-based code repositories like GitHub, Bitbucket and Gitlab to share, edit and update code language with their colleagues. Cyber threat actors are well aware that developers may leave sensitive security access keys within their shared source code repositories. One of the most sought-after keys lies in git-config text files, which can allow access to all the settings or options for a Git repository, including credentials.
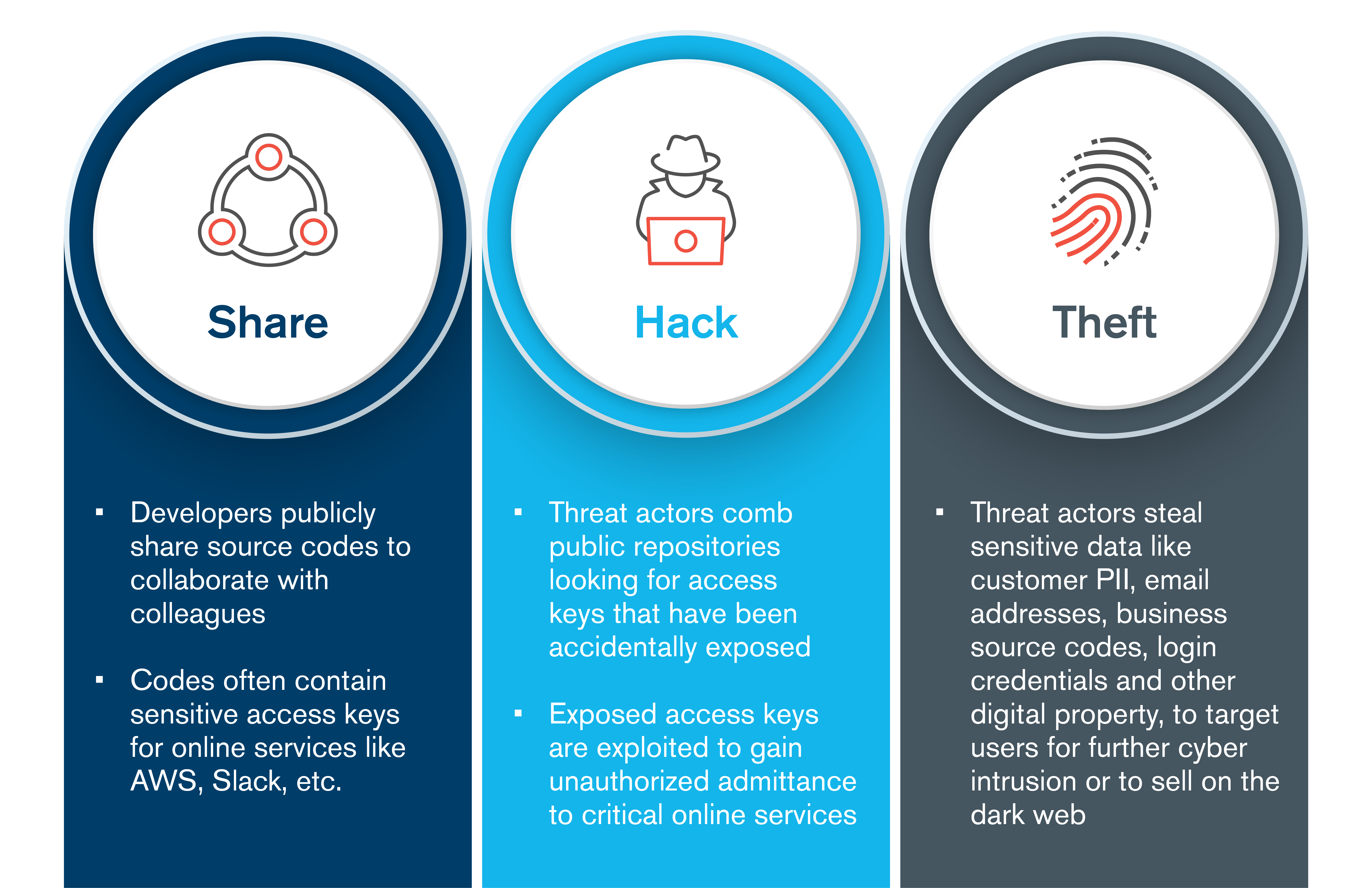
Once threat actors find an exposed git-config file, they can simply copy and clone the accidentally compromised source code. They can then use the exposed credentials to access sensitive data stored in cloud services or credit card processing accounts, which can be a treasure trove of sensitive data, such as personally identifiable information (PII), user IP addresses and financial details. Criminals may also gain full control over the entire code repository, and some malicious actors have even wiped public and private repositories and demanded ransoms to restore data. Hackers have also reportedly capitalized on source code that was inadvertently uploaded to a repository to extort a large conglomerate by threatening to sell their sensitive information on the dark web.
How Extensive is the Leakage in Code Repositories?
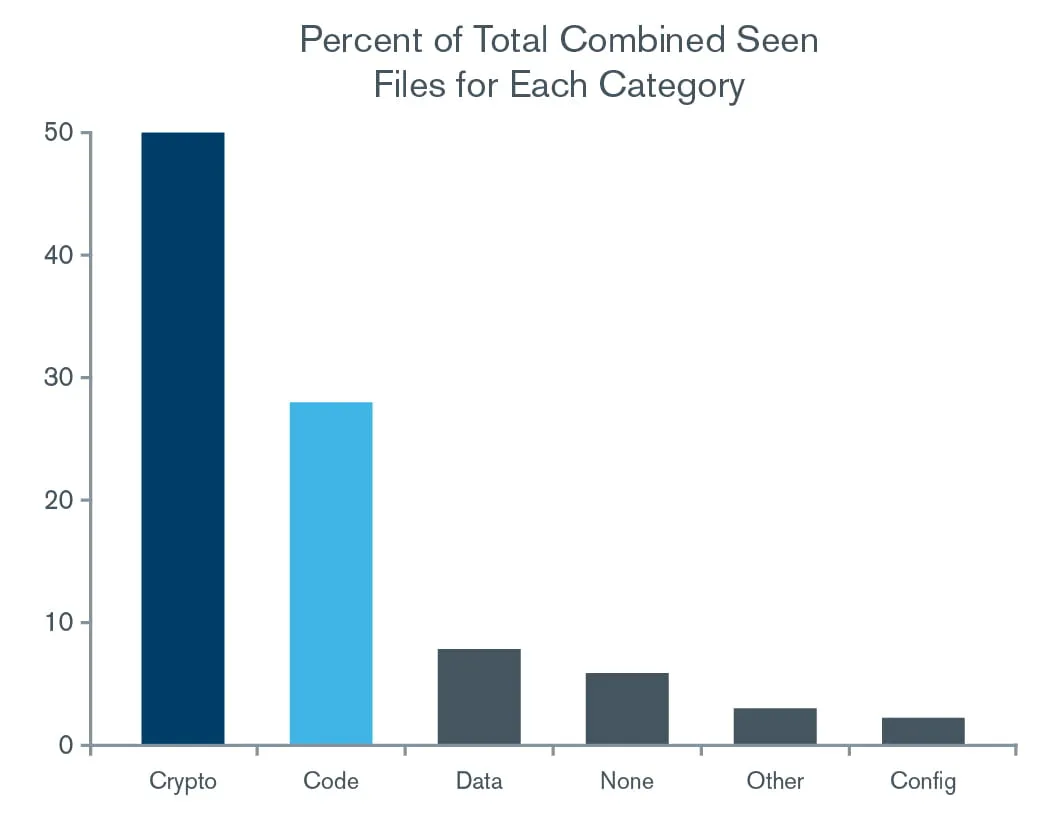
Researchers from North Carolina State University conducted the first large-scale and longitudinal analysis of secret leakage in repositories, examining billions of files over six months and focusing on private keys and some of the highest-impact credential types. Their study uncovered leaks in over 100,000 repositories and identified “thousands of new, unique secrets leaked every day.” The most commonly exposed file types were related to access keys and certificates (categorized as “crypto” in the table below), and source code files.
It’s important to note the most popular cloud-based code repositories are aware of the issue and have strong security features available to minimize exposure risks. These platforms are growing communities of “security advisors” and implementing more visible processes for reporting vulnerabilities, but developers must be security-aware. Training sessions customized for software developers have shown great results, and so has instituting a repository security checklist, such as the one created by author and security researcher Kristov Atlas.
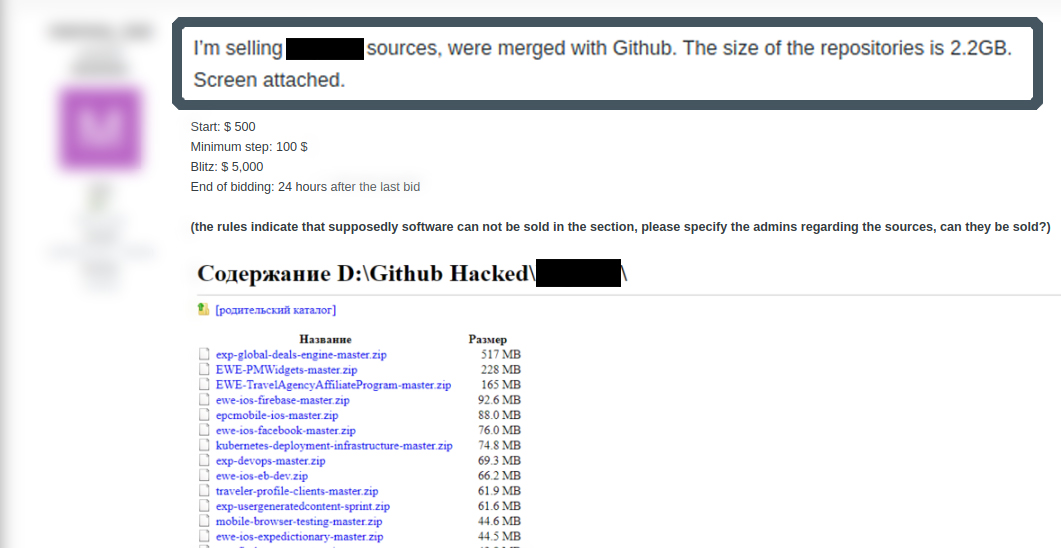
Exposed Digital Property Gained from Repository, Auctioned on the Dark Web
In September 2019, the actor memory_lost posted an auction listing on the Russian language forum Exploit referencing 2.2GB of a large e-commerce company’s source code obtained from an exposed code repository. It appears the repository was subsequently taken down by an unknown user, but the auction indicates memory_lost had already downloaded the code repository before it was taken down.
Kroll Experts Corner: Best Practices for Securing Code Repositories
Strengthening the security mindset of your developers is fundamental to minimize the exposure risk posed by code repositories, but we asked Ray Manna and Justin Price, senior directors in Kroll’s Cyber Risk practice, for additional recommendations to help prevent the compromise of sensitive data and access keys in code repositories:
- Consistently review and remove sensitive data: Develop a plan to periodically review and scan your code, clear sensitive data, invalidate tokens and passwords, and clear any historical records.
- Review code changes: Before any code is merged with the master version, ensure that it is properly reviewed for any malicious content.
- Utilize code scanning tools: Command-line interface tools like Gitrob, Repo Security Scanner and various GitHub Dorks can be great resources as part of the code review process. These tools can help identify sensitive data that has been accidentally exposed in repositories. Some sample Dorks used to scan exposed data include:
- Control access: Access should only be given to those requiring it and should be controlled by multifactor authentication. Never share any accounts and ensure all hardware is secured.
- Back up your code: Make sure you have a good and current backup.
- Security mindset: Develop all projects with a mindset that someone else may access it.
Humans Can Be Your Strongest Defense
A fundamental strategy for mitigating risks associated with cloud-based code repositories is to create and enforce pragmatic policies and controls that guide your internal staff and third-party developers in prioritizing security in development projects. Kroll also offers proactive security configuration hardening for Microsoft Office 365 (O365) and other cloud-based services susceptible to repository-based attacks as well as vulnerability assessment services that include source code review and analysis.
In the News
- Extortionist continues to scan for exposed Git creds – published May 16, 2019, ITNews
- A hacker is demanding ransom for hundreds" of stolen Git code repositories – published May 6, 2019, The Verge
- An exposed password let a hacker access internal Comodo files – published July 27, 2019, TechCrunch
- Report: Scotiabank exposed source code and credentials on GitHub repositories – published September 19, 2019, SC Magazine
- Chinese police arrest hacker who sold data of millions of hotel guests on the dark web – published September 20, 2018, ZDNet
The article above was extracted from The Monitor newsletter, a monthly digest of Kroll’s global cyber risk case intake. The Monitor also includes an analysis of the month’s most popular threat types investigated by our cyber experts. Subscription is available below.
Sign up for The Monitor
Email Address
Cyber Risk
Incident response, digital forensics, breach notification, managed detection services, penetration testing, cyber assessments and advisory.
24x7 Incident Response
Kroll is the largest global IR provider with experienced responders who can handle the entire security incident lifecycle.
Cyber Risk Assessments
Kroll's cyber risk assessments deliver actionable recommendations to improve security, using industry best practices & the best technology available.
Virtual CISO (vCISO) Advisory Services
Kroll’s Virtual CISO (vCISO) services help executives, security and technology teams safeguard information assets while supporting business operations with augmented cyber expertise to reduce business risk, signal commitment to data security and enhance overall security posture.

