Fri, Mar 1, 2019
Ryuk and the Resurgence of Ransomware - The Monitor, Issue 2
The article below was extracted from The Monitor newsletter, a monthly digest of Kroll’s global cyber risk case intake. The Monitor also includes an analysis of the month’s most popular threat types investigated by our cyber experts. Subscription is available below:
Kroll identified 15 ransomware cases via its cyber intake process during the month of February 2019. In particular, we noted the highly opportunistic Ryuk variant seizing on vulnerable networks, with attacks across industry sectors, including manufacturing, government, education, professional services and healthcare.
Kroll reviewed Ryuk ransom notes that directed victims to contact a Swiss-based ProtonMail email address. Then the attackers followed up with varying demands for payment in bitcoin. Based on our experience and other reports, most Ryuk ransomware attacks follow this pattern.
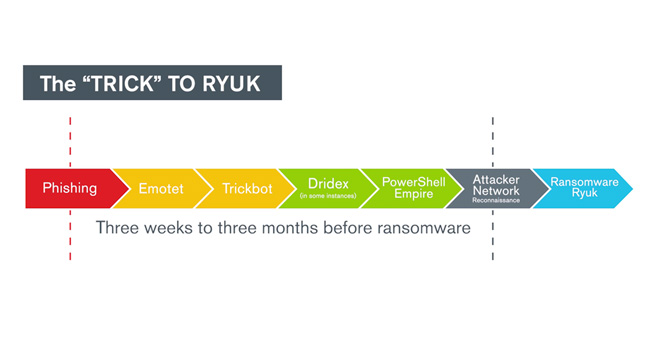
However, Ryuk mainly differs from other ransomware families based on its delivery mechanism. Most types of ransomware rely on phishing attacks or open Remote Desktop Protocol (RDP) connections. Ryuk most often leverages established command and control servers associated with Trickbot and Emotet banking trojans. This allows the Ryuk attackers to access a large swath of victims and “cash in” on high-value Trickbot and Emotet victims; they then tailor ransom demands to each organization. (See the Technically Speaking section in this newsletter for a representative attack sequence.)
While Ryuk attackers profit from their ties with these trojans, the connection also provides a tripwire that can alert victims to a potential ransomware attack following a trojan infection. “Ransomware in 2019 is significantly different than ransomware in 2017, with attackers leveraging the access gained with Trickbot and Emotet, which usually includes domain administrator access. Attackers now spend far more time performing reconnaissance on an impacted network, which allows them to have a high level of confidence that an organization will have to pay the ransom. We have identified attackers deleting backups to make recovery increasingly difficult,” says Associate Managing Director Pierson Clair.
Pierson continues, “Most trojans are introduced via methods such as social engineering attacks, specifically infected email attachments. Emotet and Trickbot are families of polymorphic malware, which makes them very difficult for anti-virus to identify. However, we know these attack vectors can be addressed effectively with several other proven measures. These range from human-focused efforts, such as educating employees and making social engineering exercises part of broader technical penetration testing programs, to implementing layers of technological solutions, including threat intelligence and endpoint detection and response applications. So, organizations can virtually head off Ryuk at the pass by implementing best practices that prevent Trickbot/Emotet from getting a foothold in the first place.”
Technically Speaking
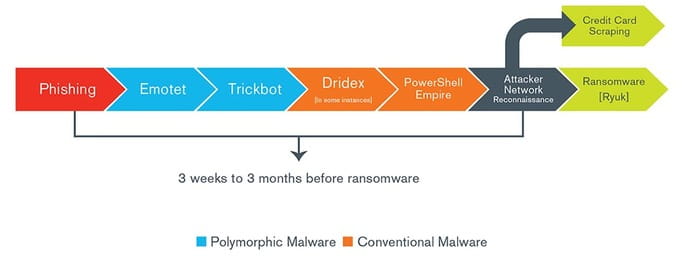
Following is a typical sequence of events that Kroll’s investigations have identified in the evolution of Emotet/Trickbot/Ryuk attack.
According to an FBI Flash, the Ryuk ransomware variant is marked by these characteristics:
- First appeared as a derivative of Hermes 2.1 ransomware and became available on the open market as of August 2018
- Retains some aspects of Hermes code; all of Ryuk’s files contain the “HERMES” tag, but some of the files have .ryk added to the filename, while others do not.
- In other parts of the ransomware code, Ryuk has removed or replaced features of its predecessor.
- Ryuk deletes all files related to the dropper used to deploy the malware
- Ryuk has been deployed secondary to Trickbot and/or Emotet banking Trojans, which use Server Message Block (SMB) protocols to propagate through the network and can be used to steal credentials.
- After the initial attack, additional network exploitation tools may be downloaded, including PowerShell Empire, the Microsoft Sysinternals tool psexec, or the penetration testing tool Cobalt Strike.
- Once executed, Ryuk establishes persistence in the registry, injects into running processes, looks for network connected file systems, and begins encrypting files.
- Ryuk utilizes AES-256 to encrypt files and uses an RSA public key to encrypt the AES key.
- The Ryuk dropper drops a .bat file which tries to delete all backup files and Volume Shadow Copies (automatic backup snapshots made by Windows), preventing the victim from recovering encrypted files without the decryption program.
Watch Associate Managing Director Thomas Brittain go into further detail about the Ryuk ransomware timeline.

Kroll Experts Corner – Mitigating Ransomware
Following are some insights from Kroll experts on how to prevent or mitigate the harms from a ransomware attack, including the Ryuk variant.
- Backups, Backups, Backups
If ransomware does strike, and backups are valid and intact, then recovery is significantly easier. However, Managing Director Devon Ackerman cautions that organizations might be operating under a false sense of security in their backups. “While many organizations have robust processes for creating backups, a similar rigor often doesn’t extend to validating the security controls around the backups. For example, is the backup on an open network? Could a breached domain admin credential access the backup? These issues and more all leave open the possibility that an attacker could destroy the backup repository.” - Conduct Routine Security Risk Assessments, Including Vulnerability and Penetration Testing
Preventing trojans from entering and taking hold in your organization will go a long way toward neutralizing the Ryuk ransomware threat. Addressing fundamental cyber risks through expert assessments and targeted testing can help prevent your organization from being victimized twice. Tabletop exercises can also be instructive; practice incident response scenarios that include complex attacks combining disruption through ransomware, DDoS, network downtime, etc. - Implement Endpoint Monitoring, Detection and Response
Solutions such as Kroll’s CyberDetectER® Endpoint prevent the spread of the attack by halting the execution of the code that launches the encryption processes before it damages and cripples systems. - Use a Firewall to Prevent All Public Access to the Service Message Block (SMB/port 445) and the Remote Desktop Protocol (RDP/port 3389)
Remote access should be restricted to a dedicated server that requires multi-factor authentication (MFA), which ensures sufficient privilege access restriction and logging capability. - Configure File Integrity Monitoring
File integrity monitoring should also be configured to monitor file creations in trusted locations, like the System32 directory. This can also be used to monitor deletes, with an alert configured to fire on excessive deletes in a row.
The article above was extracted from The Monitor newsletter, a monthly digest of Kroll’s global cyber risk case intake. The Monitor also includes an analysis of the month’s most popular threat types investigated by our cyber experts. Subscription is available below.
Cyber Risk
Incident response, digital forensics, breach notification, managed detection services, penetration testing, cyber assessments and advisory.
24x7 Incident Response
Kroll is the largest global IR provider with experienced responders who can handle the entire security incident lifecycle.
CyberDetectER
Proactively monitor, detect and respond to threats virtually anywhere – on endpoints and throughout the surface, deep and dark web.


