
Fri, Nov 27, 2020
2020 Ransomware Attack Trends in Asia Pacific - Beyond the Ransom
Since early 2020, as more of the workforce remained away from the office due to COVID-19, our cyber investigators in APAC have seen a surge in threat actors exploiting remote access vulnerabilities to gain initial access to their victims. While these attacks often ended in a widespread ransomware launch that encrypted a victim’s data and demanded payment for the decryption key, another disturbing trend became increasingly common—data theft prior to encryption.
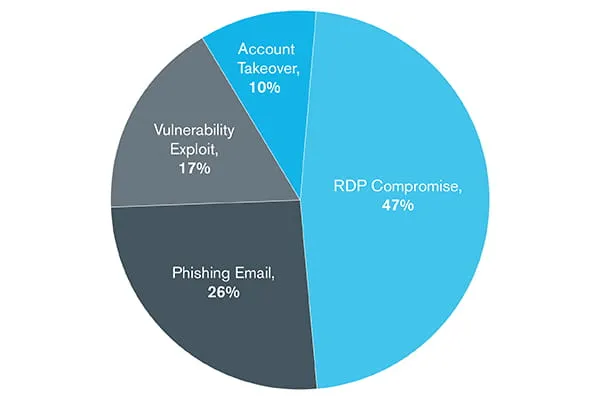
In a recent analysis, ransomware accounted for over one-third of all cases as of September, surpassing email compromises as the topmost threat. The rapid, forced migration to remote work caused by the pandemic opened additional entry points for infection, and our intelligence found that 47% of all ransomware attacks got in through RDP compromises, while another 17% came in from vulnerability exploits such as the ones related to VPN and other remote access solutions.1
What Precedes a Ransomware Event?
Kroll case intake analysis, January 1 – September 1, 2020
Theft Before Encryption
Historically, ransomware had been successful due to the abrupt nature of the attack. It impacts critical systems at a volume level, creates significant risk in time and operational capacity and instills fear and doubt in victims. Since more companies are prepared to defend against ransomware impact with strengthened and verified backup policies and staging of key restoration capabilities, threat actors have changed their tactics. Confidential data is now stolen prior to a ransomware launch, allowing threat actors to extort victims twice. In addition, ransomware groups such as Netwalker, Maze, DoppelPaymer, REvil and Ragnar have moved to publicly shaming “non-compliant” victims and exposing stolen data in phases to further force payment. Kroll has actively investigated incidents attributed to Netwalker and Maze in APAC, but it should be noted that Maze announced they ended operations after November 1.
Due to this trend, companies must shift from seeing ransomware as just a business disruption that can be remedied through backups to treating the incident as a potential data breach that can carry increasingly high fines. Few examples below:
- The Singapore Parliament proposed amendments to the Personal Data Protection Act (PDPA) to increase the maximum data breach fine to 10% of a company’s annual turnover or SGD 1 million, whichever is higher.
- Indonesia’s proposed data protection law includes fines of up to SGD 20 million.
- Japan has also proposed increased data breach penalties close to USD 1 million (100 million Yen).
Victims must consider regulatory reporting, client/customer notifications and reputational risk. Furthermore, an incident is not just a matter of restoration, it needs to be thoroughly investigated by professionals to determine the full impact and ensure total containment and remediation.
To Pay or Not to Pay
Paying a ransom is ultimately a business risk decision. Common questions often include: Can business operations continue without that data? Is it detrimental if stolen data is leaked? Will this encourage the threat actors if payment is made?
If you are considering engaging with the threat actor, seek legal advice and utilize professionals who can assist with providing threat actor intelligence, obtaining a proof of life sample, reducing payment amount, ensuring legal compliance if a payment is made, and completing the payment as an independent third -party.
Preparedness is Key
Here are some simple steps companies can take to ensure they are prepared for an incident:
- Run regular backups, secure the backups and test them regularly
- Know where your sensitive data is stored and implement controls to limit access
- Restrict remote access to Virtual Private Network (VPN) users further secured by multi-factor authentication (MFA)
- Segment internal networks to prevent free movement once inside
- Regularly update patches on all endpoints
- Deploy network and endpoint monitoring throughout the enterprise
- Plan for an attack, have proper incident response policies and procedure in place, organize internal and external teams that can be rapidly engaged to respond and hold regular exercises to test these plans
- Have a partner or process in place should regulations mandate notification procedures
Engaging an end-to-end cyber risk management expert with capabilities ranging from proactive services such as risk assessment tests to incident response services and investigations, companies will be able to leverage on the full suite of services to check breach readiness and close potential gaps.
In an interview with Ausbiz TV, Kroll's Louisa Vogelenzang discusses the rise in ransomware attacks. Watch the video here:

Cyber Risk
Incident response, digital forensics, breach notification, managed detection services, penetration testing, cyber assessments and advisory.
Ransomware Preparedness Assessment
Kroll’s ransomware preparedness assessment helps your organization avoid ransomware attacks by examining 14 crucial security areas and attack vectors.
24x7 Incident Response
Kroll is the largest global IR provider with experienced responders who can handle the entire security incident lifecycle.
Kroll Responder
Stop cyberattacks. Kroll Responder managed detection and response is fueled by seasoned IR experts and frontline threat intelligence to deliver unrivaled response.
Notification, Call Centers and Monitoring
Kroll’s data breach notification, call centers and monitoring team brings global breach response expertise to efficiently manage regulatory and reputational needs.
Virtual CISO (vCISO) Advisory Services
Kroll’s Virtual CISO (vCISO) services help executives, security and technology teams safeguard information assets while supporting business operations with augmented cyber expertise to reduce business risk, signal commitment to data security and enhance overall security posture.
Cyber Risk Retainer
Kroll delivers more than a typical incident response retainer—secure a true cyber risk retainer with elite digital forensics and incident response capabilities and maximum flexibility for proactive and notification services.
